Security Aware Virtual Machine Allocation Policy to Improve QoS
Main Article Content
Abstract
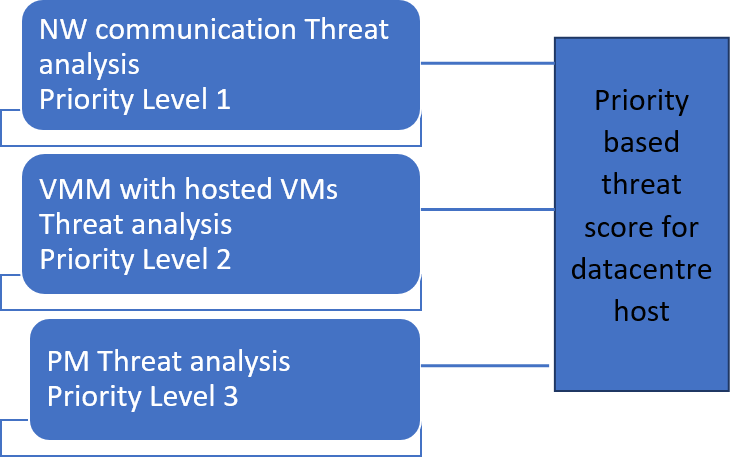
Cloud service providers find managing the energy consumption for datacentres as a critical operation. Significant energy is being used by a rising spike in the number of data centres. To overcome this challenge datacentres, attempt to reduce the number of active physical servers by carrying out virtual machine consolidation process. However, due to inadequate security measures to verify hostile cloud users, the security threats on cloud multitenancy platform have escalated. In this paper we propose energy efficient virtual machine consolidation using priority-based security aware virtual machine allocation policy to improve datacentre security. The proposed security solution considers the host threat score before virtual machine placement, which has reduced the security threats for co-residency attacks without impacting datacentre energy consumption.
Article Details
References
J. Shepard, “E N Power,” 2016. [Online]. Available: https://eepower.co m/news/unplanned-data-center-outages-cost-nearly-9000-per-minute/
A. Bhonde and S. Devane, “Impact of Cloud Attacks on Service Level Agreement,” 2021 International Conference on Communication information and Computing Technology (ICCICT), pp. 1–6, 2021.
T. Ristenpart, E. Tromer, H. Shacham, and S. Savage, “Hey, you, get off of my cloud: exploring information leakage in third-party compute clouds,” Proceedings of the 16th ACM conference on Computer and communications security, pp. 199–212, 2009.
T. Zhang, Y. Zhang, and B. Ruby, 2016. [Online]. Available: https://arxiv.org/abs/1603.03404
J. Betz, D. Westhoff, and G. Müller, “Survey on covert channels in virtual machines and cloud computing,” Transactions on Emerging Telecommunications Technologies, vol. 28, no. 6, pp. 3134–3134, 2017.
Mr. Kaustubh Patil, Promod Kakade. (2014). Self-Sustained Debacle Repression Using Zig-Bee Communication. International Journal of New Practices in Management and Engineering, 3(04), 05 - 10. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/32
A. Jasti, P. Shah, R. Nagaraj, and R. Pendse, “Security in multi-tenancy cloud,” 44th Annual 2010 IEEE International Carnahan Conference on Security Technology, pp. 35–41, 2010.
“OWASP Top 10 Risks,” Open Web Application Security Project, 2021.
Yadav, S. S. ., Maan, M. K. ., Kumar, M. S. ., J., K. ., Pund, S. S. ., & Rathod, M. . (2023). A Secure IoT Smart Network Model for the Contributory Broadcast Encryption for the Text Policy Management Scheme. International Journal of Intelligent Systems and Applications in Engineering, 11(3s), 42–48. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2530
J. Somorovsky, M. Heiderich, M. Jensen, J. Schwenk, N. Gruschka, and L. L. Iacono, “All your clouds are belong to us: security analysis of cloud management interfaces,” in Proceedings of the 3rd ACM workshop on Cloud computing security workshop (CCSW ’11). Association for Computing Machinery, 2011, pp. 3–14.
G. Somani, M. S. Gaur, D. Sanghi, M. Conti, and R. Buyya, “DDoS attacks in cloud computing: Issues, taxonomy, and future directions,” Computer Communications, vol. 107, pp. 30–48, 2017.
A. Kurmus, M. Gupta, R. Pletka, C. Cachin, and R. Haas, “A comparison of secure multi-tenancy architectures for filesystem storage clouds,” in ACM/IFIP/USENIX International Conference on Distributed Systems Platforms and Open Distributed Processing. Springer, 2011, pp. 471– 490.
G. Somani, M. S. Gaur, D. Sanghi, M. Conti, and R. Buyya, “DDoS attacks in cloud computing: Issues, taxonomy, and future directions,” Computer Communications, vol. 107, pp. 30–48, 2017.
R. Buyya, R. Ranjan, and R. N. Calheiros, “Modeling and simulation of scalable Cloud computing environments and the CloudSim toolkit: Challenges and opportunities,” 2009 international conference on high performance computing & simulation, pp. 1–11, 2009.
Jóhann, Þorvaldsson, Koskinen, P., Meer, P. van der, Steiner, M., & Keller, T. Improving Graduation Rates in Engineering Programs Using Machine Learning. Kuwait Journal of Machine Learning, 1(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/110
B. info, “SPEC’s Benchmarks and Tools,” 2011. [Online]. Available: https://www.spec.org/benchmarks.html#power