An Improved Integrity-Based Hybrid Multi-User Data Access Control for Cloud Heterogeneous Supply Chain Databases
Main Article Content
Abstract
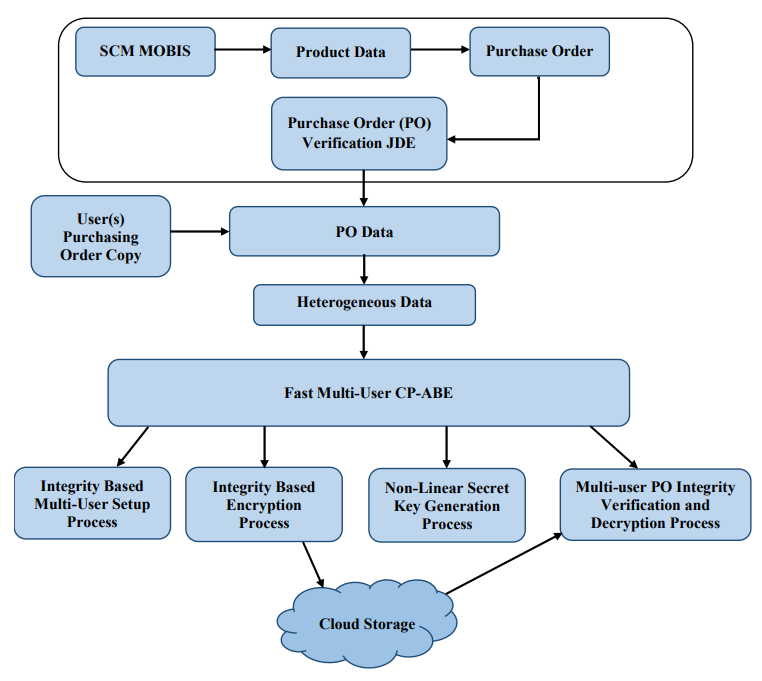
Cloud-based supply chain applications play a vital role in the multi-user data security framework for heterogeneous data types. The majority of the existing security models work effectively on small to medium-sized datasets with a homogenous data structure. In contrast, Supply Chain Management (SCM) systems in the real world utilize heterogeneous databases. The heterogeneous databases include a massive quantity of raw SCM data and a scanned image of a purchase quotation. In addition, as the size of the database grows, it becomes more challenging to provide data security on multi-user SCM databases. Multi-user datatypes are heterogeneous in structure, and it is complex to apply integrity and confidentiality models due to high computational time and resources. Traditional multi-user integrity algorithms are difficult to process heterogeneous datatypes due to computational time and variation in hash bit size. Conventional attribute-based encryption models such as "Key-policy attribute-based encryption" (KP-ABE), "Ciphertext-Policy Attribute-Based Encryption" (CP-ABE) etc., are used to provide strong data confidentiality on large textual data. Providing security for heterogeneous databases in a multi-user SCM system requires a significant computational runtime for these conventional models. An enhanced integrity-based multi-user access control security model is created for heterogeneous databases in the cloud infrastructure to address the problems with heterogeneous SCM databases. A non-linear integrity model is developed to provide strong integrity verification in the multi-user communication process. A multi-user based access control model is implemented by integrating the multi-user hash values in the encoding and decoding process. Practical results proved that the multi-user non-linear integrity-based multi-access control framework has better runtime and hash bit variation compared to the conventional models on large cloud-based SCM databases.
Article Details
References
Ali, S. I., Ali, A., AlKilabi, M., & Christie, M. (2021). Optimal supply chain design with product family: A cloud-based framework with real-time data consideration. Computers & Operations Research, 126, 105112, doi: 10.1016/j.cor.2020.105112.
Karumanchi, M. D., Sheeba, J. I., & Devaneyan, S. P. (2019, December). Cloud based supply chain management system using blockchain. In 2019 4th International Conference on Electrical, Electronics, Communication, Computer Technologies and Optimization Techniques (ICEECCOT) (pp. 390-395). IEEE, doi: 10.1109/ICEECCOT46775.2019.9114692
Bergier, I., Papa, M., Silva, R., & Santos, P. M. (2021). Cloud/edge computing for compliance in the Brazilian livestock supply chain. Science of The Total Environment, 761, 143276, doi: 10.1016/j.scitotenv.2020.143276.
