Hybrid Cryptography and Steganography-Based Security System for IoT Networks
Main Article Content
Abstract
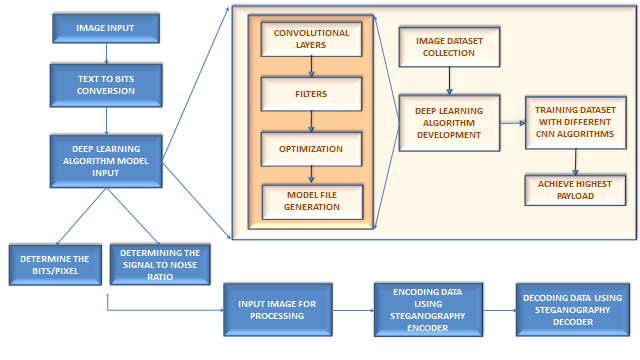
Despite the fact that many IoT devices are publicly accessible to everyone on the network, understanding the security risks and threats posed by cyber attacks is critical; as a result, it should be safeguarded. Plain text is constructed into encrypted text, before being delivered by using cryptography, and is then reconstructed back to plain text after receiving a response from the recipient. The steganography technique can be used to hide sensitive information incorporated in a text, audio, or video file. One approach is to hide data in bits that correspond to successive rows of pixels with the same color in an image file. As a consequence, the image file retains the original's appearance while also containing "noise" patterns made out of common, unencrypted data. To do this, the encrypted data is subtly applied to the redundant data. In this work, it is suggested that IoT network data be encrypted using cryptography, and that an encrypted message be concealed inside an image file using steganography. Additionally, it is suggested to enhance the number of bits that may be stored within a single picture pixel. The payload that may be sent through an image is significantly increased by incorporating Convolutional Neural Networks into the classic steganography technique. In this work, we propose, design, and train Convolutional Neural Networks (CNN) to enhance the amount of data that can be securely encrypted and decrypted to show the original message.
Article Details
References
S. Wu, S. -h. Zhong and Y. Liu, "A Novel Convolutional Neural Network for Image Steganalysis with Shared Normalization," in IEEE Transactions on Multimedia, vol. 22, no. 1, pp. 256-270, Jan. 2020, doi: 10.1109/TMM.2019.2920605.
M. Hassaballah, M. A. Hameed, A. I. Awad and K. Muhammad, "A Novel Image Steganography Method for Industrial Internet of Things Security," in IEEE Transactions on Industrial Informatics, vol. 17, no. 11, pp. 7743-7751, Nov. 2021, doi: 10.1109/TII.2021.3053595.
W. Su, J. Ni, X. Hu and J. Fridrich, "Image Steganography with Symmetric Embedding Using Gaussian Markov Random Field Model," in IEEE Transactions on Circuits and Systems for Video Technology, vol. 31, no. 3, pp. 1001-1015, March 2021, doi: 10.1109/TCSVT.2020.3001122.
M. Khari, A. K. Garg, A. H. Gandomi, R. Gupta, R. Patan and B. Balusamy, "Securing Data in Internet of Things (IoT) Using Cryptography and Steganography Techniques," in IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 50, no. 1, pp. 73-80, Jan. 2020, doi:10.1109/TSMC.2019.2903785.
M. Boroumand, M. Chen and J. Fridrich, "Deep Residual Network for Steganalysis of Digital Images," in IEEE Transactions on Information Forensics and Security, vol. 14, no. 5, pp. 1181-1193, May 2019, doi: 10.1109/TIFS.2018.2871749. [6] W. Wang, P. Xu, D. Liu, L.
T. Yang and Z. Yan, "Lightweighted Secure Searching Over Public-Key Ciphertexts for Edge-Cloud-Assisted Industrial IoT Devices," in IEEE Transactions on Industrial Informatics, vol. 16, no. 6, pp. 4221-4230, June 2020, doi: 10.1109/TII.2019.2950295.
W. Tang, B. Li, S. Tan, M. Barni and J. Huang, "CNN-Based Adversarial Embedding for Image Steganography," in IEEE Transactions on Information Forensics and Security, vol. 14, no. 8, pp. 2074-2087, Aug. 2019, doi: 10.1109/TIFS.2019.2891237.
X. Liao, J. Yin, M. Chen and Z. Qin, "Adaptive Payload Distribution in Multiple Images Steganography Based on Image Texture Features," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 2, pp. 897-911, 1 March-April 2022, doi: 10.1109/TDSC.2020.3004708.
B. Singh, A. Sur and P. Mitra, "Steganalysis of Digital Images Using Deep Fractal Network," in IEEE Transactions on Computational Social Systems, vol. 8, no. 3, pp. 599-606, June 2021, doi: 10.1109/TCSS.2021.3052520.