An Optimized Node Level Lightweight Security Algorithm for Cloud Assisted-IoT
Main Article Content
Abstract
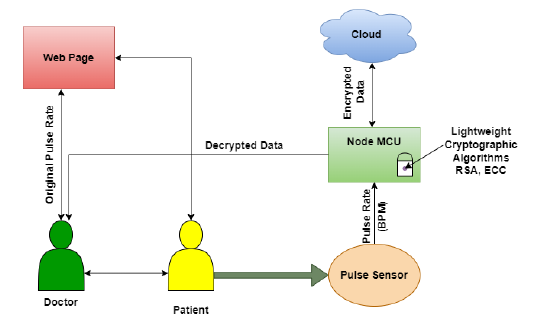
The fastest-evolving technology, the Internet of Things (IoT), will advance the fields of agriculture, defense, and medical electronics. IoT is focused on giving every object a purpose. IoT with cloud assistance offers a potential remedy for the issue of data expansion for individual objects with restricted capabilities. With the increasing use of cloud technology, the Internet of Things (IoT) has encountered additional security hurdles when it comes to exchanging data between two parties. To address this issue, a thorough investigation was conducted into a secure cloud-assisted strategy for managing IoT data, which ensures the safety of data during its collection, storage, and retrieval via the cloud, while also considering the growing number of users. To achieve this, a lightweight security mechanism that is optimized at the node level is implemented in the proposed system. By utilizing our technology, a secure IoT infrastructure can be established to prevent the majority of data confidentiality threats posed by both insiders and outsiders. Using a heartbeat sensor and a node MCU, we create a heartbeat monitoring system. At the node MCU level, giving security to the patient's health data and preventing unauthorized users from attacking it. Smaller key sizes and lightweight security techniques for IoT devices with minimal power, lower power and memory consumption and Execution time, transmission capacity reserve is used to achieve security. In order to achieve this. The performance of the RSA and ECC algorithms in terms of execution time, power consumption, and memory use have been tabulated for this experimental arrangement. The ECC method occurs to produce the best results in tiny devices.
Article Details
References
R. K. Kodali and A. Naikoti, ?ECDH based security model for IoT using ESP8266, ?2016 International Conference on Control Instrumentation, Communication and Computational Technologies (ICCICCT), 2016, bpp, 629-633,10.1109/ ICCICCT.2016.7988026.
Goyal, Tarun & Sahula, Vineet. (2016). Lightweight security algorithm for low power IoTdevices.17251729.10.1109/ICACCI.2016.773 2296.
Koblitz, Neal. ?Elliptic curve cryptosystems.? Mathematics of Computation 48 (1987): 203-209.
Rao, M. N. . (2023). A Comparative Analysis of Deep Learning Frameworks and Libraries. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 337–342. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2707
Rajesh, Sreeja & Paul, Varghese & Menon,Varun & Khosravi, Mohammad. (2019). A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry. 11. 293. 10.3390/sym11020293.
V. S. Mahalle and A. K. Shahade, "Enhancing the data security in Cloud by implementing hybrid (Rsa & Aes) encryption algorithm," 2014 International Conference on Power, Automation and Communication (INPAC),2014, pp.146-149, doi:10.1109/INPAC.2014.6981152.
J. Arora, Gagandeep, A. Singh, N. P. Singh, S. S.S. Rawat and G. Singh, "Heartbeat rate monitoring system by pulse technique using HB sensor," International Conference on Information Communication and Embedded Systems (ICICES2014), 2014, pp.1-5, doi: 10.1109/ICICES.2014.7033986.
Skarmeta A., Moreno M.V. (2014) Internet of Things. In: Jonker W., Petkovi? M. (eds) Secure Data Management. SDM 2013. Lecture Notes in ComputerScience, Vol 8425. Springer, Cham. https://doi.org/10.1007/978-3-319-06811-4_10
M. Frustaci, P. Pace, G. Aloi and G. Fortino, "Evaluating Critical Security Issues of the IoT World: Present and Future Challenges," in IEEE Internet of Things Journal, vol. 5, no. 4, pp. 2483-2495, Aug. 2018, doi: 10.1109/JIOT.2017.2767291.
Y. Li, W. Dai, Z. Ming and M. Qiu, "Privacy Protection for Preventing Data Over-Collection in Smart City," in IEEE Transactions on Computers, vol. 65, no. 5, pp.1339-1350, 1 May 2016, doi: 10.1109/TC.2015.2470247.
Shubhangi Verma et at., ?Strong Authentication policy for cloud computing environment using Modified Kerberos authentication protocol?,IJTA 9 (2): 227-231(2017).
Evaluation of Cryptographic Algorithms on Low Power Devices used in Smart City Muneer Ahmad Dar Scientist-C, National Institute of Electronics and Information Technology (NIELIT) Srinagar, (J&K), India. (Corresponding author: Muneer Ahmad Dar) (Received 29 September 2020, Revised 13 November 2020, Accepted 03 December 2020) (Published by Research Trend, Website: www.researchtrend.net).
Mr. S. Sumahasan and Dr. D. Rajyalakshmi, "Privacy preserving Cloud storage in Medical IoT using Hybrid cryptography Algorithm," Solid State Technology, Vol. 64 No. 2 (2021).
D. Maimut and R. Reyhanitabar, "Authenticated Encryption:TowardNext-Generation Algorithms," in IEEE Security & Privacy, vol. 12, no. 2, pp. 70-72, Mar.-Apr. 2014, doi: 10.1109/MSP.2014.19.