Bose, R., Mondal, H., Sarkar, I., & Roy, S. (2022). Design of smart inventory management system for construction sector based on IoT and cloud computing. e-Prime-Advances in Electrical Engineering, Electronics and Energy, 2, 100051, doi: 10.1016/j.prime.2022.100051.
Kamble, V. S. ., Khampariya, P. ., & Kalage, A. A. . (2023). A Survey on the Development of Real-Time Overcurrent Relay Coordination Using an Optimization Algorithm. International Journal of Intelligent Systems and Applications in Engineering, 11(3s), 104–114. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2537
Karumanchi, M. D., Sheeba, J. I., & Devaneyan, S. P. (2022). Integrated Internet of Things with cloud developed for data integrity problems on supply chain management. Measurement: Sensors, 24, 100445, doi: 10.1016/j.measen.2022.100445
Chen, L. M., & Chang, W. L. (2021). Supply-and cyber-related disruptions in cloud supply chain firms: Determining the best recovery speeds. Transportation Research Part E: Logistics and Transportation Review, 151, 102347, doi: 10.1016/j.tre.2021.102347.
Chinnasamy, P., Padmavathi, S., Swathy, R., & Rakesh, S. (2021). Efficient data security using hybrid cryptography on cloud computing. In Inventive Communication and Computational Technologies: Proceedings of ICICCT 2020 (pp. 537-547). Springer Singapore, doi: 10.1007/978-981-15-7345-3_46
Javed, B., Bloodsworth, P., Rasool, R. U., Munir, K., & Rana, O. (2016). Cloud market maker: An automated dynamic pricing marketplace for cloud users. Future Generation Computer Systems, 54, 52-67, doi: 10.1016/j.future.2015.06.004.
Abdel-Basset, M., Gunasekaran, M., Mohamed, M., & Chilamkurti, N. (2019). A framework for risk assessment, management and evaluation: Economic tool for quantifying risks in supply chain. Future Generation Computer Systems, 90(1), 489-502, doi: 10.1016/j.future.2018.08.035.
Longo, F., & Mirabelli, G. (2008). An advanced supply chain management tool based on modeling and simulation. Computers & Industrial Engineering, 54(3), 570-588, doi: 10.1016/j.cie.2007.09.008.
Peiris, K. D. A., Jung, J., & Gallupe, R. B. (2015). Building and evaluating ESET: A tool for assessing the support given by an enterprise system to supply chain management. Decision Support Systems, 77, 41-54, doi: 10.1016/j.dss.2015.05.004.
Yeh, T. M., Yang, C. C., & Lin, W. T. (2007). Service quality and ERP implementation: A conceptual and empirical study of semiconductor-related industries in Taiwan. Computers in Industry, 58(8-9), 844-854, doi: 10.1016/j.compind.2007.03.002.
Hassan, R. S., Nawaz, A., Lashari, M. N., & Zafar, F. (2015). Effect of customer relationship management on customer satisfaction. Procedia economics and finance, 23, 563-567, doi: 10.1016/S2212-5671(15)00513-4.
Silva Filho, O. S., & Neagu, G. (2000). Special Session on Models and Tools for Supply Chain Management. IFAC Proceedings Volumes, 33(17), 909-910, doi: 10.1016/S1474-6670(17)39524-1.
Hartono, E., Holsapple, C. W., & Jin, H. (2011). The role of technological know-how in c-commerce success. Decision support systems, 51(1), 77-87, doi: 10.1016/j.dss.2010.11.030.
AlAhmad, A. S., Kahtan, H., Alzoubi, Y. I., Ali, O., & Jaradat, A. (2021). Mobile cloud computing models security issues: A systematic review. Journal of Network and Computer Applications, 190, 103152, doi: 10.1016/j.jnca.2021.103152.
