Hybrid Encryption of Cloud Processing With IOT Devices Using DNA And RSA Cryptography
Main Article Content
Abstract
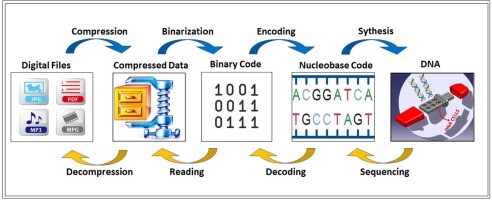
The research paper titled "Hybrid Data Encryption as well as Decryption Using Hybrid RSA and DNA" develops a hybrid cryptosystem by combining the usefulness of such an asymmetric-key (public-key) cryptosystem with the efficacy of a symmetric-key (private-key) cryptosystem. These two types of cryptosystems use different types of keys. The method addresses concerns regarding the users' right to privacy, authentication, and accuracy by utilizing a data encryption process that is secure in both directions. Both the process of encrypting data and the process of decrypting data, which are both utilized by the system, are two different encryption methods. It has been suggested that a hybrid encryption algorithm, which combines DNA and RSA, be used for file encryption in order to address the issues with efficiency and security. The results of the testing show that the RSA and DNA hybrid encryption algorithm is suitable for use. In this particular research project's hybrid encryption and decoding for cloud processing with IOT devices, the DNA and RSA algorithms were used.
Article Details
References
M. A. Iliyasu, O. A. Abisoye, S. A. Bashir, and J. A. Ojeniyi, “A review of DNA cryptograhic approaches,” Proc. 2020 IEEE 2nd Int. Conf. Cyberspace, CYBER Niger. 2020, pp. 66–72, 2021, doi: 10.1109/CYBERNIGERIA51635.2021.9428855.
T. Mandge and V. Choudhary, “A DNA encryption technique based on matrix manipulation and secure key generation scheme,” 2013 Int. Conf. Inf. Commun. Embed. Syst. ICICES 2013, pp. 47–52, 2013, doi: 10.1109/ICICES.2013.6508181.
G. Bhoi, R. Bhavsar, P. Prajapati, and P. Shah, “A review of recent trends on DNA based cryptography,” Proc. 3rd Int. Conf. Intell. Sustain. Syst. ICISS 2020, pp. 815–822, 2020, doi: 10.1109/ICISS49785.2020.9316013.
X. Zhou and X. Tang, “Research and implementation of RSA algorithm for encryption and decryption,” Proc. 6th Int. Forum Strateg. Technol. IFOST 2011, vol. 2, pp. 1118–1121, 2011, doi: 10.1109/IFOST.2011.6021216.
D. A. Zebari, H. Haron, S. R. M. Zeebaree, and D. Qader Zeebaree, “Multi-Level of DNA Encryption Technique Based on DNA Arithmetic and Biological Operations,” ICOASE 2018 - Int. Conf. Adv. Sci. Eng., pp. 312–317, 2018, doi: 10.1109/ICOASE.2018.8548824.
B. B. Raj and V. Ceronmani Sharmila, “An survey on DNA based cryptography,” 2018 Int. Conf. Emerg. Trends Innov. Eng. Technol. Res. ICETIETR 2018, pp. 1–3, 2018, doi: 10.1109/ICETIETR.2018.8529075.
F. J. Aufa, Endroyono, and A. Affandi, “Security System Analysis in Combination Method: RSA Encryption and Digital Signature Algorithm,” Proc. - 2018 4th Int. Conf. Sci. Technol. ICST 2018, vol. 1, pp. 1–5, 2018, doi: 10.1109/ICSTC.2018.8528584.
K. A. Fasila, “Automated DNA encryption algorithm based on UNICODE and colors,” Proc. 2017 2nd IEEE Int. Conf. Electr. Comput. Commun. Technol. ICECCT 2017, pp. 6–9, 2017, doi: 10.1109/ICECCT.2017.8117907.
S. Arunpandian and S. S. Dhenakaran, “DNA based Computing Encryption Scheme Blending Color and Gray Images,” Proc. 2020 IEEE Int. Conf. Commun. Signal Process. ICCSP 2020, pp. 966–970, 2020, doi: 10.1109/ICCSP48568.2020.9182195.
F. H. M. S. Al-Kadei, H. A. Mardan, and N. A. Minas, “Speed Up Image Encryption by Using RSA Algorithm,” 2020 6th Int. Conf. Adv. Comput. Commun. Syst. ICACCS 2020, pp. 1302–1307, 2020, doi: 10.1109/ICACCS48705.2020.9074430.
K. S. Sajisha and S. Mathew, “An encryption based on DNA cryptography and steganography,” Proc. Int. Conf. Electron. Commun. Aerosp. Technol. ICECA 2017, vol. 2017-January, pp. 162–167, 2017, doi: 10.1109/ICECA.2017.8212786.
M. M. Elamir, M. S. Mabrouk, and S. Y. marzouk, “Secure framework for IoT technology based on RSA and DNA cryptography,” Egypt. J. Med. Hum. Genet., vol. 23, no. 1, 2022, doi: 10.1186/s43042-022-00326-5.
R. Ahmad, S. Naz, M. Afzal, S. Rashid, M. Liwicki, and A. Dengel, “A Deep Learning based Arabic Script Recognition System?: Benchmark on KHAT,” vol. 17, no. 3, pp. 299–305, 2020.
P. Pavithran, S. Mathew, S. Namasudra, and P. Lorenz, “A novel cryptosystem based on DNA cryptography and randomly generated mealy machine,” Comput. Secur., vol. 104, p. 102160, 2021, doi: 10.1016/j.cose.2020.102160.
E. Vidhya and R. Rathipriya, “Key Generation for DNA Cryptography Using Genetic Operators and Diffie-Hellman Key Exchange Algorithm,” Int. J. Math. Comput. Sci., vol. 15, no. 4, pp. 1109–1115, 2020.
S. Chirakkarottu and S. Mathew, “A novel encryption method for medical images using 2D Zaslavski map and DNA cryptography,” SN Appl. Sci., vol. 2, no. 1, pp. 1–10, 2020, doi: 10.1007/s42452-019-1685-8.
R. Soni, A. Johar, and V. Soni, “An encryption and decryption algorithm for image based on DNA,” Proc. - 2013 Int. Conf. Commun. Syst. Netw. Technol. CSNT 2013, pp. 478–481, 2013, doi: 10.1109/CSNT.2013.105.
L. K. Galla, V. S. Koganti, and N. Nuthalapati, “Implementation of RSA,” 2016 Int. Conf. Control Instrum. Commun. Comput. Technol. ICCICCT 2016, pp. 81–87, 2017, doi: 10.1109/ICCICCT.2016.7987922.
M. Sabry, M. Hashem, T. Nazmy, and M. E. Khalifa, “Design of DNA-based Advanced Encryption Standard (AES),” 2015 IEEE 7th Int. Conf. Intell. Comput. Inf. Syst. ICICIS 2015, pp. 390–397, 2016, doi: 10.1109/IntelCIS.2015.7397250.
A. Jain and N. Rajpal, “Adaptive key length based encryption algorithm using DNA approach,” Proc. - 2013 Int. Conf. Mach. Intell. Res. Adv. ICMIRA 2013, no. 3, pp. 140–144, 2014, doi: 10.1109/ICMIRA.2013.34.