GBJOF: Gradient Boosting Integrated with Jaya Algorithm to Optimize the Features in Malware Analysis
Main Article Content
Abstract
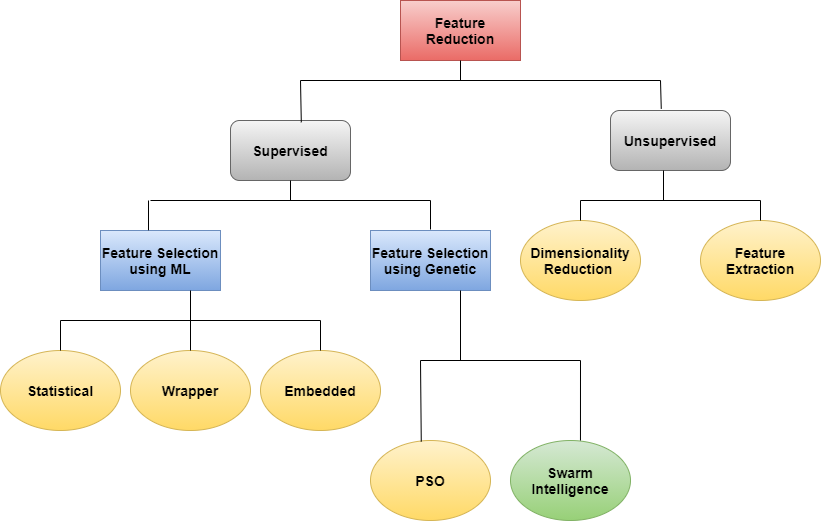
Malware analysis is used to identify suspicious file transferring in the network. It can be identified efficiently by using the reverse engineering hybrid approach. Implementing a hybrid approach depends on the feature selection because the dataset contains static and dynamic parameters. The given dataset contains 85 attributes with 10 different class labels. Since it has high dimensional and multi-classification data, existing approaches of ML could be more efficient in reducing the features. The model combines the enhanced JAYA genetic algorithm with a gradient boosting technique to identify the efficiency and a smaller number of features. Many existing approaches for feature selection either implement correlation analysis or wrapper techniques. The major disadvantages of these issues are that they are facing fitting problems with a very small number of features. With the Usage of the genetic approach, this paper has achieved 95% accuracy with 12 features, approximately 7% greater than ML approaches.
Article Details
References
Shhadat, I., Bataineh, B., Hayajneh, A., & Al-Sharif, Z. A. (2020). The Use of Machine Learning Techniques to Advance the Detection and Classification of Unknown Malware. Procedia Computer Science, 170, 917–922. https://doi.org/10.1016/j.procs.2020.03.110
Srinivasan, R., Karpagam, S., Kavitha, M., & Kavitha, R. (2022). An Analysis of Machine Learning-Based Android Malware Detection Approaches. Journal of Physics: Conference Series, 2325(1). https://doi.org/10.1088/1742-6596/2325/1/012058
Akhtar, M. S., & Feng, T. (2022). Malware Analysis and Detection Using Machine Learning Algorithms. Symmetry, 14(11). https://doi.org/10.3390/sym14112304
Ayeni, O. A. (2022). A Supervised Machine Learning Algorithm for Detecting Malware. Journal of Internet Technology and Secured Transactions, 10(1), 764–769. https://doi.org/10.20533/jitst.2046.3723.2022.0094
Akhtar, M. S., & Feng, T. (2023). Evaluation of Machine Learning Algorithms for Malware Detection. Sensors, 23(2). https://doi.org/10.3390/s23020946
Usman, Nighat, Saeeda Usman, Fazlullah Khan, Mian Ahmad Jan, Ahthasham Sajid, Mamoun Alazab, and Paul Watters. "Intelligent dynamic malware detection using machine learning in IP reputation for forensics data analytics." Future Generation Computer Systems 118 (2021): 124-141.
Khan, Firoz, Cornelius Ncube, Lakshmana Kumar Ramasamy, Seifedine Kadry, and Yunyoung Nam. "A digital DNA sequencing engine for ransomware detection using machine learning." IEEE Access 8 (2020): 119710-119719.
