Hybrid CNN+LSTM Deep Learning Model for Intrusions Detection Over IoT Environment
Main Article Content
Abstract
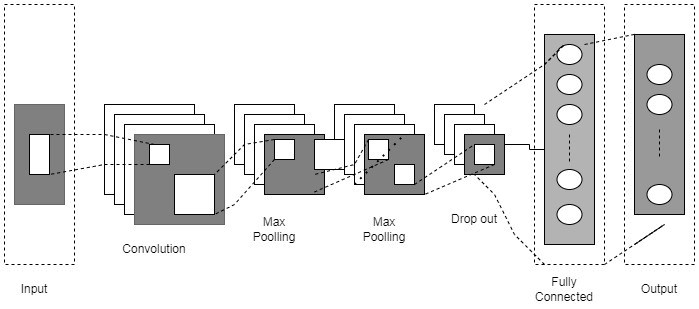
The connectivity of devices through the internet plays a remarkable role in our daily lives. Many network-based applications are utilized in different domains, e.g., health care, smart environments, and businesses. These applications offer a wide range of services and provide services to large groups. Therefore, the safety of network-based applications has always been an area of research interest for academia and industry alike. The evolution of deep learning has enabled us to explore new areas of research. Hackers make use of the vulnerabilities in networks and attempt to gain access to confidential systems and information. This information and access to systems can be very harmful and portray losses beyond comprehension. Therefore, detection of these network intrusions is of the utmost importance. Deep learning-based techniques require minimal inputs while exploring every possible feature set in the network. Thus, in this paper, we present a hybrid CNN+LSTM deep learning model for the detection of network intrusions. In this research, we detect DDOS types of network intrusions, i.e., R2L, R2R, Prob, and which belong to the active attack category, and PortScan, which falls in the passive attack category. For this purpose, we used the benchmark CICIDS2017 dataset for conducting the experiments and achieved an accuracy of 99.82% as demonstrated in the experimental results.
Article Details
References
Mahmudul Hasan, Md. Milon Islam, Ishrak Islam, M.M.A. Hashem, Attack and Anomaly Detection in IoT Sensors in IoT Sites Using Machine Learning Approaches, Internet of Things (2019), doi: https://doi.org/10.1016/j.iot.2019.100059
M.-O. Pahl, F.-X. Aubet, All eyes on you: Distributed Multi-Dimensional IoT microservice anomaly detection, in: 2018 14th International Conference on Network and Service Management (CNSM) (CNSM 2018), Rome, Italy, 2018.
M.-O. Pahl, F.-X. Aubet, S. Liebald, Graph-based IoT microservice security, in: NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium, IEEE, 2018, pp. 1–3.
H. H. Pajouh, R. Javidan, R. Khayami, D. Ali, K.-K. R. Choo, A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks, IEEE Transactions on Emerging Topics in Computing
Banaamah, A.M.; Ahmad, I. Intrusion Detection in IoT Using Deep Learning. Sensors 2022, 22, 8417. https://doi.org/10.3390/s22218417
Zhang, J.; Pan, L.; Han, Q.-L.; Chen, C.; Wen, S.; Xiang, Y. Deep learning-based attack detection for cyber-physical system cybersecurity: A survey. IEEE/CAA J. Autom. Sin. 2021, 9, 377-391
Jaffar, S. ., & Baharum, A. . (2023). Gamification Framework for Engagement Design Using Pls-Sem. International Journal of Intelligent Systems and Applications in Engineering, 11(4s), 194–202. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2646
Lee, I. Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management. Futur. Internet 2020, 12, 157.
Almiani, M.; AbuGhazleh, A.; Al-Rahayfeh, A.; Atiewi, S.; Razaque, A. Deep recurrent neural network for IoT intrusion detection system. Simul. Model. Pract. Theory 2020, 101, 102031.
Azumah, S.W.; Elsayed, N.; Adewopo, V.; Zaghloul, Z.S.; Li, C. A deep lstm based approach for intrusion detection iot devices network in smart home. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 26–31 July 2021.
