Clustering of Non-Associated Item Sets for Analyzing Show Room Sales Dataset
Main Article Content
Abstract
Market basket analysis (MBA) is a well-liked method for identifying relationships between products that people purchase in a database. It is predicated on association rule mining (ARM), a data mining technique that pulls valuable data from huge databases. Due to consumers using internet applications for online shopping and insurance, an ever-increasing amount of data is generated online. It produces large amounts and, if mined effectively, will greatly benefit society as a whole as well as individuals. So, numerous data science and machine learning-related techniques have been created to gradually unlock the potential. The Clustering of Non-Associated Item Sets (CNAIS) of the Sales dataset used in the Showroom for choosing customers for benefits and web application design is discussed in this study. The CNAIS algorithm implementation process and dataset for this study are discussed.
Article Details
References
K.M.V. Madan Kumar,Dr. P.V.S. Srinivas, Algorithms for Mining Sequential Patterns International Journal of Information Sciences and Application. ISSN 0974-2255 Volume 3, Number 1 (2011), pp. 59-69
Agrawal, R., Imielinski, T., and Swami, A. N. 1993. Mining association rules between sets of items in large databases. In Proceedings of the 1993 ACM SIGMOD International Conference on Management of Data, P. Buneman and S. Jajodia, Eds. Washington, D.C., 207–216.
Peltier J W,Schibmwsky J A,Schuhz D E,et al. “Interactive Psychographics:Cross-Selling in the Banking Industry” .Journal of Advertising Research, 2002, 4 (2) ,pp.7-22.
Sotiris Kotsiantis, Dimitris Kanellopoulos,Association Rules Mining: A Recent Overview , GESTS International Transactions on Computer Science and Engineering, Vol.32 (1), 2006, pp. 71-82
Bellini etal. “Multi Clustering Recommendation System for Fashion Retail” ,Multimedia Tools and Applications p1-28, 1573-7721 2022 Springer
Jiawei Han and Micheline Kamber, Data Mining: Concepts and Techniques, Second Edition, Morgan Kaufmann Publishers is an imprint of Elsevier 2006.
R. Agrawal and R. Srikant. Mining Sequential Patterns. In Proc. of the 11th Int’lConference on Data Engineering~ Taipei, Taiwan, March 1995.
G.Ahalya and H. M. Pandey, “Data clustering approaches survey and analysis,” 2015 International Conference on Futuristic Trends on Computational Analysis and Knowledge Management (ABLAZE), 2015, pp. 532-537, doi: 10.1109/ABLAZE.2015.7154919.
Rui Xu and D. Wunsch, “Survey of clustering algorithms,” in IEEE Transactions on Neural Networks, vol. 16, no. 3, pp. 645-678, May 2005, doi: 10.1109/TNN.2005.845141.
Ramakrishna, M. T., Venkatesan, V. K., Bhardwaj, R., Bhatia, S., Rahmani, M. K. I., Lashari, S. A., & Alabdali, A. M. (2023). HCoF: Hybrid Collaborative Filtering Using Social and Semantic Suggestions for Friend Recommendation. Electronics, 12(6), 1365.
Xu, D., Tian, Y. A Comprehensive Survey of Clustering Algorithms. Ann. Data. Sci. 2, 165–193 (2015). https://doi.org/10.1007/s40745-015-0040-1
Prof. Amruta Bijwar, Prof. Madhuri Zambre. (2018). Voltage Protection and Harmonics Cancellation in Low Voltage Distribution Network. International Journal of New Practices in Management and Engineering, 7(04), 01 - 07. https://doi.org/10.17762/ijnpme.v7i04.68.
Kanungo, Tapas, et al. “An efficient k-means clustering algorithm: Analysis and implementation.” Pattern Analysis and Machine Intelligence, IEEE Transactions on 24.7 (2002): 881-892.
