A Jamming Attacks Detection Approach Based on CNN based Quantum Leap Method for Wireless Sensor Network
Main Article Content
Abstract
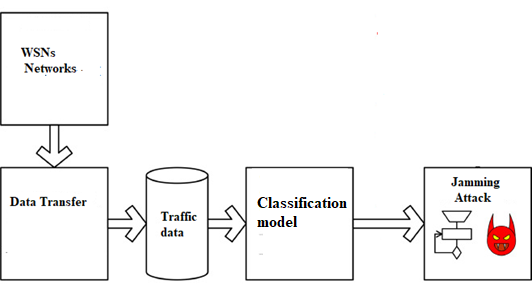
The wireless sensor network is the most significant largest communication device. WSN has been interfacing with various wireless applications. Because the wireless application needs faster communication and less interruption, the main problem of jamming attacks on wireless networks is that jamming attack detection using various machine learning methods has been used. The reasons for jamming detection may be user behaviour-based and network traffic and energy consumption. The previous machine learning system could not present the jamming attack detection accuracy because the feature selection model of Chi-Squared didn’t perform well for jamming attack detections which determined takes a large dataset to be classified to find the high accuracy for jamming attack detection. To resolve this problem, propose a CNN-based quantum leap method that detects high accuracy for jamming attack detections the WSN-DS dataset collected by the Kaggle repository. Pre-processing using the Z-score Normalization technique will be applied, performing data deviations and assessments from the dataset, and collecting data and checking or evaluating data. Fisher’s Score is used to select the optimal feature of a jamming attack. Finally, the proposed CNN-based quantum leap is used to classify the jamming attacks. The CNN-based quantum leap simulation shows the output for jamming attacks with high precision, high detection, and low false alarm detection.
Article Details
References
. Y. Li et al., "Jamming Detection and Classification in OFDM-Based UAVs via Feature- and Spectrogram-Tailored Machine Learning," in IEEE Access, vol. 10, pp. 16859-16870, 2022, doi: 10.1109/ACCESS.2022.3150020.
. S. Kumar, K. Singh, S. Kumar, O. Kaiwartya, Y. Cao and H. Zhou, "Delimitated Anti Jammer Scheme for Internet of Vehicle: Machine Learning Based Security Approach," in IEEE Access, vol. 7, pp. 113311-113323, 2019, doi: 10.1109/ACCESS.2019.2934632.
. B. Upadhyaya, S. Sun and B. Sikdar, "Multihypothesis Sequential Testing for Illegitimate Access and Collision-Based Attack Detection in Wireless IoT Networks," in IEEE Internet of Things Journal, vol. 8, no. 14, pp. 11705-11716, 15 July15, 2021, doi: 10.1109/JIOT.2021.3059880.
. M. Furdek, C. Natalino, F. Lipp, D. Hock, A. D. Giglio and M. Schiano, "Machine Learning for Optical Network Security Monitoring: A Practical Perspective," in Journal of Lightwave Technology, vol. 38, no. 11, pp. 2860-2871, 1 June1, 2020, doi: 10.1109/JLT.2020.2987032.
. L. Zhang, F. Restuccia, T. Melodia and S. M. Pudlewski, "Taming Cross-Layer Attacks in Wireless Networks: A Bayesian Learning Approach," in IEEE Transactions on Mobile Computing, vol. 18, no. 7, pp. 1688-1702, 1 July 2019, doi: 10.1109/TMC.2018.2864155.
. G. Kornaros, "Hardware-Assisted Machine Learning in Resource-Constrained IoT Environments for Security: Review and Future Prospective," in IEEE Access, vol. 10, pp. 58603-58622, 2022, doi: 10.1109/ACCESS.2022.3179047.
. Y. Yang, L. Wu, G. Yin, L. Li and H. Zhao, "A Survey on Security and Privacy Issues in Internet-of-Things," in IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1250-1258, Oct. 2017, doi: 10.1109/JIOT.2017.2694844.
. S. Liu, Y. Chen, W. Trappe and L. J. Greenstein, "ALDO: An Anomaly Detection Framework for Dynamic Spectrum Access Networks," IEEE INFOCOM 2009, Rio de Janeiro, Brazil, 2009, pp. 675-683, doi: 10.1109/INFCOM.2009.5061975.
. C. Chen, H. Cheng and Y. -D. Yao, "Cooperative Spectrum Sensing in Cognitive Radio Networks in the Presence of the Primary User Emulation Attack," in IEEE Transactions on Wireless Communications, vol. 10, no. 7, pp. 2135-2141, July 2011, doi: 10.1109/TWC.2011.041311.100626.