Hwang, J., Kim, J., Lee, S., & Kim, K. (2020). Two-Stage Ransomware Detection Using Dynamic Analysis and Machine Learning Techniques. Wireless Personal Communications. doi:10.1007/s11277-020-07166-9
Mahindru, A., Sangal, A.L. MLDroid—a framework for Android malware detection using machine learning techniques. Neural Comput & Applic 33, 5183–5240 (2021). https://doi.org/10.1007/s00521-020-05309-4
Daoudi, N., Samhi, J., Kabore, A.K., Allix, K., Bissyandé, T.F., Klein, J. (2021). DEXRAY: A Simple, yet Effective Deep Learning Approach to Android Malware Detection Based on Image Representation of Bytecode. In: Wang, G., Ciptadi, A., Ahmadzadeh, A. (eds) Deployable Machine Learning for Security Defense. MLHat 2021. Communications in Computer and Information Science, vol 1482. Springer, Cham. https://doi.org/10.1007/978-3-030-87839-9_4
Akhtar, M. S., & Feng, T. (2023). Evaluation of Machine Learning Algorithms for Malware Detection. Sensors, 23(2), 946. MDPI AG. Retrieved from http://dx.doi.org/10.3390/s23020946
Shaukat, K., Luo, S., & Varadharajan, V. (2023). A novel deep learning-based approach for malware detection. In Engineering Applications of Artificial Intelligence (Vol. 122, p. 106030). Elsevier BV. https://doi.org/10.1016/j.engappai.2023.106030
Dhalaria, M., Gandotra, E., & Gupta, D. (2023). Comparative Analysis of Feature Selection Methods for Detection of Android Malware. In T. Kavitha, G. Senbagavalli, D. Koundal, Y. Guo, & D. Jain (Eds.), Convergence of Deep Learning and Internet of Things: Computing and Technology (pp. 263-284). IGI Global. https://doi.org/10.4018/978-1-6684-6275-1.ch013
Chaganti, R., Ravi, V., & Pham, T. D. (2023). A multi-view feature fusion approach for effective malware classification using Deep Learning. In Journal of Information Security and Applications (Vol. 72, p. 103402). Elsevier BV. https://doi.org/10.1016/j.jisa.2022.103402
Herrera-Silva, J. A., & Hernández-Álvarez, M. (2023). Dynamic Feature Dataset for Ransomware Detection Using Machine Learning Algorithms. Sensors, 23(3), 1053. MDPI AG. Retrieved from http://dx.doi.org/10.3390/s23031053
Maniriho, P., Mahmood, A. N., & Chowdhury, M. J. M. (2022). A study on malicious software behaviour analysis and detection techniques: Taxonomy, current trends and challenges. In Future Generation Computer Systems (Vol. 130, pp. 1–18). Elsevier BV. https://doi.org/10.1016/j.future.2021.11.030
Urooj, U., Al-rimy, B. A. S., Zainal, A., Ghaleb, F. A., & Rassam, M. A. (2021). Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions. Applied Sciences, 12(1), 172. MDPI AG. Retrieved from http://dx.doi.org/10.3390/app12010172
Benjamin Jackson, Mark Johnson, Andrea Ricci, Piotr Wi?niewski, Laura Martínez. Intelligent Automation through the Integration of Machine Learning and Decision Science. Kuwait Journal of Machine Learning, 2(4). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/222
Yadav, C. S., Singh, J., Yadav, A., Pattanayak, H. S., Kumar, R., Khan, A. A., Haq, M. A., et al. (2022). Malware Analysis in IoT & Android Systems with Defensive Mechanism. Electronics, 11(15), 2354. MDPI AG. Retrieved from http://dx.doi.org/10.3390/electronics11152354
Rath, M. & Mishra, S. (2022). Advanced-Level Security in Network and Real-Time Applications Using Machine Learning Approaches. In I. Management Association (Ed.), Research Anthology on Machine Learning Techniques, Methods, and Applications (pp. 664-680). IGI Global. https://doi.org/10.4018/978-1-6684-6291-1.ch035
Fahd Alhaidari, Nouran Abu Shaib, Maram Alsafi, Haneen Alharbi, Majd Alawami, Reem Aljindan, Atta-ur Rahman, Rachid Zagrouba, "ZeVigilante: Detecting Zero-Day Malware Using Machine Learning and Sandboxing Analysis Techniques", Computational Intelligence and Neuroscience, vol. 2022, Article ID 1615528, 15 pages, 2022. https://doi.org/10.1155/2022/1615528
Usman, N., Usman, S., Khan, F., Jan, M. A., Sajid, A., Alazab, M., & Watters, P. (2021). Intelligent Dynamic Malware Detection using Machine Learning in IP Reputation for Forensics Data Analytics. In Future Generation Computer Systems (Vol. 118, pp. 124–141). Elsevier BV. https://doi.org/10.1016/j.future.2021.01.004
A. Abusnaina et al., "DL-FHMC: Deep Learning-Based Fine-Grained Hierarchical Learning Approach for Robust Malware Classification," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 5, pp. 3432-3447, 1 Sept.-Oct. 2022, doi: 10.1109/TDSC.2021.3097296.
Srinivasan, S., Vinayakumar, R., Arunachalam, A., Alazab, M., & Soman, K. (2020). DURLD: Malicious URL Detection Using Deep Learning-Based Character Level Representations. In Malware Analysis Using Artificial Intelligence and Deep Learning (pp. 535–554). Springer International Publishing. https://doi.org/10.1007/978-3-030-62582-5_21
Suryanarayana, G., Prakash K, L., Mahesh, P.C.S. et al. Novel dynamic k-modes clustering of categorical and non categorical dataset with optimized genetic algorithm based feature selection. Multimed Tools Appl 81, 24399–24418 (2022). https://doi.org/10.1007/s11042-022-12126-5
Balakrishna, G., V. Radha, and K. Rao. "ESMP: EXPLORATORY SCALE FOR MALWARE PERCEPTION THROUGH API CALL SEQUENCE LEARNING." journal of theoretical & applied information technology 95.10 (2017).
Daoudi, N., Samhi, J., Kabore, A. K., Allix, K., Bissyandé, T. F., & Klein, J. (2021). DexRay: A Simple, yet Effective Deep Learning Approach to Android Malware Detection Based on Image Representation of Bytecode. In Deployable Machine Learning for Security Defense (pp. 81–106). Springer International Publishing. https://doi.org/10.1007/978-3-030-87839-9_4
Mahindru, A., Sangal, A. FSDroid:- A feature selection technique to detect malware from Android using Machine Learning Techniques. Multimed Tools Appl 80, 13271–13323 (2021). https://doi.org/10.1007/s11042-020-10367-w
Hira, S., Bai, A. A Novel Map Reduced Based Parallel Feature Selection and Extreme Learning for Micro Array Cancer Data Classification. Wireless Pers Commun 123, 1483–1505 (2022). https://doi.org/10.1007/s11277-021-09196-3
Agrawal, P., & Trivedi, B. (2020). Machine Learning Classifiers for Android Malware Detection. In Data Management, Analytics and Innovation (pp. 311–322). Springer Singapore. https://doi.org/10.1007/978-981-15-5616-6_22