Secured Scheme for Privacy Preserving and Node Authentication Mechanism for a Special Mobile Ad hoc Network
Main Article Content
Abstract
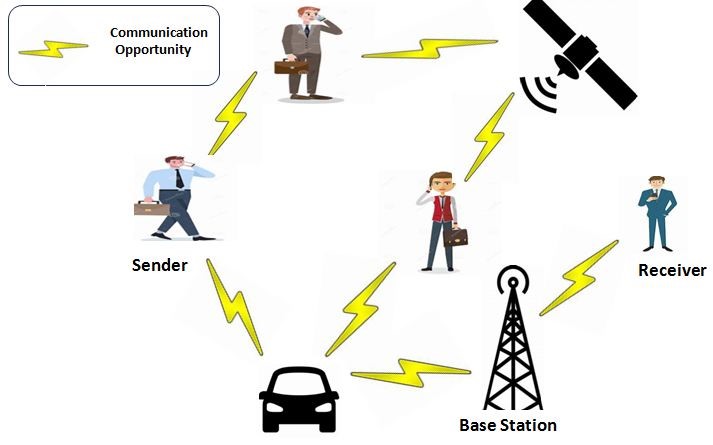
Opportunistic networks are a special type of Mobile Ad hoc network which are wirelessly interlinked nodes with the absence of end to end connectivity. All nodes in an opportunistic network are free to move in an environment. Due to the high degree of mobility of nodes, opportunistic networks differ significantly from the existing traditional networks and it works on store, carry &forward mechanism in which, each node has a communication range. Within its proximity, if any node comes, it can send and receive messages. In an opportunistic network, there is no proper infrastructure available for communication and node have limited storage and computational capabilities. The major problem being faced in an opportunistic network is the identification of normal and malicious nodes because due to the open nature of the opportunistic network, malicious nodes also can join the network and perform some malicious activities like Sybil attack. We propose a remedy to address the authentication and privacy issue that can arise in an opportunistic network. According to the findings of the simulation, the proposed research work satisfies the authentication and privacy criteria of an opportunistic network.
Article Details
References
. Z. Y. Le, G. Vakde, and M. Wright, “Peon: privacy enhanced opportunistic networks with applications in assistive environments, “in Proceedings of the 2ndinternational conference on Pervasive technologies related to assistive environments, vol. 1–8, Corfu,Greece,June2009.
. W.-C. Kuo, H.-J. Wei, and J.-C. Cheng, “An efficient and secure anonymous mobility network authentication scheme,” journal of information security and applications, vol.19,no. 1,pp. 18–24, 2014.
. N. Ahmad, H. Cruickshank, Y. Cao et al., “Privacy by architecture pseudonym framework for delay tolerant network,” Future Generation Computer Systems, vol. 93, pp. 979–992,2019.
. C .B. Avoussoukpo, T.B. Ogunseyi, and M.Tchenagnon, “Securing and facilitating communication within opportunistic networks: a holistic survey,” IEEE access, vol. 9, pp.55009–55035,2021.
. G. Srivastava, R. Agrawal, K. Singh, R. Tripathi, and K. Naik, “A hierarchical identity based security for delay tolerant networks using lattice based cryptography,” Peer-to-Peer Networking and Applications, vol. 13,no.1, pp.348–367,2020.
. K.ChenandH.Shen,“ FaceChange: attaining neighbor node anonymity in mobile opportunistic social networks with fine grained control,”IEEE/ACM Transactions son Networking, vol. 25, no. 2,pp. 1176–1189,2017.
. N.Magaia,C.Borrego, and P.Pereira,“ePRIVO : an enhanced privacy preserving opportunistic routing protocol for vehicular delay-tolerant networks,” IEEE Transactions on Vehicular Technology, vol. 67,no. 11,pp. 11154–11168,2018.
. Rashidibajgan,S. & Hupperich,T. Improving the Performance of Opportunistic Networks in Real World Applications Using Machine Learning Techniques. Journal of Sensor andActuatorNetworks11,(2022)
. S. Rashidibajgan, T. Hupperich, R. Doss, and A. F¨orster, “Secure and privacy preserving structure in opportunistic networks,”Computers &Security,vol.104,pp.1–15,2021.
