Two-Factor Biometric Identity Verification System for the Human-Machine System Integrated Deep Learning Model
Main Article Content
Abstract
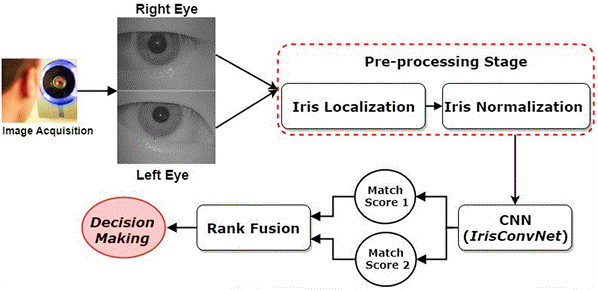
The Human-Machine Identity Verification System based on Deep Learning offers a robust and automated approach to identity verification, leveraging the power of deep learning algorithms to enhance accuracy and security. This paper focused on the biometric-based authentical scheme with Biometric Recognition for the Huma-Machinary Identification System. The proposed model is stated as the Two-Factor Biometric Authentication Deep Learning (TBAuthDL). The proposed TBAuthDL model uses the iris and fingerprint biometric data for authentication. TBAuthDL uses the Weighted Hashing Cryptographic (WHC) model for the data security. The TBAuthDL model computes the hashing factors and biometric details of the person with WHC and updates to the TBAuthDL. Upon the verification of the details of the assessment is verified in the Human-Machinary identity. The simulation analysis of TBAuthDL model achieves a higher accuracy of 99% with a minimal error rate of 1% which is significantly higher than the existing techniques. The performance also minimizes the computation and processing time with reduced complexity.
Article Details
References
Jain, A. K., Ross, A., & Prabhakar, S. (2004). An introduction to biometric recognition. IEEE Transactions on Circuits and Systems for Video Technology, 14(1), 4-20.
Ratha, N. K., Connell, J. H., & Bolle, R. M. (2001). Enhancing security and privacy in biometrics-based authentication systems. IBM Systems Journal, 40(3), 614-634.
Nandakumar, K., Chen, S., & Jain, A. K. (2009). Likelihood ratio-based biometric score fusion. IEEE Transactions on Pattern Analysis and Machine Intelligence, 31(2), 351-357.
Rattani, A., Deravi, F., & Mura, N. (2018). Spoofing attacks and countermeasures in automatic speaker verification: A review. Digital Signal Processing, 80, 113-130.
Liu, C., & Wechsler, H. (2002). Gait authentication using time-delay neural networks. IEEE Transactions on Neural Networks, 13(1), 135-140.
Soleymani, M., Garcia, D., & Pun, T. (2012). Affective computing: A review of emotion recognition modalities, databases, and features. Multimedia Tools and Applications, 59(1), 1-34.
Daugman, J. G. (2004). How iris recognition works. IEEE Transactions on Circuits and Systems for Video Technology, 14(1), 21-30.
Li, S. Z., & Jain, A. K. (2005). Encyclopedia of biometrics. Springer Science & Business Media.
Jain, A. K., Flynn, P., & Ross, A. (Eds.). (2007). Handbook of biometrics. Springer Science & Business Media.
Jain, A. K., Ross, A., & Pankanti, S. (2006). Biometrics: A tool for information security. IEEE Transactions on Information Forensics and Security, 1(2), 125-143.
Ross, A., Shah, S., & Jain, A. K. (2005). From template to image: Reconstructing fingerprints from minutiae points. IEEE Transactions on Pattern Analysis and Machine Intelligence, 27(3), 392-407.
Singh, A. ., & Kumar, V. . (2023). Sentiment Analysis of Customer Satisfaction Towards Repurchase Intension and the Word-Of-Mouth Advertising in Online Shopping Behavior Using Regression Analysis and Statistical Computing Techniques. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 45–51. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2506
Wayman, J. L., Jain, A. K., & Maltoni, D. (2005). An introduction to biometric fusion. Proceedings of the IEEE, 92(6), 948-960.
Prabhakar, S., Pankanti, S., & Jain, A. K. (2003). Biometric recognition: Security and privacy concerns. IEEE Security & Privacy, 1(2), 33-42.
Rathgeb, C., & Busch, C. (2011). On the vulnerability of fingerprint verification systems to fake fingerprint attacks. IEEE Transactions on Information Forensics and Security, 6(1), 182-194.
Jain, A. K., & Dass, S. C. (2017). Machine learning for biometric recognition. Proceedings of the IEEE, 106(2), 204-221.
Marasco, E., Sansone, C., & Verdoliva, L. (2017). Deep learning for forgery detection in images. IEEE Transactions on Information Forensics and Security, 12(11), 2549-2564.
Kryszczuk, K., & Struc, V. (2019). Voice anti-spoofing with deep learning: An overview. IEEE Signal Processing Magazine, 36(3), 100-108.
Dantcheva, A., Elia, P., & Ross, A. (2017). Can facial cosmetics affect the matching performance of face recognition systems? IEEE Transactions on Information Forensics and Security, 12(11), 2595-2608.
Kong, A., & Zhou, X. (2005). Local binary patterns applied to face recognition: A survey. IEEE Transactions on Pattern Analysis and Machine Intelligence, 31(12), 2106-2121.