Bambang Susilo and Riri Fitri Sari (2020). Intrusion Detection in IoT Networks Using Deep Learning Algorithm, Information 2020, 11, 279; doi:10.3390/info11050279
Lee, S., Shin, D., Kang, S., Kim, J., & Kim, C. (2021). A Hybrid Deep Learning Model for IoT Intrusion Detection. Sensors, 21(15), 5247. https://doi.org/10.3390/s21155247
Liu, X., Zhang, Y., Xie, Y., Wang, Y., & Zhang, W. (2021). Deep Learning Based Intrusion Detection for IoT Systems Using Bi-LSTM and Convolutional Neural Network. IEEE Access, 9, 84015-84025. https://doi.org/10.1109/ACCESS.2021.3088101
Lee, W.-H., Chen, Y.-C., Lee, Y.-H., & Yang, C.-C. (2021). Intrusion Detection in IoT Networks Using Bi-LSTM and Convolutional Neural Networks. In Proceedings of the International Conference on Network-Based Information Systems (pp. 311-316). Springer. https://doi.org/10.1007/978-3-030-79150-3_33
Lee, S., Park, J., Kim, S., & Yoon, S. (2020). IoT Intrusion Detection Using Bidirectional LSTM. In Proceedings of the 15th International Conference on Availability, Reliability and Security (pp. 1-8). ACM. https://doi.org/10.1145/3407023.3407047
Khan, M. A., Abbas, H., Hussain, M., & Bilal, K. (2020). A Comprehensive Study on Intrusion Detection Systems in IoT Environments. Journal of Ambient Intelligence and Humanized Computing, 11(9), 4173-4200. https://doi.org/10.1007/s12652-019-01471-4
Wei, Y.-C., Hu, Y.-H., & Hsu, S.-S. (2020). Anomaly Detection for IoT Cybersecurity Using Bidirectional Long Short-Term Memory Networks. IEEE Access, 8, 79773-79782. https://doi.org/10.1109/ACCESS.2020.2998123
Zhang, Y.; Chen, X.; Jin, L.; Wang, X.; Guo, D. Network Intrusion Detection: Based on Deep Hierarchical Network and Original Flow Data. IEEE Access 2019, 7, 37004-37016.
Jamil, F.; Kim, D. An Ensemble of Prediction and Learning Mechanism for Improving Accuracy of Anomaly Detection in Network Intrusion Environments. Sustainability 2021, 13, 10057
Asad, M.; Asim, M.; Javed, T.; Beg, M.O.; Mujtaba, H.; Abbas, S. Deepdetect: Detection of distributed denial of service attacks using deep learning. Comput. J. 2020, 63, 983-994
Bhardwaj, A.; Mangat, V.; Vig, R. Hyperband tuned deep neural network with well posed stacked sparse autoencoder for detection of DDoS attacks in cloud. IEEE Access 2020, 8, 181916–181929.
Altunay, Hakan & Albayrak, Zafer. (2023). A hybrid CNN + LSTM-based intrusion detection system for industrial IoT networks. Engineering Science and Technology an International Journal. 38. 10.1016/j.jestch.2022.101322.
Ali Alferaidi, Kusum Yadav, Yasser Alharbi, Navid Razmjooy, Wattana Viriyasitavat, Kamal Gulati, Sandeep Kautish, Gaurav Dhiman, "Distributed Deep CNN-LSTM Model for Intrusion Detection Method in IoT-Based Vehicles", Mathematical Problems in Engineering, vol. 2022, Article ID 3424819, 8 pages, 2022. https://doi.org/10.1155/2022/3424819
W. Cao, “CNN-based intelligent safety surveillance in green IoT applications,” China Communications, vol. 18, no. 1, pp. 108–119, 2021.
M. Ganesan and N. Sivakumar, “IoT based heart disease prediction and diagnosis model for healthcare using machine learning models,” in Proceedings of the 2019 IEEE International Conference on System, Computation, Automation and Networking (ICSCAN), pp. 1-5, Pondicherry, India, March 2019.
R. Fotohi, S. Firoozi Bari, and M. Yusefi, “Securing wireless sensor networks against denial?of?sleep attacks using RSA cryptography algorithm and interlock protocol,” International Journal of Communication Systems, vol. 33, no. 4, Article ID e4234, 2020.