. Rashidibajgan,S.;Doss,R. Privacy preserving history based routing in Opportunistic Networks.Comput. Secur. 2019, 84,244–255.
. Y. Mao, C. Zhou, Y. Ling, and J. Lloret, “An optimized probabilistic delay tolerant network(DTN) routing protocol based on scheduling mechanism for Internet of things (IoT),”Sensors,vol. 19, no. 243,pp.1–16,2019.
. E. K. Wang, Y. Li, Y. Ye, S. M. Yiu and L. C. K. Hui, "A Dynamic Trust Framework for Opportunistic Mobile Social Networks," in IEEE Transactions on Network and Service Management, vol. 15, no. 1, pp. 319-329, March 2018, doi:10.1109/TNSM.2017.2776350.
. Li, F.; Jiang, H.; Wang, Y.; Hashang, L.; Cheng, Y. SEBAR: Social Energy Based Routing scheme for mobile social Delay Tolerant Networks. IEEE Trans. Veh. Technol. 2017, 66,7195–7206.
. Chen,K.;Shen,H.Y.Face Change: Attaining neighbor node anonymity in mobile opportunistic social networks with fine-grained control.IEEE/ACMTrans.Netw.2017,25,1176–118
. Guo,M.,Liaw,H.,Chiu,M.,Tsai,L.: Authenticating with Privacy Protection in Opportunistic Networks Ming Huang.In: EAI International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness (QSHINE2015).pp. 375–380(2015).
. C.Xi,S.Liang, M.Jianfengand, M.Zhuo,"A trust management scheme based on behavior feedback for opportunistic networks," in China Communications, vol. 12, no. 4,pp.117-129, April 2015,doi:10.1109/CC.2015.7114058
. Goyal, M., Chaudhary, M.: Ensuring Privacy in opportunistic Network. IOSR J. Comput.Eng.13, 74–82(2013).
. B.PoonguzharselviandV.Vetriselvi“TrustFrameworkforDataForwardinginOpportunistic network Using Mobile Traces” International Journal of Wireless & Mobile Networks(IJWMN)Vol. 4,No.6, December2012.
. Greede, A. & Allen, Stuart & Whitaker, Roger. (2009). RFP: Repository Based Forwarding Protocol for Opportunistic Networks. Next Generation Mobile Applications, Services andTechnologies,InternationalConferenceon.329-334.10.1109/NGMAST.2009.33.
. Jian Ren, Yun Li, and Tongtong Li, “SPM: Source Privacy for Mobile Ad Hoc Networks”,Journal on Wireless Communications and Networking,doi:10.1155/2010/534712,2010.
. A. T. A. Forwarding and S. M. Traces, Data Forwarding In Opportunistic Network Using Mobile Traces, In Data Forwarding In Opportunistic Network Using Mobile Traces, 2012, 425–430.
. M. Alajeely, R. Doss, and A. Ahmad, Security and Trust in Opportunistic Networks – A Survey, IETE Tech. Rev., vol. 33, no. 3, 256–268, 2016.
. J. L. Tsai and N. W. Lo, Provably secure anonymous authentication with batch verification for mobile roaming services, Ad Hoc Networks, vol. 44, 19–31, 2016
. Kang, M.W.; Seo, D.Y.; Chung, Y.W. An efficient delay tolerant networks routing protocol for information-centric networking. Electronics 2020, 9, 839.
. Xiao, Y.; Wu, J. Data transmission and management based on node communication in opportunistic social networks. Symmetry 2020, 12, 1288.
. Goudar, G.; Batabyal, S. Optimizing bulk transfer size and scheduling for efficient buffer management in mobile opportunistic networks. IEEE Trans. Mob. Comput. 2021, 1–16.
. Kandhoul, N.; Dhurandher, S.K. An efficient and secure data forwarding mechanism for opportunistic IoT. Wirel. Pers. Commun. 2021, 118, 217–237.