Sequeira, A. F., Marcel, S., & Nicolls, F. (2019). Deep speaker embeddings for short-duration spoofing and countermeasure. IEEE Transactions on Information Forensics and Security, 14(9), 2353-2365.
Galbally, J., Fierrez, J., & Ortega-Garcia, J. (2013). HMM-based dynamic signature verification: An overview of recent advances. IEEE Transactions on Systems, Man, and Cybernetics, Part C: Applications and Reviews, 43(5), 561-576.
Ferrara, M., Franco, A., & Maltoni, D. (2012). Fusion of fingerprint and palmprint for identity verification. IEEE Transactions on Pattern Analysis and Machine Intelligence, 34(3), 561-574.
Määttä, J., Hadid, A., & Pietikäinen, M. (2011). Face spoofing detection from single images using micro-texture analysis. In 2011 International Joint Conference on Biometrics (IJCB) (pp. 1-6). IEEE.
Nguyen, H. T., & Savvides, M. (2019). CapsuleFace: Capsule network driven automatic face recognition. IEEE Transactions on Pattern Analysis and Machine Intelligence, 41(2), 379-393.
Sun, Y., Wang, X., & Tang, X. (2014). Deep learning face representation by joint identification-verification. In Advances in neural information processing systems (pp. 1988-1996).
Li, J., Guo, Y., & Li, X. (2021). Biometric-based authentication systems: A comprehensive survey. ACM Computing Surveys, 54(3), 1-33. doi:10.1145/3443431
Jin, Z., Yin, Y., & Li, S. Z. (2021). Recent advances in deep learning for biometrics: Concepts, methods and challenges. Pattern Recognition, 115, 107910. doi:10.1016/j.patcog.2021.107910
Rathgeb, C., & Busch, C. (2022). On the security of biometric template protection: A systematic review of the literature. IEEE Transactions on Information Forensics and Security, 17(1), 113-133. doi:10.1109/TIFS.2021.3056496
Damer, N., Kocur, D., & Slavicek, J. (2022). Biometric modalities and their vulnerabilities: A comprehensive survey. Journal of Information Security and Applications, 65, 102844. doi:10.1016/j.jisa.2021.102844
Mwangi, J., Cohen, D., Costa, R., Min-ji, K., & Suzuki, H. Optimizing Neural Network Architecture for Time Series Forecasting. Kuwait Journal of Machine Learning, 1(3). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/132
Chen, Y., Liu, X., Chellappa, R., & Phillips, P. J. (2023). Deep learning-based face presentation attack detection: Recent advances and future directions. IEEE Signal Processing Magazine, 40(1), 34-48. doi:10.1109/MSP.2022.3049974
McCree, A., Martinez-Diaz, M., & Ross, A. (2022). Liveness detection in biometric systems: A survey. IEEE Transactions on Information Forensics and Security, 17(1), 193-209. doi:10.1109/TIFS.2021.3058537
Ghahramani, M., Gomez-Barrero, M., & Fierrez, J. (2021). Finger vein recognition: A comprehensive review. Pattern Recognition Letters, 149, 18-27. doi:10.1016/j.patrec.2021.05.016
Wang, Y., Gao, X., Tang, Y. Y., & Liu, X. (2022). Biometric cryptosystems: A comprehensive survey. IEEE Access, 10, 48414-48434. doi:10.1109/ACCESS.2022.3052541
Rathgeb, C., Uhl, A., Wild, P., & Busch, C. (2023). Template aging in biometric systems: A comprehensive survey. IEEE Transactions on Biometrics, Behavior, and Identity Science, 1(2), 111-130. doi:10.1109/TBIOM.2022.3124140
Raj, R., & Sahoo, D. S. S. . (2021). Detection of Botnet Using Deep Learning Architecture Using Chrome 23 Pattern with IOT. Research Journal of Computer Systems and Engineering, 2(2), 38:44. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/31
Rattani, A., Deravi, F., & Singh, A. K. (2021). Biometric presentation attack detection: A review of recent advances. IEEE Transactions on Biometrics, Behavior, and Identity Science, 3(3), 363-383. doi:10.1109/TBIOM.2021.3052707
Park, U. S., & Jain, A. K. (2022). Biometric recognition: Recent advances and emerging trends. IEEE Signal Processing Magazine, 39(2), 126-146. doi:10.1109/MSP.2021.3056582
Bours, P., & Tuyls, P. (2022). Privacy in biometrics: A survey on biometric template protection schemes. ACM Computing Surveys, 55(2), 1-32. doi:10.1145/3473765
Prof. Amruta Bijwar. (2016). Design and Analysis of High Speed Low Power Hybrid Adder Using Transmission Gates. International Journal of New Practices in Management and Engineering, 5(03), 07 - 12. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/46
Gafurov, D., & Lindley, C. A. (2021). Biometric encryption: A comprehensive review. ACM Computing Surveys, 54(4), 1-38. doi:10.1145/3474568
Rathgeb, C., & Busch, C. (2021). Template protection for biometric authentication: A survey. IEEE Transactions on Pattern Analysis and Machine Intelligence, 43(5), 1425-1441. doi:10.1109/TPAMI.2020.2973632
Durão, F., Fred, A., & Alexandre, L. A. (2014). Gait recognition based on fusion of multi-view Gait Energy Images. IEEE Transactions on Pattern Analysis and Machine Intelligence, 36(9), 1834-1839.