Shielding against Web Application Attacks - Detection Techniques and Classification
Main Article Content
Abstract
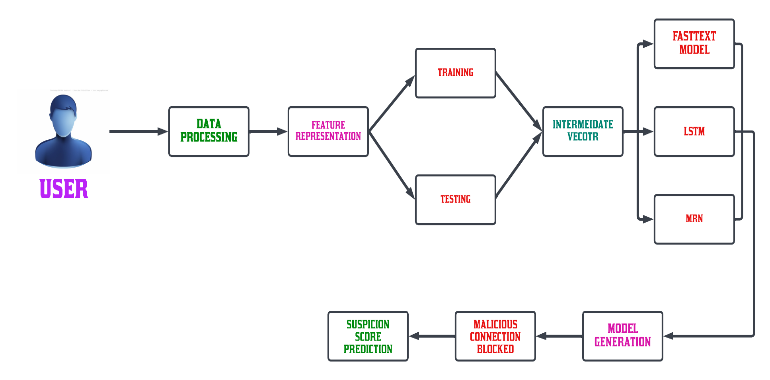
The field of IoT web applications is facing a range of security risks and system attacks due to the increasing complexity and size of home automation datasets. One of the primary concerns is the identification of Distributed Denial of Service (DDoS) attacks in home automation systems. Attackers can easily access various IoT web application assets by entering a home automation dataset or clicking a link, making them vulnerable to different types of web attacks. To address these challenges, the cloud has introduced the Edge of Things paradigm, which uses multiple concurrent deep models to enhance system stability and enable easy data revelation updates. Therefore, identifying malicious attacks is crucial for improving the reliability and security of IoT web applications. This paper uses a Machine Learning algorithm that can accurately identify web attacks using unique keywords. Smart home devices are classified into four classes based on their traffic predictability levels, and a neural system recognition model is proposed to classify these attacks with a high degree of accuracy, outperforming other classification models. The application of deep learning in identifying and classifying attacks has significant theoretical and scientific value for web security investigations. It also provides innovative ideas for intelligent security detection by classifying web visitors, making it possible to identify and prevent potential security threats.
Article Details
References
M. Lin, C. Chiu, Y. Lee, and H. Pao, “Malicious URL filtering—A big data application,” in Proc. IEEE Int. Conf. Big Data, 2013, pp. 589–596.
D. Kar, S. Panigrahi, and S. Sundararajan, “SQLiDDS: SQL injection detection using query transformation and document similarity,” in Proc. Int. Conf. Distrib. Comput. Internet Technol., 2015, pp. 377–390.
A. Le, A. Markopoulou, and M. Faloutsos, “PhishDef: URL names say it all,” in Proc. IEEE INFOCOM, 2011, pp. 191–195.
Revathy, S. ., & Priya, S. S. . (2023). Enhancing the Efficiency of Attack Detection System Using Feature Selection and Feature Discretization Methods. International Journal on Recent and Innovation Trends in Computing and Communication, 11(4s), 156–160. https://doi.org/10.17762/ijritcc.v11i4s.6322
P. Bisht, P. Madhusudan, and V. N. Venkatakrishnan, “Dynamic candidate evaluations for automatic prevention of SQL injection attacks,” ACM Trans. Inf. Syst. Secure., vol. 13, no. 2, pp. 398–404, 2010.
C. Luo, S. Su, and Y. Sun, “A convolution-based system for malicious URL requests detection,” Comput. Mater. Continua, vol. 61, no. 3, pp. 399–411, 2019.
M. Li, Y. Sun, H. Lu, S. Maharjan, and Z. Tian, “Deep reinforcement learning for partially observable data poisoning attack in crowdsensing systems,” IEEE Internet Things J., vol. 7, no. 7, pp. 6266–6278, Jul. 2020.
Y. H. Hwang, “IoT security & privacy: Threats and challenges,” in Proc. 1st Acm Workshop on IoT Privacy Trust and Security, 2015, p. 1.
A. Jamdagni, Z. Tan, and X. He, “RePIDS: A multi-tier real-time payload-based intrusion detection system,” Comput. Netw., vol. 57, no. 3, pp. 811–824, 2013.
Z. Tan, A. Jamdagni, X. He, P. Nanda, and R. P. Liu, “A system for denial-of-service attack detection based on multivariate correlation analysis,” IEEE Trans. Parallel Distrib. Syst., vol. 25, no. 2, pp. 447–456, Feb. 2014.
