A Security Model for the Classification of Suspicious Data Using Machine Learning Techniques
Main Article Content
Abstract
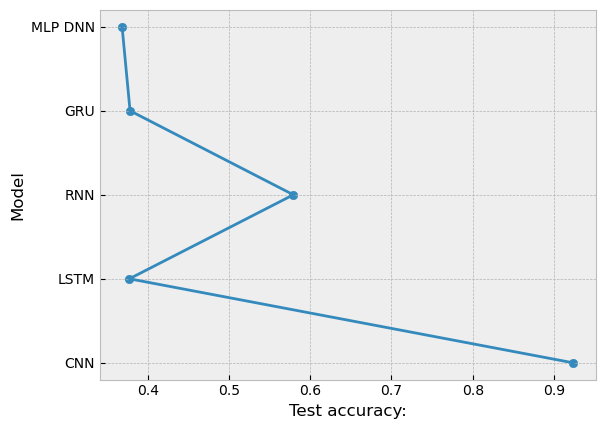
Cybercrime first emerged in 1981 and gained significant attention in the 20th century. The proliferation of technology and our increasing reliance on the internet have been major factors contributing to the growth of cybercrime. Different countries face varying types and levels of cyber-attacks, with developing countries often dealing with different types of attacks compared to developed countries. The response to cybercrime is usually based on the resources and technological capabilities available in each country. For example, sophisticated attacks involving machine learning may not be common in countries with limited technological advancements. Despite the variations in technology and resources, cybercrime remains a costly issue worldwide, projected to reach around 8 trillion by 2023. Preventing and combating cybercrime has become crucial in our society. Machine learning techniques, such as convolutional neural networks (CNN), recurrent neural networks (RNN), and more, have gained popularity in the fight against cybercrime. Researchers and authors have made significant contributions in protecting and predicting cybercrime. Nowadays, many corporations implement cyber defense strategies based on machine learning to safeguard their data. In this study, we utilized five different machine learning algorithms, including CNN, LSTM, RNN, GRU, and MLP DNN, to address cybercrime. The models were trained and tested using the InSDN public dataset. Each model provided different levels of trained and test accuracy percentages.
Article Details
References
Mughaid A, AlZu’bi S, Hnaif A, Taamneh S, Alnajjar A, Elsoud EA. An intelligent cyber security phishing detection system using deep learning techniques. Cluster Computing. 2022 Dec;25(6):3819-28.
Arshey M, Viji KA. Thwarting cyber crime and phishing attacks with machine learning: a study. In2021 7th international conference on advanced computing and communication systems (ICACCS) 2021 Mar 19 (Vol. 1, pp. 353-357). IEEE.
Crime Prediction Using Machine Learning and Deep Learning: A Systematic Review and Future Directions
Bilen A, Özer AB. Cyber-attack method and perpetrator prediction using machine learning algorithms. PeerJ Computer Science. 2021 Apr 9;7:e475.
Saeed RM, Abdulmohsin HA. A study on predicting crime rates through machine learning and data mining using text. Journal of Intelligent Systems. 2023 Mar 31;32(1):20220223.
Lazar D, Cohen K, Freund A, Bartik A, Ron A. IMDoC: identification of malicious domain campaigns via DNS and communicating files. IEEE Access. 2021 Mar 18;9:45242-58.
Simonthomas S, Subramanian R. Detection and Prevention of Cyber-Attacks in Cyber-Physical Systems based on Nature Inspired Algorithm. In2023 International Conference on Intelligent Systems for Communication, IoT and Security (ICISCoIS) 2023 Feb 9 (pp. 483-487). IEEE.
Vinayakumar R, Alazab M, Soman KP, Poornachandran P, Al-Nemrat A, Venkatraman S. Deep learning approach for intelligent intrusion detection system. Ieee Access. 2019 Apr 3;7:41525-50.
Yuan J, Chen G, Tian S, Pei X. Malicious URL detection based on a parallel neural joint model. IEEE Access. 2021 Jan 6;9:9464-72.
Karim A, Shahroz M, Mustofa K, Belhaouari SB, Joga SR. Phishing Detection System Through Hybrid Machine Learning Based on URL. IEEE Access. 2023 Mar 3;11:36805-22.
Nicholls J, Kuppa A, Le-Khac NA. Financial cybercrime: A comprehensive survey of deep learning approaches to tackle the evolving financial crime landscape. Ieee Access. 2021 Dec 8;9:163965-86.
Lekha KC, Prakasam S. Data mining techniques in detecting and predicting cyber crimes in banking sector. In2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS) 2017 Aug 1 (pp. 1639-1643). IEEE.
Sanni ML, Akinyemi BO, Akinwuyi D, Olajubu EA, Aderounmu GA. A Predictive Cyber Threat Model for Mobile Money Services. Annals of Emerging Technologies in Computing (AETiC). 2023 Jan 1;7(1):40-60.
Biswas A, Deol RS, Jha BK, Jakka G, Suguna MR, Thomson BI. Automated Banking Fraud Detection for Identification and Restriction of Unauthorised Access in Financial Sector. In2022 3rd International Conference on Smart Electronics and Communication (ICOSEC) 2022 Oct 20 (pp. 809-814). IEEE.
Shaukat K, Luo S, Chen S, Liu D. Cyber threat detection using machine learning techniques: A performance evaluation perspective. In2020 international conference on cyber warfare and security (ICCWS) 2020 Oct 20 (pp. 1-6). IEEE.
Rookard C, Khojandi A. Applying Deep Reinforcement Learning for Detection of Internet-of-Things Cyber Attacks. In2023 IEEE 13th Annual Computing and Communication Workshop and Conference (CCWC) 2023 Mar 8 (pp. 0389-0395). IEEE.
Rahman MA, Al-Saggaf Y, Zia T. A data mining framework to predict cyber attack for cyber security. In2020 15th IEEE Conference on Industrial Electronics and Applications (ICIEA) 2020 Nov 9 (pp. 207-212). IEEE.
Tuor A, Kaplan S, Hutchinson B, Nichols N, Robinson S. Deep learning for unsupervised insider threat detection in structured cybersecurity data streams. arXiv preprint arXiv:1710.00811. 2017 Oct 2.
Barik K, Misra S, Konar K, Fernandez-Sanz L, Koyuncu M. Cybersecurity deep: approaches, attacks dataset, and comparative study. Applied Artificial Intelligence. 2022 Dec 31;36(1):2055399.