Karumanchi, M. D., Sheeba, J. I., & Devaneyan, S. P. (2022). Nonlinear integrity algorithm for blockchain based supply chain databases. In Pervasive Computing and Social Networking: Proceedings of ICPCSN 2022 (pp. 169-181). Singapore: Springer Nature Singapore, doi: 10.1007/978-981-19-2840-6_13.
Deep, G., Sidhu, J., & Mohana, R. (2022). Insider threat prevention in distributed database as a service cloud environment. Computers & Industrial Engineering, 169, 108278, doi: 10.1016/j.cie.2022.108278.
Parast, F. K., Sindhav, C., Nikam, S., Yekta, H. I., Kent, K. B., & Hakak, S. (2022). Cloud computing security: A survey of service-based models. Computers & Security, 114, 102580, doi: 10.1016/j.cose.2021.102580.
Li, R., Wang, X. A., Yang, H., Niu, K., Tang, D., & Yang, X. (2022). Efficient certificateless public integrity auditing of cloud data with designated verifier for batch audit. Journal of King Saud University-Computer and Information Sciences, 34(10), 8079-8089, doi: 10.1016/j.jksuci.2022.07.020.
Nain, G., Pattanaik, K. K., & Sharma, G. K. (2022). Towards edge computing in intelligent manufacturing: Past, present and future. Journal of Manufacturing Systems, 62, 588-611, doi: 10.1016/j.jmsy.2022.01.010.
Chinnasamy, P., & Deepalakshmi, P. (2022). HCAC-EHR: hybrid cryptographic access control for secure EHR retrieval in healthcare cloud. Journal of Ambient Intelligence and Humanized Computing, 1-19, doi: 10.1007/s12652-021-02942-2
Belguith, S., Kaaniche, N., Laurent, M., Jemai, A., & Attia, R. (2018). Phoabe: Securely outsourcing multi-authority attribute based encryption with policy hidden for cloud assisted iot. Computer Networks, 133, 141-156, doi: 10.1016/j.comnet.2018.01.036.
Mandal, M. (2020). Privacy-preserving fully anonymous ciphertext policy attribute-based broadcast encryption with constant-size secret keys and fast decryption. Journal of Information Security and Applications, 55, 102666, doi: 10.1016/j.jisa.2020.102666.
Pareek, G., & Purushothama, B. R. (2020). Proxy re-encryption for fine-grained access control: Its applicability, security under stronger notions and performance. Journal of Information Security and Applications, 54, 102543, doi: 10.1016/j.jisa.2020.102543.
La Manna, M., Perazzo, P., & Dini, G. (2021). SEA-BREW: A scalable attribute-based encryption revocable scheme for low-bitrate IoT wireless networks. Journal of Information Security and Applications, 58, 102692, doi: 10.1016/j.jisa.2020.102692.
Sun, X., Wang, H., Fu, X., Qin, H., Jiang, M., Xue, L., & Wei, X. (2021). Substring-searchable attribute-based encryption and its application for IoT devices. Digital Communications and Networks, 7(2), 277-283, doi: 10.1016/j.dcan.2020.07.008.
Abdul Rahman, Artificial Intelligence in Drug Discovery and Personalized Medicine , Machine Learning Applications Conference Proceedings, Vol 1 2021.
Sun, P. (2020). Security and privacy protection in cloud computing: Discussions and challenges. Journal of Network and Computer Applications, 160, 102642, doi: 10.1016/j.jnca.2020.102642.
Karumanchi, M. D., Sheeba, J. I., & Devaneyan, S. P. (2022). Blockchain enabled supply chain using machine learning for secure cargo tracking. International Journal of Intelligent Systems and Applications in Engineering, 10(4), 434-442.
Karumanchi, M. D., Sheeba, J. I., & Devaneyan, S. P. (2023). An efficient integrity based multi-user blockchain framework for heterogeneous supply chain management applications. International Journal of Computers and Applications, 45(4), 337-351.doi: 10.1080/1206212X.2023.2199966.