Security Issues in Service Model of Fog Computing Environment
Main Article Content
Abstract
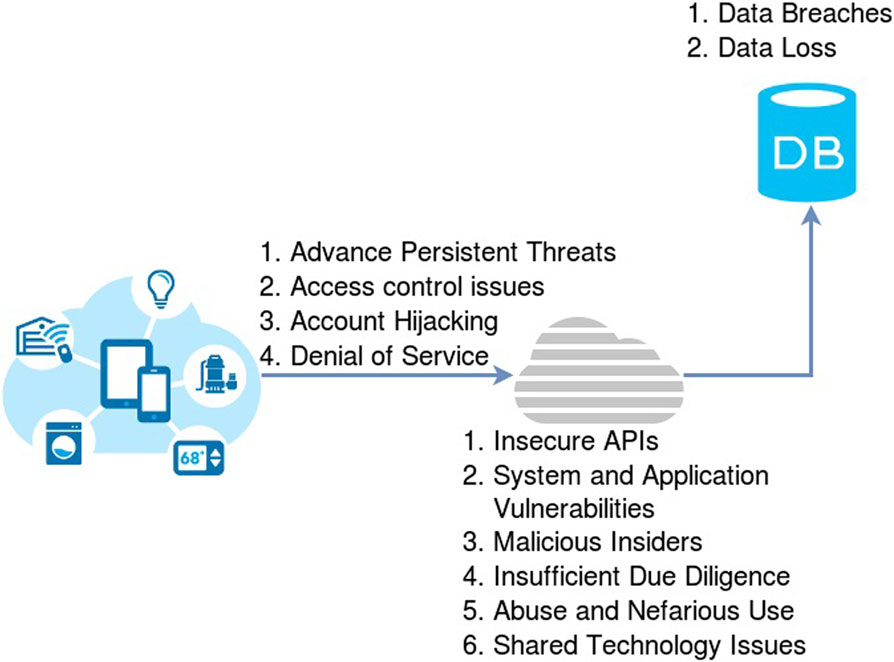
Fog computing is an innovative way to expand the cloud platform by providing computing resources. The platform is a cloud that has the same data, management, storage and application features, but their origins are different because they are deployed to different locations. The platform system can retrieve a large amount, work in the field, be fully loaded, and mount on a variety of hardware devices. With this utility, Fog Framework is perfect for applications and critical moments. Fog computing is similar to cloud computing, but because of its variability, creates new security and privacy challenges that go beyond what is common for fog nodes. This paper aims to understand the impact of security problems and how to overcome them, and to provide future safety guidance for those responsible for building, upgrading and maintaining fog systems.
Article Details
References
Z. Wen, R. Yang, P. Garraghan, P., T. Lin, J. Xu, and M. Rovatsos, “Fog orchestration for the Internet of things services,” IEEE Internet Computing”., vol. 21, no. 2, pp. 16–24, 2017.
A. Al-fuqaha, M. Guizani, M. Mohammadi, M. Aledhari, and M. Ayyash, “Internet of Things?: A Survey on Enabling Internet of Things?: A Survey on Enabling Technologies, Protocols, and Applications”, IEEE communications surveys & tutorials vol.17, no. 4, pp.2347–2376, 2015.
F. Bonomi, R. Milito, J. Zhu, and S. Addepalli, “Fog computing and its role in the internet of things,” in MCC ’12: Proceedings of of the MCC workshop on Mobile cloud computing, pp. 13–16, 2012.
Ayesha Mariyam, SK. Althaf Hussain Basha, S.Viswanadha Raju. (2023). Long Document Classification using Hierarchical Attention Networks. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 343 –. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2708
Krishna, B. Hari, et al. "Security Issues In Service Model Of Cloud Computing Environment." Procedia Computer Science 87 (2016): 246-251.
S. N. Gollaprolu Harish, B. Harish, and M. Shaik, “A Review on Fog Computing and its Applications,” Int. J. Innov. Technol. Explore. Eng., vol. 8, no. 6, pp. 358-369, 2019.
X. Xu., Fu, S., Cai, Q., Tian, W., Liu, W., Dou, W., & Liu, A. X.,”.Dynamic resource allocation for load balancing in fog environment”. Wireless Communications and Mobile Computing, pp. 1–15, 2018.