Rajesh Kumar Chaudhary, M. K. C. (2021). The Role of School Management Towards Staff Motivation for Effective Performance in Nepal: During the Covid-19. International Journal of New Practices in Management and Engineering, 10(01), 01–11. https://doi.org/10.17762/ijnpme.v10i01.93
R. Fotohi and S. F. Bari, “A novel countermeasure technique to protect WSN against denial-of-sleep attacks using firefly and Hopfield neural network (HNN) algorithms,” The Journal of Supercomputing, vol. 76, pp. 1–27, 2020.
M. Zaminkar and R. Fotohi, “SoS-RPL: securing internet of things against sinkhole attack using RPL protocol-based node rating and ranking mechanism,” Wireless Personal Communications, vol. 114, 2020.
G. D. L. T. Parra, P. Rad, K. K. R. Choo, and N. Beebe, “Detecting Internet of Things attacks using distributed deep learning,” Journal of Network and Computer Applications, vol. 163, Article ID 102662, 2020.
R. Fotohi, E. Nazemi, and F. S. Aliee, “An agent-based self-protective method to secure communication between UAVs in unmanned aerial vehicle networks,” Vehicular Communications, vol. 26, Article ID 100267, 2020.
M. Roopak, G. Y. Tian, and J. Chambers, “An intrusion detection system against ddos attacks in iot networks,” in Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), pp. 0562–0567, IEEE, Las Vegas, NV, USA, January 2020.
T. Alladi, A. Agrawal, B. Gera, V. Chamola, B. Sikdar, and M. Guizani, “Deep neural networks for securing IoT enabled vehicular ad-hoc networks,” in Proceedings of the ICC 2021-IEEE International Conference on Communications, pp. 1–6, IEEE, Montreal, QC, Canada, June 2021.
Y. Mirsky, T. Doitshman, Y. Elovici, and A. Shabtai, “Kitsune: an ensemble of autoencoders for online network intrusion detection,” 2018, https://arxiv.org/abs/1802.09089.
A. Khraisat, I. Gondal, P. Vamplew, J. Kamruzzaman, and A. Alazab, “Hybrid intrusion detection system based on the stacking ensemble of c5 decision tree classifier and one class support vector machine,” Electronics, vol. 9, no. 1, p. 173, 2020.
G. J. M. Ariyathilake, M. H. R. Sandeepanie, and P. L. Rupasinghe, “SQL injection detection and prevention solution for web applications,” 2021, http://ir.kdu.ac.lk/handle/345/5253.
Chen, L.; Kuang, X.; Xu, A.; Suo, S.; Yang, Y. A Novel Network Intrusion Detection System Based on CNN. In Proceedings of the 2020 Eighth International Conference on Advanced Cloud and Big Data (CBD), Taiyuan, China, 19–20 September 2020; pp. 243-247.
Mwangi , J., Cohen, D., Silva, C., Min-ji, K., & Suzuki, H. Improving Fraud Detection in Financial Transactions with Machine Learning. Kuwait Journal of Machine Learning, 1(4). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/148
Roopak, M.; Tian, G.Y.; Chambers, J. Deep learning models for cyber security in IoT networks. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 452-457.
Sivamohan, S.; Sridhar, S.S.; Krishnaveni, S. An Effective Recurrent Neural Network (RNN) based Intrusion Detection via Bidirectional Long Short-Term Memory. In Proceedings of the 2021 International Conference on Intelligent Technologies (CONIT), Karnataka, India, 25–27 June 2021; pp. 1-5.
Atefi, K.; Hashim, H.; Khodadadi, T. A hybrid anomaly classification with deep learning (DL) and binary algorithms (BA) as optimizer in the intrusion detection system (IDS). In Proceedings of the 2020 16th IEEE International Colloquium on SIGNAL Processing & Its Applications (CSPA), Langkawi, Malaysia, 28–29 February 2020; pp. 29-34.
Asad, M.; Asim, M.; Javed, T.; Beg, M.O.; Mujtaba, H.; Abbas, S. Deepdetect: Detection of distributed denial of service attacks using deep learning. Comput. J. 2020, 63, 983–994.