LCHAIN: A Secure Log Storage Mechanism using IPFS and Blockchain Technology
Main Article Content
Abstract
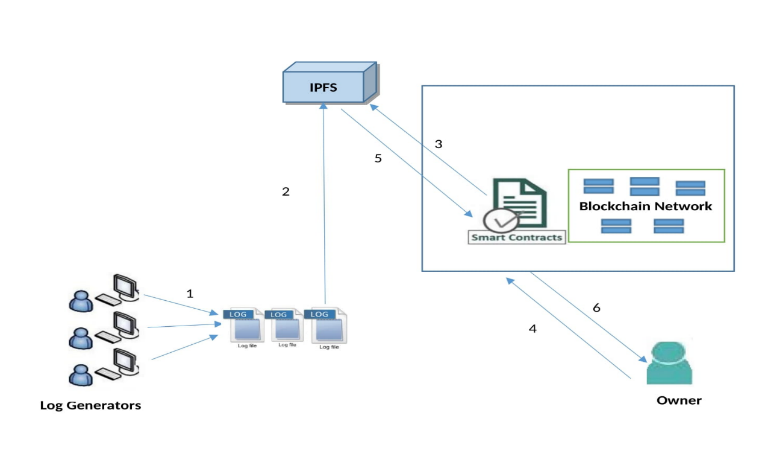
Data security is a very important and crucial part of Cloud storage. Day by day, thousands of operations function over the Cloud, verify logs generated from all transactions is very difficult. The attacker may temper or remove targeted logs or attack traces on the system with stealthy techniques. It is required to maintain the security of the log to trace back all the transactions to identify such tempering and loss of logs. Temper-proof log storage is a challenging issue on the Cloud. To overcome the issue, we propose strong and secure log storage using Blockchain technology and IPFS. Detecting log tempering and tracing is challenging due to large log volumes. We recommend the usage of Blockchain technology due to its inherent feature of immutability to address the issue of log tempering. We present LChain which provides immutable storage of logs with tracing. Blockchain technology helps yp create immutable logs but also offers non-repudiation and scalability. Smart contracts are used for efficient searching and enhancing computational power.
Article Details
References
J. Buric and D. Delija, "Challenges in network forensics," 2015 38th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, 2015, pp.1382-1386.
N. Virvilis, B. Vanautgaerden and O. S. Serrano, "Changing the game: The art of deceiving sophisticated attackers," 2014 6th International Conference On Cyber Conflict (CyCon 2014), Tallinn, 2014, pp. 87-97.
M. Sato and T. Yamauchi, “Vmm-based log-tampering and loss detection scheme,” Journal of Internet Technology, vol. 13, no. 4, pp. 655–666,2012.
R. T. Snodgrass, S. S. Yao, and C. Collberg, “Tamper detection in audit logs,” in Proceedings of the Thirtieth international conference on Very large data bases-Volume 30. VLDB Endowment, 2004, pp. 504–515.
Holt JE. Logcrypt: forward security and public verification for secure audit logs. Proceedings of the 4th Australasian workshops on grid computing and e¬research (ACSW '06), Tasmania, Australia, 2006; 203–211.
I. Ray, K. Belyaev, M. Strizhov, D. Mulamba and M. Rajaram, "SecureLogging as a Service—Delegating Log Management to the Cloud,"in IEEE Systems Journal, vol. 7, no. 2, pp. 323-334, June 2013.
Omar, Abdullah & Bhuiyan, Md & Basu, Anirban & Kiyomoto, Shinsaku & Rahman, Shahriar(2019). A privacy-friendly platform for healthcare data in Cloud based on Blockchain environment. Future Generation Computer Systems. 95C. 511-521. 10.1016/j.future.2018.12.044.
Dr. Manish Kumar, Ashish Kumar Singh, Dr. T V Suresh Kumar,( 2018)Secure Log Storage Using Blockchain and Cloud Infrastructure ,9th ICCCNT 2018, IISC, Bengaluru, India,IEEE’.
Ozdayi, M.S., Kantarcioglu, M. & Malin, B. Leveraging Blockchain for immutable logging and querying across multiple sites. BMC Med Genomics 13 (Suppl 7), 82 (2020). https://doi.org/10.1186/s12920-020-0721-2
W. Pourmajidi and A. Miranskyy, "Logchain: Blockchain-Assisted Log Storage," 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), 2018, pp. 978-982, doi: 10.1109/CLOUD.2018.00150.
