Cooperative Self-Scheduling Secure Routing Protocol for Efficient Communication in MANET
Main Article Content
Abstract
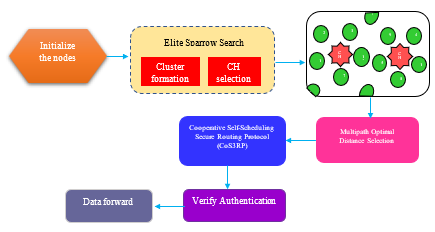
In wireless transmission, a Mobile Ad-hoc Network (MANET) contains many mobile nodes that can communicate without needing base stations. Due to the highly dynamic nature of wireless, MANETs face several issues, like malicious nodes making packet loss, high energy consumption, and security. Key challenges include efficient clustering and routing with optimal energy efficiency for Quality of Service (QoS) performance. To combat these issues, this novel presents Cooperative Self-Scheduling Secure Routing Protocol (CoS3RP) for efficient scheduling for proficient packet transmission in MANET. Initially, we used Elite Sparrow Search Algorithm (ESSA) for identifies the Cluster Head (CH) and form clusters. The Multipath Optimal Distance Selection (MODS) technique is used to find the multiple routes for data transmission. Afterward, the proposed CoS3RP transmits the packets based on each node authentication. The proposed method for evaluating and selecting efficient routing and data transfer paths is implemented using the Network simulator (NS2) tool, and the results are compared with other methods. Furthermore, the proposed well performs in routing performance, security, latency and throughput.
Article Details
References
H. Xia, Z. Li, Y. Zheng, A. Liu, Y. -J. Choi and H. Sekiya, "A Novel Light-Weight Subjective Trust Inference Framework in MANETs," in IEEE Transactions on Sustainable Computing, vol. 5, no. 2, pp. 236-248, 1 April-June 2020, doi: 10.1109/TSUSC.2018.2817219.
J. Tu, D. Tian and Y. Wang, "An Active-Routing Authentication Scheme in MANET," in IEEE Access, vol. 9, pp. 34276-34286, 2021, doi: 10.1109/ACCESS.2021.3054891.
M. Tahboush and M. Agoyi, "A Hybrid Wormhole Attack Detection in Mobile Ad-Hoc Network (MANET)," in IEEE Access, vol. 9, pp. 11872-11883, 2021, doi: 10.1109/ACCESS.2021.3051491.
B. U. I. Khan, F. Anwar, R. F. Olanrewaju, M. L. B. M. Kiah and R. N. Mir, "Game Theory Analysis and Modeling of Sophisticated Multi-Collusion Attack in MANETs," in IEEE Access, vol. 9, pp. 61778-61792, 2021, doi: 10.1109/ACCESS.2021.3073343.
A.M. El-Semary and H. Diab, "BP-AODV: Blackhole Protected AODV Routing Protocol for MANETs Based on Chaotic Map," in IEEE Access, vol. 7, pp. 95197-95211, 2019, doi: 10.1109/ACCESS.2019.2928804.
R. J. Cai, X. J. Li and P. H. J. Chong, "An Evolutionary Self-Cooperative Trust Scheme Against Routing Disruptions in MANETs," in IEEE Transactions on Mobile Computing, vol. 18, no. 1, pp. 42-55, 1 Jan. 2019, doi: 10.1109/TMC.2018.2828814.
Jain Andy B. Buksh, "Solutions for secure routing in mobile ad hoc network (MANET): A survey", Imperial Journal of Interdisciplinary Research, vol. 2, no. 4, pp. 5-8, 2016.
M. Abdan and S. A. H. Seno, "Machine Learning Methods for Intrusive Detection of Wormhole Attack in Mobile Ad Hoc Network (MANET)", Wirel. Commun. Mob. Comput., vol. 2022, pp. e2375702, janv. 2022.
G. Farahani, "Black Hole Attack Detection Using K-Nearest Neighbor Algorithm and Reputation Calculation in Mobile Ad Hoc Networks", Secur. Commun. Netw., vol. 2021, pp. e8814141, 2021.
S. Gurung and S. Chauhan, "Performance analysis of black-hole attack mitigation protocols under gray-hole attacks in MANET", Wirel. Netw., vol. 25, no. 3, pp. 975-988, 2019.
N. Veeraiah et al., "Trust Aware Secure Energy Efficient Hybrid Protocol for MANET," in IEEE Access, vol. 9, pp. 120996-121005, 2021, doi: 10.1109/ACCESS.2021.3108807.
U. Srilakshmi, N. Veeraiah, Y. Alotaibi, S. A. Alghamdi, O. I. Khalaf and B. V. Subbayamma, "An Improved Hybrid Secure Multipath Routing Protocol for MANET," in IEEE Access, vol. 9, pp. 163043-163053, 2021, doi: 10.1109/ACCESS.2021.3133882.
K. S. Sankaran, N. Vasudevan, K. R. Devabalaji, T. S. Babu, H. H. Alhelou and T. Yuvaraj, "A Recurrent Reward Based Learning Technique for Secure Neighbor Selection in Mobile AD-HOC Networks," in IEEE Access, vol. 9, pp. 21735-21745, 2021, doi: 10.1109/ACCESS.2021.3055422.
I. Zografopoulos and C. Konstantinou, "Detection of Malicious Attacks in Autonomous Cyber-Physical Inverter-Based Microgrids," in IEEE Transactions on Industrial Informatics, vol. 18, no. 9, pp. 5815-5826, Sept. 2022, doi: 10.1109/TII.2021.3132131.