Kutalmis Akpinar and Kien A. Hua and Kai, LiAkpinar2015ThingStoreAP,?ThingStore: a platform forinternet-of-things application development and deployment?.Journal- Proceedings of the 9th ACM International Conference on Distributed Event-Based Systems in Year 2015.
Financial Cryptography and Data Security, 2014, Volume 8437 ISBN: 978-3-662-45471-8 Jopp W.Bos, J. Ale Halderman, NadiaHeninger, Jonathan Moore, MichaelNaehrig, EricWustrow.
Xian ping Wu, O. Dan dash and Phu Dung Le, "The Design and Implementation of a Smartphone Payment System based on Limited- used Key Generation Scheme," Third International Conference on Information Technology: New Generations (ITNG'06), 2006, pp. 458-463, doi: 10.1109/ITNG.2006.128.
Xiaoyong Zhou et al., "Identity, location, disease and more: inferring your secrets from android public resources",CCS '13: Proceedings of the 2013.ACM SIGSAC conference on Computer & communications security.
Farhan, Syed & Zaidi, Syed Farhan & Munam, Ali & Shah, Munam & Kamran, Muhammad & Javaid, Qaisar & Zhang, Sijing. (2016). A Survey on Security for Smartphone Device. International Journal of Advanced Computer Science and Applications.
Mr. S. Sumahasan et al, ?A Node-Level Security Algorithm for Cloud Assisted-IoT?, NeuroQuantology, Volume 20 Issue 11.September 2022.
S.L. Keoha, S. S. Kumar and H. Tschofenig, ? Securing the Internet of Things:?, in IEEE Internet of Things Journal,Vol.1,no.3,pp.265- 275,June2014,doi:10.1109/JOIT.2014.2323395.
Rounak Sinha, Hemant Kumar srivatsava, Sumita Gupta,?Performance based comparison Study of RSA and Elliptic Curve of Cryptography?, IJSER, Vol: 4, Issues 5 May 2013.
Hindawi, Journal of Sensors ?Influence of Encryption Algorithms on Power Consumption in Energy Harvesting Systems? Volume 2019, Article ID 8520562.
Generation Methods of Elliptic Curves by Harald Baier and Johannes Buchmann August 27, 2002.
Manan Mehta, ?ESP8266: A Breakthrough in wireless sensor networks and internet of things?, IJECET, Vol: 6, Issue:8, August 2015.
Makarenko, S. Semushin, S. Suhai, S. M. Ahsan Kazmi, A. Oracevic and R. Hussain, "A Comparative Analysis of Cryptographic. Algorithms in the Internet of Things," 2020 International Scientific and Technical Conference ModernComputer Network Technologies (MoNeTeC), Moscow, Russia, 2020, pp. 1-8, doi:10.1109/MoNeTeC49726.2020.9258156.
Kanakaris, Venetis & Papakostas, George & Bandekas, D.V.. (2019). Power consumption analysis on an IoT network based on wemos: a case study. TELKOMNIKA (Telecommunication Computing Electronics and Control). 17. 2505.10.12928/telkomnika.v17i5.11317.
Ooko, Samson. (2019). A Comparison of Arduino, Raspberry Pi and ESP8266 Boards.
V.A. Thakor, M.A. Razzaque, M.R.A. KhandakerLightweightcryptographyalgorithms for resource-constrained IoT devices: A review, comparison and research opportunities IEEE Access, 9 (2021), pp. 28177-28193.
Al_Barazanchi I, Murthy A, Al Rababah AA, Khader G, Abdulshaheed HR, Rauf HT, Daghighi E, Niu Y (2022) Blockchain technology-based solutions for IOT security. Iraqi J Comput Sci Math 3(1):53–63
Lata N, Kumar R (2022) Security in internet of things (IoT): challenges and models. Math Stat Eng Appl 71(2):75–81
Alfandi O, Khanji S, Ahmad L, Khattak A (2021) A survey on boosting IoT security and privacy through block chain. Clust Comput 24:1–19
S. Singh, A.S.M.S. Hosen, B. Yoon Blockchain security attacks, challenges, and solutions for the future distributed IoT network IEEE Access, 9 (2021), pp. 13938-13959
IoT devices are more vulnerable thaneverHomepage. https://www.itpro.com/network-internet/internet-of-things-iot/360850/iot-devices-are-more-vulnerable-than-ever. Last accessed 23 Mar 2022
M. Hasan, ?IoT in healthcare: 20 examples That'll make you feel better,? April 2, 2020. [Online]. Available: https://www.ubuntupit.com/iot-in-healthcare-20-examples-thatll-make-you-feel-better.
H. HaddadPajouh, A. Dehghantanha, R. Parizi, M. Aledhari, H. KarimipourAsurvey on internet of things security: requirements, challenges and solutions Elsevier: Internet of Things, 14 (2021).
Naidu, Purushotam, P. Krishna Subba Rao, and MHM Krishna Prasad. "Smart-farming: IoT Based Crop Prediction System using Machine Learning Techniques." Solid State Technology 64, no. 1 (2021): 4085-4096
]Kaspersky(2022)AttacksonIoTdevicesdoubleinayearHomepage. https://iottechnews.com/news/2021/sep/07/kaspersky-attacks-on-iot-devices-double-inayear/.Lastaccessed 21 Mar 2022.