W. Huang, "A Blockchain-Based Framework for Secure Log Storage," 2019 IEEE 2nd International Conference on Computer and Communication Engineering Technology (CCET), 2019, pp. 96-100, doi: 10.1109/CCET48361.2019.8989093.
H. Wang, D. Yang, N. Duan, Y. Guo and L. Zhang, "Medusa: Blockchain Powered Log Storage System," 2018 IEEE 9th International Conference on Software Engineering and Service Science (ICSESS), 2018, pp. 518-521, doi: 10.1109/ICSESS.2018.8663935.
S. Ali, G. Wang, B. White and R. L. Cottrell, "A Blockchain-Based Decentralized Data Storage and Access Framework for PingER," 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), 2018, pp. 1303-1308, doi: 10.1109/TrustCom/BigDataSE.2018.00179.
M. Castro, B. Liskov, Practical Byzantine fault tolerance and proactive recovery, ACM Transactions on Computer Systems (TOCS) 20 (4) (2002) 398–461.
Z. Zheng, S. Xie, H.-N. Dai, H. Wang, Blockchain challenges and opportunities: A survey, Work Pap.–2016 .
Jiaxing Li, Jigang Wu, Long Chen, Block-Secure: Blockchain Based Scheme for Secure P2P Cloud Storage, Information Sciences (2018), doi: 10.1016/j.ins.2018.06.071
Ilya Sukhodolskiy, Sergey Zapechnikov,A Blockchain-Based Access Control System for Cloud Storage,IEEE2018,978-1-5386-4340-2/18
Xue, Jingting & Xu, Chunxiang & Zhang, Yuan & Bai, Lanhua. (2018). DStore: A Distributed Cloud Storage System Based on Smart Contracts and Blockchain: 18th International Conference, ICA3PP 2018, Guangzhou, China, November 15-17, 2018, Proceedings, Part III. 10.1007/978-3-030-05057-3_30.
Xueping Liang, Sachin Shetty, Deepak Tosh, Charles Kamhoua, Kevin Kwiat, and Laurent Njilla,ProvChain: A Blockchain-based Data Provenance Architecture in Cloud Environment with Enhanced Privacy and Availability,2018 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing
S. Wang, X. Wang, and Y. Zhang, "A Secure Cloud Storage Framework With Access Control Based on Blockchain," in IEEE Access, vol. 7, pp. 112713-112725, 2019, doi: 10.1109/ACCESS.2019.2929205.
PengCheng Wei, Dahu Wang, Yu Zhao, Sumarga Kumar Sah Tyagi, Neeraj Kumar, Blockchain data-based Cloud data integrity protection mechanism, Future Generation Computer Systems, Volume 102,2020, Pages 902-911, ISSN 0167-739X,https://doi.org/10.1016/j.future.2019.09.028.
W. Pourmajidi and A. Miranskyy, “Logchain: Blockchain-Assisted Log Storage,” 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), 2018.
D. Yue, R. Li, Y. Zhang, W. Tian and C. Peng, "Blockchain Based Data Integrity Verification in P2P Cloud Storage," 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS), Singapore, Singapore, 2018, pp. 561-568.doi: 10.1109/PADSW.2018.8644863
Sutton A., Samavi R. (2017) Blockchain Enabled Privacy Audit Logs. In: d'Amato C. et al. (eds) The Semantic Web – ISWC 2017. ISWC 2017. Lecture Notes in Computer Science, vol 10587. Springer, Cham.
Xuanmei Qin, Yongfeng Huang, Zhen Yang, Xing Li, A Blockchain-based access control scheme with multiple attribute authorities for secure Cloud data sharing, Journal of Systems Architecture, Volume 112,2021,101854, ISSN 1383-7621,https://doi.org/10.1016/j.sysarc.2020.101854.
Smita Athanere, Ramesh Thakur, Blockchain based hierarchical semi-decentralized approach using IPFS for secure and efficient data sharing, Journal of King Saud University - Computer and Information Sciences,Volume 34, Issue 4,2022,Pages 1523-1534,https://doi.org/10.1016/j.jksuci.2022.01.019.