U. Srilakshmi, S. A. Alghamdi, V. A. Vuyyuru, N. Veeraiah and Y. Alotaibi, "A Secure Optimization Routing Algorithm for Mobile Ad Hoc Networks," in IEEE Access, vol. 10, pp. 14260-14269, 2022, doi: 10.1109/ACCESS.2022.3144679.
A. M. El-Semary and H. Diab, "BP-AODV: Blackhole Protected AODV Routing Protocol for MANETs Based on Chaotic Map," in IEEE Access, vol. 7, pp. 95197-95211, 2019, doi: 10.1109/ACCESS.2019.2928804.
X. Wang, P. Zhang, Y. Du and M. Qi, "Trust Routing Protocol Based on Cloud-Based Fuzzy Petri Net and Trust Entropy for Mobile Ad hoc Network," in IEEE Access, vol. 8, pp. 47675-47693, 2020, doi: 10.1109/ACCESS.2020.2978143.
N. Veeraiah and B. T. Krishna, "An approach for optimal-secure multi-path routing and intrusion detection in MANET" in Evolutionary Intelligence, Berlin, Germany:Springer, pp. 1-15, Mar. 2020.
M. Naseem, G. Ahamad, S. Sharma and E. Abbasi, "EE-LB-AOMDV: An efficient energy constraints-based load-balanced multipath routing protocol for MANETs", Int. J. Commun. Syst., vol. 34, no. 16, 2021.
G. M. Borkar and A. R. Mahajan, "A secure and trust based on-demand multipath routing scheme for self-organized mobile ad-hoc networks", Wireless Netw., vol. 23, no. 8, pp. 2455-2472, Nov. 2017.
R. Prasad and P. S. Shankar, "Efficient performance analysis of energy aware on demand routing protocol in mobile ad-hoc network", Eng. Rep., vol. 2, no. 3, 2020.
S. V. Kumar and V. Anuratha, "Energy efficient routing for MANET using optimized hierarchical routing algorithm (Ee-Ohra)", Int. J. Sci. Technol. Res., vol. 9, no. 2, pp. 2157-2162, Feb. 2020.
M. Sirajuddin, C. H. Rupa, C. Iwendi and C. Biamba, "TBSMR: A trust-based secure multipath routing protocol for enhancing the QoS of the mobile ad hoc network", Secur. Commun. Netw., vol. 2021, Apr. 2021.
T. V. S. Kumar and D. P. G. Benakop, "A secure routing protocol for MANET using neighbor node discovery and multi detection routing protocol", Int. J. Eng. Trends Technol., vol. 68, no. 7, pp. 50-55, 2020.
C. Ran, S. Yan, L. Huang and L. Zhang, "An improved AODV routing security algorithm based on blockchain technology in ad hoc network", EURASIP J. Wireless Commun. Netw., vol. 2021, no. 1, pp. 1-16, 2021.
O. Singh, J. Singh and R. Singh, "Multi-level trust based intelligence intrusion detection system to detect the malicious nodes using elliptic curve cryptography in MANET", Cluster Comput., vol. 21, no. 1, pp. 51-63, Mar. 2018.
Z. Ali Zardari, J. He, N. Zhu, K. Mohammadani, M. Pathan, M. Hussain, et al., "A dual attack detection technique to identify black and gray hole attacks using an intrusion detection system and a connected dominating set in MANETs", Future Internet, vol. 11, no. 3, pp. 61, Mar. 2019.
S. Sankara Narayanan and G. Murugaboopathi, "Modified secure AODV protocol to prevent wormhole attack in MANET", Concurrency Comput. Pract. Exper., vol. 32, no. 4, Feb. 2020.
A. Mallikarjuna and V. C. Patil, "PUSR: Position update secure routing protocol for MANET", Int. J. Intell. Eng. Syst., vol. 14, no. 1, pp. 93-102, Feb. 2021.
Deepika Kukreja, S.K Dhurandher and B.V.R Reddy, "Power aware malicious nodes detection (PAMDS) for securing MANETs against packet forwarding misbehaviour attack", Journal of Ambient Intelligence and Humanized Computing, August 2018.
P. Satyanarayana, U. D. Yalavarthi, Y. S. S. Sriramam, M. Arun, V. G. Krishnan and S. Gopalakrishnan, "Implementation of Enhanced Energy Aware Clustering Based Routing (EEACBR)Algorithm to Improve Network Lifetime in WSN’s," 2022 IEEE 2nd International Conference on Mobile Networks and Wireless Communications (ICMNWC), Tumkur, Karnataka, India, 2022, pp. 1-6, 2022.
P. Satyanarayana, G. Diwakar, B.V. Subbayamma, N.V. Phani Sai Kumar, M. Arun, S. Gopalakrishnan, Comparative analysis of new meta-heuristic-variants for privacy preservation in wireless mobile adhoc networks for IoT applications, Computer Communications, vol.198, 2023.
Gopalakrishnan Subburayalu, Hemanand Duraivelu, Arun Prasath Raveendran, Rajesh Arunachalam, Deepika Kongara & Chitra Thangavel (2021) Cluster Based Malicious Node Detection System for Mobile Ad-Hoc Network Using ANFIS Classifier, Journal of Applied Security Research, 2021.