Challenges on Missing Packet Detection or Packet Dropping Attacks in Mobile Adhoc Network -A Survey
Main Article Content
Abstract
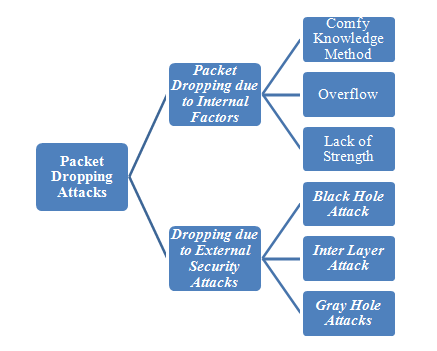
Collection of wireless nodes forms together to communicate each other in the network without infrastructure less and any access point along with the characteristics of freedom in mobility is called Mobile Adhoc Network. Transmitting of packets from source to destination plays the vital role in MANET. When a Packet is not delivered properly at the destination , its affects the performance of the MANET. Due to this characteristics of the mobility nodes can subject to falls on the packet missing also the various packets dropping security attacks take part in the dropping the packets while communication to achieve the decreasing the performance of the MANET. This article focus on the survey about the missing packet assembly as well the packet dropping security attacks in MANET.
Article Details
References
Giordano, Silvia.(2002) "Mobile ad hoc networks." Handbook of wireless networks and mobile computing (2002): 325-346.
Bang, Ankur O., and Prabhakar L. Ramteke. ( 2013) "MANET: History, challenges and applications." International Journal of Application or Innovation in Engineering & Management (IJAIEM) 2.9 (2013): 249-251.
Mohammad, Arshad Ahmad Khan, Ali Mirza Mahmood, and Srikanth Vemuru. (2019)"Intentional and unintentional misbehaving node detection and prevention in mobile adhoc network." International Journal of Hybrid Intelligence 1.2-3 (2019): 239-267.
Siddiqua, Ayesha, Kotari Sridevi, and Arshad Ahmad Khan Mohammed. (2015)"Preventing black hole attacks in MANETs using secure knowledge algorithm." 2015 International Conference on Signal Processing and Communication Engineering Systems. IEEE, 2015.
Mohammad, Arshad Ahmad Khan, Ali Mirza, and Srikanth Vemuru.(2016) "Analytical Model for Evaluating the Bottleneck Node in MANETs." Indian Journal of Science and Technology 9 (2016):
Krishnan, V. G. ., Saradhi, M. V. V. ., Dhanalakshmi, G. ., Somu, C. S. ., & Theresa, W. G. . (2023). Design of M3FCM based Convolutional Neural Network for Prediction of Wheat Disease. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 203 –. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2523
M. Al-Shurman, S. M. Yoo and S. Park,(2004) Black Hole Attack in Mobile Ad Hoc Networks, In Proc. of the 42nd Annual Southeast Regional Conference (ACMSE’04), Huntsville, ALabama, USA, April 2004.
Qureshi, D. I. ., & Patil, M. S. S. . (2022). Secure Sensor Node-Based Fusion by Authentication Protocol Using Internet of Things and Rfid. Research Journal of Computer Systems and Engineering, 3(1), 48–55. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/41
W. Yu, Y. Sun and K. R. Liu,(2005) HADOF: Defense Against Routing Disruptions in Mobile Ad Hoc Networks, In Proc. of the 24th IEEE INFOCOM, Miami, USA, March 2005.
Marti, T. Giuli, K. Lai,and M. Baker,(2000) Mitigating Routing Misbehavior in Mobile Ad Hoc Networks, Proc. MobiCom, Aug. 2000.
L. Buttyan and J.-P. Hubaux, (2000)Enforcing Service Availability in Mobile Ad-Hoc WANs,? Proc. MobiHoc, Aug. 2000 .
L. Buttyan and J.-P. Hubaux, (2003) Stimulating Cooperation in Self- Organizing Mobile Ad Hoc Networks,? ACM/Kluwer Mobile Networks and Applications, vol. 8, no. 5, 2003.
S. Zhong, J. Chen, and Y.R. Yang, (2003)Sprite: A Simple, Cheat-Proof, Credit-Based System for Mobile Ad-Hoc Networks,? Proc. INFOCOM, Mar.-Apr. 2003.
S. Buchegger and J.-Y. Le Boudec, (2002)Performance Analysis of the CONFIDANT Protocol: Cooperation of Nodes, Fairness in Dynamic Ad-Hoc Networks,? Proc. MobiHoc, June 2002.
H. Miranda and L. Rodrigues, (2002)Preventing Selfishness in Open Mobile Ad Hoc Networks,? Proc. Seventh CaberNet Radicals Workshop, Oct. 2002.
V.-N. Padmanabhan and D.-R. Simon, (2003) Secure Traceroute to Detect Faulty or Malicious Routing, SIGCOMM Computer Comm. Rev., vol. 33, no. 1, Jan. 2003.
Y. Xue and K. Nahrstedt,(2004) Providing Fault-Tolerant Ad-Hoc Routing Service in Adversarial Environments,? Wireless Personal Comm., vol. 29, nos. 3-4, pp. 367-388, 2004.