Sharing Secret Colour Images with Embedded Visual Cryptography Using the Stamping Algorithm and OTP Procedure
Main Article Content
Abstract
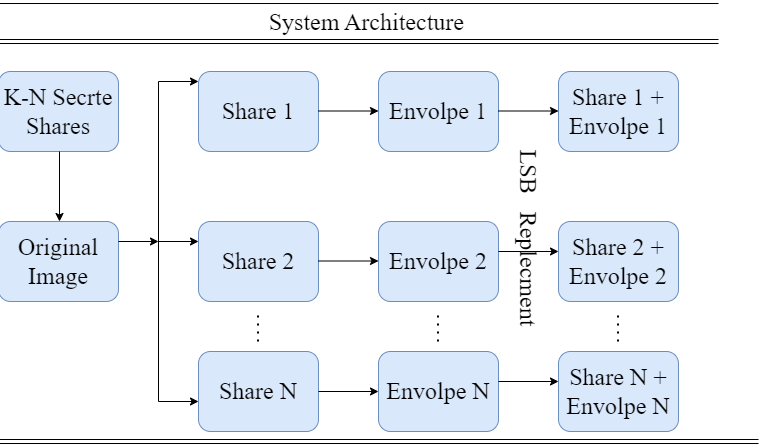
Finding a way to ensure the safety of media is becoming increasingly common in the modern world as digital media usage increases. Visual cryptography (VC) offers an efficient method for sending images securely. Images that have been protected using visual encryption can be decoded using features of human vision. Emails are not a highly safe method of exchanging private data because someone else can quickly weaken the content. In the visual cryptography technique, we presented for colour pictures, the divided shares are enclosed in additional pictures using stamping. Using a random number generator, the shares are created. Visual cryptography schemes (VCS) are a method of encoding pictures that conceals the secret information which is present in images. A secret image is encrypted using a straightforward visual cryptography technique by splitting it into n shares, and the stamping operation is carried out by overlapping k shares. It can be beneficial for hiding a secret image. There is a chance that employing cryptography for information exchange could cause security problems because the process of decryption of simple visual cryptographic algorithms can be completed by the human eye. To address this issue, we are using the OTP procedure. In the past, static ID and passwords were employed, making them susceptible to replay and eavesdropping attacks. One Time Password technology, which generates a unique password each time, is utilized to solve this issue. The suggested approach strengthens the security of the created transparencies by applying an envelope to each share and employing a stamping technique to address security vulnerabilities that the previous methods had, such as pixel expansion and noise.
Article Details
References
Varsha Himthani; Vijaypal Singh Dhaka; Manjit Kaur “Systematic Survey on Visually Meaningful Image Encryption Techniques”, 31 August 2022, IEEE.
Dhabliya, P. D. . (2020). Multispectral Image Analysis Using Feature Extraction with Classification for Agricultural Crop Cultivation Based On 4G Wireless IOT Networks. Research Journal of Computer Systems and Engineering, 1(1), 01–05. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/10
K Alghathbar “OTP-Based Two-Factor Authentication Using Mobile Phones”, 11-13 April 2021, IEEE.
K Anish; C K Sai Dinesh; S Ranjit; E Venkatesh; S V Shruthi “Performance Analysis of Visual Cryptography and Watermarking Algorithms” 27-29 May 2022,IEEE.
Jitendra Saturwar; D.N. Chaudhari “Secure visual secret sharing scheme for color images using visual cryptography and digital watermarking”, 22-24 February 2017,IEEE.
Suiang-Shyan Lee; Yi-Jheng Huang; Ja-Chen Lin “WEB-VC: Visual Cryptography for Web Image”, 22-25 September 2019, IEEE.
Hsiang-Cheh Huang, