Hybrid Dynamic Source Routing Technique and Security Implementation in Adhoc Network Topology
Main Article Content
Abstract
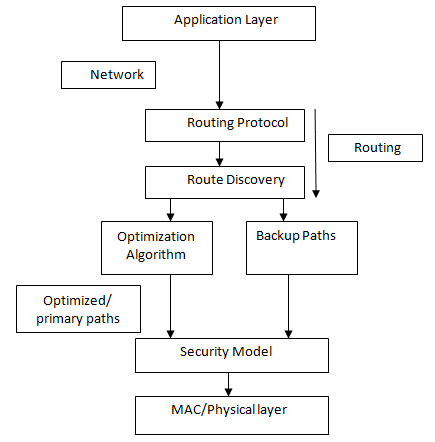
Routing protocols that are developed with the error-prone environment and resource constraints of mobile nodes in mind perform better in wireless Ad Hoc environments. A good and dependable routing method is required to meet the packet transition aim. When the network is small, most existing routing algorithms operate fine, but when the network is large, there is a problem with link breakage in multipath routing algorithms, especially on demand routing algorithms. As a result, we investigated many forms of routing protocols in order to identify all of the existing algorithms' flaws. In this study, we examine existing protocols in terms of network factors such as delay, throughput, energy consumption, control overhead, and so on.
Article Details
References
] S.Misra, N. Saha, “Detour: Dynamic Task Offloading in … S. Misra, I. Woungang and S.Misra (Eds.), Guide to Wireless Ad Hoc … and Networks Series, Springer-Verlag, London, U.K., February 2009, 632 pages
] K.Toh ,Ad Hoc Mobile Wireless Networks: Protocols and Systems,Prentice Hall PTR,NJ,2002
] Misra and B. J. Oommen, “Adaptive Algorithms for Network Routing and Traffic Engineering”, Proceedings of the 19th National Conference on Artificial Intelligence (AAAI’04) , San Jose, California, USA, July 25-29, 2004.
] Q. Y. Liu, Multipath based QoS routing in MANET,, Journal of Networks 4 (8) (2004) 771–778.
] J. Haas, Pearlman MR: The zone routing protocol: a hybrid framework for routing, Vol. 2001, Addison-Wesley, Reading, MA.
] Nasipuri, R. Castaneda, Das SR: Performance of multipath routing for on-demand protocols in mobile ad hoc networks, Mob. Netw. Appl 4 (339-349) 10–1023.
] Ducatelle, Di, Caro GA, Gambardella LM: Using ant agents to combine reactive and proactive strategies for routing in mobile ad hoc networks, Int. J. Comput. Intell. Appl. (Special Issue on NatureInspired Approaches to Networks and Telecommunications) 2005 5–2.
] https://minigranth.in/mobile-adhoc-networks-tutorial/dsdv-routing-protocol-manet
] https://minigranth.in/mobile-adhoc-networks-tutorial/global-state-routing-gsr-manet.
] Vaishali, Priyank Pandey, Prashant GoelA Review on Security in MANET, International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Published by, www.ijert.org ICCCS - 2017 Conference Proceedings
] S.Sudha, V.Madhu Viswanatham, K.Brindha, L. Agilandeeswari , School of Information Technology and Engineering, School of Computing Science and Engineering VIT University, Vellore-632 014, TamilNadu, IndiaImplementation of Enhanced Data Encryption Standard on MANET with less energy consumption through limited computation, International Journal of Engineering Research and Development eISSN : 2278-067X, pISSN : 2278-800X, www.ijerd.com Volume 2, Issue 4 (July 2012), PP. 46-52.
] Neelima, Lekharaju Sai Siddhartha, Chavali Meghana, Shaik Sameer4,Shaik Ashika,Vemulamada Naga Chandramouli,SECURITY IN MANETS USING CRYPTOGRAPHY ALGORITHMS, International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056,Volume: 04 Issue: 03 | Mar -2017 www.irjet.net p-ISSN: 2395-0072