. F. Zhang, H. A. D. E. Kodituwakku, J. W. Hines and J. Coble, "Multilayer Data-Driven Cyber-Attack Detection System for Industrial Control Systems Based on Network, System, and Process Data," in IEEE Transactions on Industrial Informatics, vol. 15, no. 7, pp. 4362-4369, July 2019, doi: 10.1109/TII.2019.2891261.
. L. Zhang, G. Ding, Q. Wu and Z. Han, "Spectrum Sensing Under Spectrum Misuse Behaviors: A Multi-Hypothesis Test Perspective," in IEEE Transactions on Information Forensics and Security, vol. 13, no. 4, pp. 993-1007, April 2018, doi: 10.1109/TIFS.2017.2774770.
. G. Fragkiadakis, E. Z. Tragos and I. G. Askoxylakis, "A Survey on Security Threats and Detection Techniques in Cognitive Radio Networks," in IEEE Communications Surveys & Tutorials, vol. 15, no. 1, pp. 428-445, First Quarter 2013, doi: 10.1109/SURV.2011.122211.00162.
. Z. Yuan, D. Niyato, H. Li, J. B. Song and Z. Han, "Defeating Primary User Emulation Attacks Using Belief Propagation in Cognitive Radio Networks," in IEEE Journal on Selected Areas in Communications, vol. 30, no. 10, pp. 1850-1860, November 2012, doi: 10.1109/JSAC.2012.121102
. C. Sumathi, R. Vidhyapriya and C. Kiruthika, "A proactive elimination of Primary User Emulation Attack in cognitive radio networks using Intense Explore algorithm," 2015 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 2015, pp. 1-7, doi: 10.1109/ICCCI.2015.7218110.
. P. K. Niranjane, V. M. Wadhai, S. H. Rajput and J. B. Helonde, "Performance analysis of PUE attacker on Dynamic Spectrum access in cognitive radio," 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 2015, pp. 1-6, doi: 10.1109/PERVASIVE.2015.7086985.
. J. Yang, Y. Chen, W. Shi, X. Dong and T. Peng, "Cooperative spectrum sensing against attacks in cognitive radio networks," 2014 IEEE International Conference on Information and Automation (ICIA), Hailar, China, 2014, pp. 71-75, doi: 10.1109/ICInfA.2014.6932628.
. Ö. Cepheli and G. Karabulut Kurt, "Physical layer security in cognitive radio networks: A beamforming approach," 2013 First International Black Sea Conference on Communications and Networking (BlackSeaCom), Batumi, Georgia, 2013, pp. 233-237, doi: 10.1109/BlackSeaCom.2013.6623415.
. A Alahmadi, M. Abdelhakim, J. Ren and T. Li, "Defense Against Primary User Emulation Attacks in Cognitive Radio Networks Using Advanced Encryption Standard," in IEEE Transactions on Information Forensics and Security, vol. 9, no. 5, pp. 772-781, May 2014, doi: 10.1109/TIFS.2014.2310355.
. M. Thanu, "Detection of primary user emulation attacks in Cognitive Radio networks," 2012 International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 2012, pp. 605-608, doi: 10.1109/CTS.2012.6261113.
. G. Fragkiadakis, E. Z. Tragos and I. G. Askoxylakis, "A Survey on Security Threats and Detection Techniques in Cognitive Radio Networks," in IEEE Communications Surveys & Tutorials, vol. 15, no. 1, pp. 428-445, First Quarter 2013, doi: 10.1109/SURV.2011.122211.00162.
. Gopalakrishnan Subburayalu, Hemanand Duraivelu, Arun Prasath Raveendran, Rajesh Arunachalam, Deepika Kongara & Chitra Thangavel (2021) Cluster Based Malicious Node Detection System for Mobile Ad-Hoc Network Using ANFIS Classifier, Journal of Applied Security Research, DOI: 10.1080/19361610.2021.2002118.
. Gopalakrishnan, S. and Kumar, P. (2016) Performance Analysis of Malicious Node Detection and Elimination Using Clustering Approach on MANET. Circuits and Systems, 7, 748-758. doi: 10.4236/cs.2016.76064.
. D. Hemanand, G. . Reddy, S. S. . Babu, K. R. . Balmuri, T. Chitra, and S. Gopalakrishnan, “An Intelligent Intrusion Detection and Classification System using CSGO-LSVM Model for Wireless Sensor Networks (WSNs)”, Int J Intell Syst Appl Eng, vol. 10, no. 3, pp. 285–293, Oct. 2022.