Data Security and Anonymization in Neighborhood Attacks in Clustered Network in Internet of Things (NIoT)
Main Article Content
Abstract
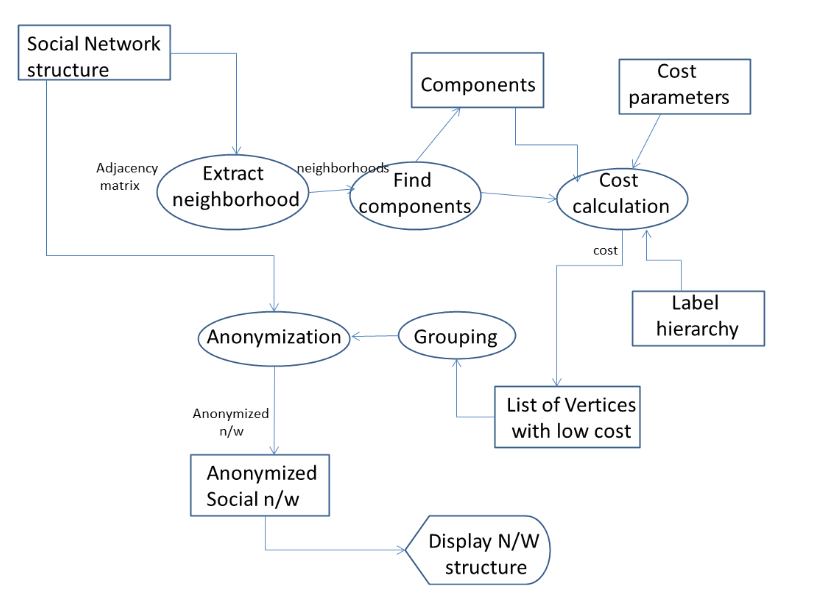
In this paper author tries to focus on the review on the K Nearest Neighbor (KNN) tied by one or more specific types of inter dependency, such as values, visions, ideas, financial exchange, friendship, conflict, or trade. Social network analysis views social relationships in terms of nodes and ties. It also focuses the network analysis, application as well as problem statement. In this paper presents a outline for the privacy hazard and sharing the anonymized data in the network. This includes a proposed architecture design flow, for which the author considers the several variations and make connections. On several real-world social networks, we show that simple anonymization techniques are inadequate, it results in considerable breaks of privacy for even modestly informed opponents. It also concentrates on a new anonymization technique. It based on the network and validate analytically that leads to saving of the privacy threat. It also analyses the effect that anonymizing the network has on the utility of the data for social network analysis.
Article Details
References
Machanavajjhala et al., “L-diversity: Privacy beyond k-anonymity,” in ICDE’06.
Bin Zhou and Jian Pei,” Preserving privacy in Social networks against neighbourhood Attacks” Simon Fraser University, IEEE 2008.
Mohsen Jamali and Hassan Abolhassani, “Different aspects of Social network analysis” in IEEE/ACM/WIC 2006.
L. Getoor and C. P. Diehl, “Link mining: a survey,” ACM SIGKDD Explorations Newsletter, vol. 7, no. 2, pp. 3–12, 2005.
L. Adamic and E. Adar, “How to search a social network,” Social Networks, vol. 27, no. 3, pp. 187–203, July 2005.
D.-W. Wang et al., “Privacy protection in social network data disclosure based on granular computing,” in Proceedings of the 2006 IEEE International Conference on Fuzzy Systems, 2006, pp. 997–1003.
M. Hay et al., “Anonymizing social networks,” University of Massachusetts Amherst, Tech. Rep. 07-19, 2007.
P. Samarati, “Protecting respondents’ identities in microdata release,” IEEE Transactions on Knowledge and Data Engineering, vol. 13, no. 6, pp. 1010–1027, 2001.
P. Samarati and L. Sweeney, “Generalizing data to provide anonymity when disclosing information,” in PODS’98.
X. Xiao and Y. Tao, “Personalized privacy preservation,” in SIGMOD’06.
S. Wasserman and K. Faust, Social Network Analysis. Cambridge University Press, 1994.
L. Backstrom et al., “Wherefore art thou r3579x?: anonymized social networks, hidden patterns, and structural steganography,” in WWW’07.
G. Kossinets and D. J. Watts, “Empirical analysis of an evolving social network,” Science, vol. 311, no. 5757, pp. 88–90, January 2006.
L. Backstrom et al., “Group formation in large social networks: membership, growth, and evolution,” in KDD’06.
R. Kumar et al., “Structure and evolution of online social networks,” in KDD’06.
L. Sweeney, “K-anonymity: a model for protecting privacy,” International Journal on uncertainty, Fuzziness and Knowledge-based System, vol. 10, no. 5, pp. 557–570, 2002.
M. Faloutsos et al., “On power-law relationships of the internet topology,” in SIGCOMM’99.
J. Xu et al., “Utility-based anonymization using local recoding,” in KDD’06.
Jonathan Green, Jayellen, “ Graph theory and its applications”, chp 2, pp 48-8, 2006.