Mr. Kaustubh Patil. (2013). Optimization of Classified Satellite Images using DWT and Fuzzy Logic. International Journal of New Practices in Management and Engineering, 2(02), 08 - 12. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/15
Bommala, H., Kiran, S., Pujitha, M., & Reddy, R. P. K. (2019). Performance of Evaluation for AES with ECC in Cloud Environment. International Journal of Advanced Networking and Applications, 10(5), 4019-4025.
Chiang and T. Zhang, “Fog and IoT: An Overview of Research Opportunities,” IEEE Internet Things J., vol. 3, no. 6, pp. 854–864, 2016.
P. Hu, S. Dhelim, H. Ning, and T. Qiu, “Survey on fog computing: architecture, key technologies, applications, and open issues,” J. Netw. Comput. Appl., vol. 98, pp. 27–42,2017.
Harikrishna, B., Kiran, S., & Deep, K. M. (2018). Network as a service model in cloud authentication by HMAC algorithm. International Journal of Advanced Networking and Applications, 9(6), 3623-3631.
W. Jiafu, “Fog computing for energy-aware load balancing and scheduling in smart factory." IEEE Transactions on Industrial Informatics, vol. 14, pp. 4548-4556,2018.
Bommala, H., Kiran, S., Deep, K. M., &Babu, V. S. (2019). Client Authentication as a Service in Microsoft Azure. International Journal of Engineering and Advanced Technology (IJEAT), 8.
S. Agarwal, S. Yadav, and A. K. Yadav, “An architecture for elastic resource allocation in Fog computing,” Int. J. Comput. Sci. Commun., vol. 6, no. 2, pp. 201–207, 2016.
Bommala, Harikrishna, and S. Kiran. "Sensitive Information Security in Network as a Service Model in Cloud-IPSec." International Conference on Emerging Trends in Engineering. Springer, Cham, 2019.
R. Deng, R. Lu, C. Lai, T. H. Luan, and H. Liang, “Optimal workload allocation in fog- cloud computing toward balanced delay and power consumption,” IEEE Internet Things J., vol. 3, no. 6, pp. 1171–1181, 2016.
L. F. Bittencourt, D.-M. J., R. Buyya, O. F. Rana, and M. Parashar, “Mobility-aware application scheduling in fog computing,” IEEE Cloud Comput., vol. 4, no. 2, pp. 26–35,2017.
Jones, D., Taylor, M., García, L., Rodriguez, A., & Fernández, C. Using Machine Learning to Improve Student Performance in Engineering Programs. Kuwait Journal of Machine Learning, 1(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/101
Bommala,Harikrishna, et al. "Survey on Machine Learning with Cloud Technology Preserving Privacy: Risks and Keys." Solid State Technology 64.2 (2021): 3135-3150.
S. K. Mishra, D. Putha, J. J. Rodrigues, B. Sahoo, and E. Dutkiewicz, “Sustainable ServiceAllocationusing Metaheuristic Technique in Fog Server for Industrial Applications,” IEEE Trans. Ind. Informatics, vol. 14, no. 10, pp. 4497–4506, 2018.
Sahoo, D. K. . (2022). A Novel Method to Improve the Detection of Glaucoma Disease Using Machine Learning. Research Journal of Computer Systems and Engineering, 3(1), 67–72. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/44
R. Mahmud, R. Kotagiri, and R. Buyya, “Fog computing: A taxonomy, survey, and future directions,” in the Internet of everything, Singapore: Springer, pp. 103–130,2018.
X. Q. Redowan Mahmud, KotagiriRamamohanarao, RajkumarBuyya, “Latency-aware Application Module Management for Fog Computing Environments”, ACM Transactions on Embedded Computing Systems, vol. 9, no. 4, pp. 1-21.2018.
Pham and E. N. Huh, “Towards task scheduling in a cloud-fog computing system.,” in 18th Asia-Pacific network operations and management symposium, pp. 1–4, 2016.
X. Masip-Bruin, E. Marín-Tordera, A. Alonso, and J. Garcia, “Fog-to-cloud computing (F2C): The key technology enabler for dependable e-health services deployment,” in 2016 Mediterranean ad hoc networking workshop (Med-Hoc-Net), pp. 1–5, 2016.