Intrusion Detection Mechanism for Empowered Intruders Using IDEI
Main Article Content
Abstract
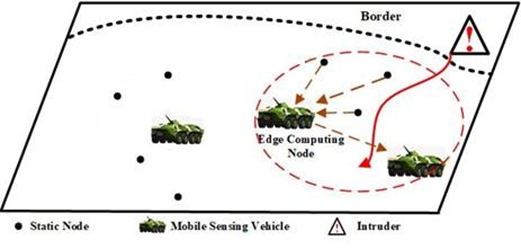
In the past, intrusion detection has been extensively investigated as a means of ensuring the security of wireless sensor networks. Anti-recon technology has made it possible for an attacker to get knowledge about the detecting nodes and plot a route around them in order to evade detection. An "empowered intruder" is one who poses new threats to current intrusion detection technologies. Furthermore, the intended impact of detection may not be obtained in certain subareas owing to gaps in coverage caused by the initial deployment of detection nodes at random. A vehicle collaboration sensing network model is proposed to solve these difficulties, in which mobile sensing cars and static sensor nodes work together to identify intrusions by empowered intruders. An algorithm for mobile sensing vehicles, called Intrusion Detection Mechanism for Empowered Intruders(IDEI), and a sleep-scheduling technique for static nodes form the basis of our proposal. Sophisticated intruders will be tracked by mobile sensors, which will fill in the gaps in coverage, while static nodes follow a sleep schedule and will be woken when the intruder is discovered close. Our solution is compared to current techniques like Kinetic Theory Based Mobile Sensor Network (KMsn)and Mean Time to Attacks (MTTA) in terms of intrusion detection performance, energy usage, and sensor node movement distance. IDEI's parameter sensitivity is also examined via comprehensive simulations. It is clear from the theoretical analysis and simulation findings that our idea is more efficient and available.
Article Details
References
B. Liu, O. Dousse, P. Nain, and D. Towsley, ‘‘Dynamic coverage of mobile sensor networks,’’ IEEE Trans. Parallel Distrib. Syst., vol. 24, no. 2, pp. 301–311, Feb. 2021.
Q. Zhang and M. Fok, ‘‘A two-phase coverage- enhancing algorithm for hybrid wireless sensor networks,’’ Sensors, vol. 17, no. 12, p. 117, Jan. 2017.
S. Sharmin, F. N. Nur, M. A. Razzaque, M. M. Rahman, A. Almogren, and M. M. Hassan, ‘‘Tradeoff between sensing quality and network lifetime for heterogeneous target coverage using directional sensor nodes,’’ IEEE Access, vol. 5, pp. 15490–15504, 2017.
Y. Liu, J.-S. Fu, and Z. Zhang, ‘‘K-nearest neighbors tracking in wireless sensor networks with coverage holes,’’ Pers. Ubiquitous Comput., vol. 20, no. 3, pp. 431–446, Jun. 2019.
Tripathi, A. ., Pandey, R. ., & Singh, A. . (2023). Comparison of Performance of Boneh-Shaw Finger Printing Codes with Tardos Under Randomized Bits Collusion Attacks . International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 01–10. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2501
S. Silvestri and K. Goss, ‘‘MobiBar: An autonomous deployment algo- rithm for barrier coverage with mobile sensors,’’ Ad Hoc Netw., vol. 54, pp. 111–129, Jan. 2020.
K. Zhou and S. Roumeliotis, ‘‘Optimal motion strategies for range-only constrained multisensor target tracking,’’ IEEE Trans. Robot., vol. 24, no. 5, pp. 1168–1185, Oct. 2021.
Joseph Miller, Peter Thomas, Maria Hernandez, Juan González, Carlos Rodríguez. Exploring Ensemble Learning in Decision Science Applications. Kuwait Journal of Machine Learning, 2(3). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/206
H. Mahboubi, W. Masoudimansour, A. G. Aghdam, and K. Sayrafian-Pour, ‘‘An energy-efficient target- tracking strategy for mobile sensor networks,’’ IEEE Trans. Cybern., vol. 47, no. 2, pp. 511–523, Feb. 2020.
T. P. Lambrou, ‘‘Optimized cooperative dynamic coverage in mixed sensor networks,’’ ACM Trans. Sensor Netw., vol. 11, no. 3, pp. 1–35, Feb. 2021.
Z. Sun, P. Wang, M. C. Vuran, M. A. Al-Rodhaan, A. M. Al-Dhelaan, and I. F. Akyildiz, ‘‘BorderSense: Border patrol through advanced wireless sensor networks,’’ Ad Hoc Netw., vol. 9, no. 3, pp. 468–477, May 2019.
S. Meguerdichian, F. Koushanfar, and G. Qu, ‘‘Exposure in wireless ad- hoc sensor networks,’’ in Proc. 7th Annu. Int. Conf. Mobile Comput. Netw., 2020, pp. 139–150.
Veltri, Q. Huang, G. Qu, and M. Potkonjak, ‘‘Minimal and maximal exposure path algorithms for wireless embedded sensor networks,’’ in Proc. 1st Int. Conf. Embedded Networked Sensor Syst., 2021, pp. 40–50.
Z. Liu, W. Wei, H. Wang, Y. Zhang, Q. Zhang, and S. Li, ‘‘Intru- sion detection based on parallel intelligent optimization feature extrac- tion and distributed fuzzy clustering in WSNs,’’ IEEE Access, vol. 6, pp. 72201–72211, 2018.
S. D. Bopardikar, F. Bullo, and J. P. Hespanha, ‘‘Sensing limitations in the Lion and Man problem,’’ in Proc. Amer. Control Conf., Jul. 2019, pp. 5958–5963.