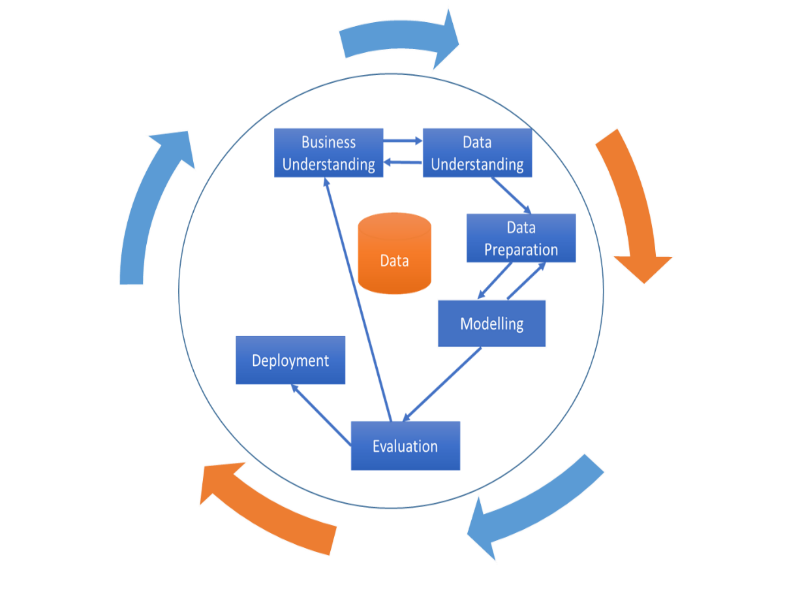
Shearer, C. (2000) The CRISP-DM Model: The New Blueprint for Data Mining. Journal of Data Warehousing, 5, 13-22.
Raghunath, K. M. K. ., Kumar, V. V. ., Venkatesan, M. ., Singh, K. K. ., Mahesh, T. R. ., & Singh, A. . (2022). XGBoost Regression Classifier (XRC) Model for Cyber Attack Detection and Classification Using Inception V4. Journal of Web Engineering, 21(04), 1295–1322. https://doi.org/10.13052/jwe1540-9589.21413
Mahesh, T. R., Ram, M. S., Ram, N. S. S., Gowtham, A., & Swamy, T. N. (2021). Real-Time Eye Blinking for Password Authentication. In Integrated Emerging Methods of Artificial Intelligence & Cloud Computing (pp. 428-434). Cham: Springer International Publishing.
Christoph Schröer, Felix Kruse, Jorge Marx Gómez,A Systematic Literature Review on Applying CRISP-DM Process Model, Procedia Computer Science,Volume 181,2021,Pages 526-534,ISSN 1877-0509
https://indatalabs.com/blog/why-python-is-used-in-data-science
Mahesh, T.R., Vinoth Kumar, V., Shashikala, H.K., Roopashree, S. (2023). ML Algorithms for Providing Financial Security in Banking Sectors with the Prediction of Loan Risks. In: Sarveshwaran, V., Chen, J.IZ., Pelusi, D. (eds) Artificial Intelligence and Cyber Security in Industry 4.0. Advanced Technologies and Societal Change. Springer, Singapore. https://doi.org/10.1007/978-981-99-2115-7_14
Devarajan, D., Alex, D. S., Mahesh, T. R., Kumar, V. V., Aluvalu, R., Maheswari, V. U., & Shitharth, S. (2022). Cervical cancer diagnosis using intelligent living behavior of artificial jellyfish optimized with artificial neural network. IEEE Access, 10, 126957-126968.
B. N. Kumar, T. R. Mahesh, G. Geetha and S. Guluwadi, "Redefining Retinal Lesion Segmentation: A Quantum Leap With DL-UNet Enhanced Auto Encoder-Decoder for Fundus Image Analysis," in IEEE Access, vol. 11, pp. 70853-70864, 2023, doi: 10.1109/ACCESS.2023.3294443.
Salim Mohammed Al-Waili, Zulkiflee Abd Latif, Siti Aekbal Salleh. (2023). GIS-Based Decision Support System and Analytical Hierrachical Process for Integrated Flood Management. International Journal of Intelligent Systems and Applications in Engineering, 11(4s), 392–399. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2678.
Mahesh, T.R., Vinoth Kumar, V., Shashikala, H.K., Roopashree, S. (2023). ML Algorithms for Providing Financial Security in Banking Sectors with the Prediction of Loan Risks. In: Sarveshwaran, V., Chen, J.IZ., Pelusi, D. (eds) Artificial Intelligence and Cyber Security in Industry 4.0. Advanced Technologies and Societal Change. Springer, Singapore. https://doi.org/10.1007/978-981-99-2115-7_14
K. Gunasekaran, V. V. Kumar, A. C. Kaladevi, T. R. Mahesh, C. R. Bhat and K. Venkatesan, "Smart Decision-Making and Communication Strategy in Industrial Internet of Things," in IEEE Access, vol. 11, pp. 28222-28235, 2023, doi: 10.1109/ACCESS.2023.3258407.