Derya erhan (Member, IEEE), and Emin anari, “Hybrid DDoS Detection Framework Using Matching Pursuit Algorithm,” Comput. Secure., vol. 60, pp. 206–225, 2020.
Zhihong Tian, Chaochao Luo, Jing Qiu, Xiaojiang Du, Mohsen Guizani, “A Distributed Deep Learning System for Web Attack Detection on Edge Devices,” 2020, arXiv:1702.08568.
Rashidah F. Olanrewaju, Burhan Ul Islam Khan, Malik Arman Morshidi, Farhat Anwar, and Miss Laiha Binti Mat Kiah, “A Frictionless and Secure User Authentication in Web-Based Premium Applications.,” in Proc. IEEE 14th Int. Colloq. Signal Process. Its Appl., 2021, pp. 103–106.
Jothi K R, Saravana Balaji B, Nishant Pandey, Pradyumn Beriwal, Abhinandan Amarajan “An Efficient SQL Injection Detection System Using Deep Learning,” in Proc. VI Int. Conf. Netw., Commun. Comput., 2021, pp. 80–85.
Wen-Bin Hsieh, Jenq-Shiou Leu, and Jun-Ichi Takada, “Use Chains to Block DNS Attacks: A Trusty Blockchain-based Domain Name System.”, vol. 7, no. 6, pp. 4682–4696, Jun. 2020.
J. Ma, L. K. Saul, and S. Savage, “Beyond blacklists: Learning to detect malicious websites from suspicious URLs,” in Proc. ACM SIGKDD Int. Conf. Knowl. Discovery Data Mining, 2009, pp. 1245–1254.
Hariharan, B., Sathya Priya, S., “Recent Web Application Attacks’ Impacts, and Detection Techniques–A Detailed Survey” Lecture notes in Networks and Systems 2023, 673 LNNS, pp. 863–871
F. Yong, P. Jiayi, L. Liang, and H. Cheng, “WOVSQLI: Detection of SQL injection behaviors using word vector and LSTM,” in Proc. 2nd Int. Conf. Cryptography, Secure. Privacy, 2018, pp. 170–174.
B. Martin, M. Brown, A. Paller and D. Kirby, "CWE/SANS top 25 most dangerous software errors," The MITRE Corporation, 2011. Michele Bugliesi, Stefano Calzavara, Riccardo Focardi, Formal methods for web security, Journal of Logical and Algebraic Methods in Programming, Volume 87, 2017, Pages 110-126.
Michele Bugliesi, Stefano Calzavara, Riccardo Focardi, “Formal methods for web security,” Journal of Logical and Algebraic Methods in Programming, Volume 87, 2017, Pages 110-126.
M. K. Gupta, M. C. Govil and G. Singh, "Static analysis approaches to detect SQL injection and cross-site scripting vulnerabilities in web applications: A survey," International Conference on Recent Advances and Innovations in Engineering (ICRAIE-2014), Jaipur, 2014, pp. 1-5.
N. Antunes and M. Vieira, "Detecting SQL Injection Vulnerabilities in Web Services," 2009 Fourth Latin-American Symposium on Dependable Computing, Joao Pessoa, 2009, pp. 17-24.
Z. Ghanbari, Y. Rahmani, H. Ghaffarian and M. H. Ahmadzadegan, "Comparative approach to web application firewalls," 2015 2nd International Conference on Knowledge-Based Engineering and Innovation (KBEI), Tehran, 2015, pp. 808-812.
A. Alzahrani, A. Alqazzaz, Y. Zhu, H. Fu, and N. Almashfi, "Web Application Security Tools Analysis," 2017 IEEE 3rd International Conference on Big Data Security on Cloud (Big Data Security), IEEE International Conference on High Performance and Smart Computing (hpsc), and IEEE international conference on intelligent data and security (ids), Beijing, 2017, pp. 237-242.
J. Han and M. Kamber, Data Mining: Concepts and Techniques. Morgan Kaufman, 2001.
J. Qiu, L. Du, D. Zhang, S. Su, and Z. Tian, “Nei-TTE: Intelligent traffic time estimation based on fine-grained time derivation of road segments for smart city,” IEEE Trans. Ind. Informat., vol. 16, no. 4, pp. 2659–2666, Apr. 2020.
I. Lee, S. Jeong, and S. Yeo, “A novel method for SQL injection attack detection based on removing SQL query attribute values,” Math. Comput. Modelling, vol. 55, no. 1-2, pp. 58–68, 2012.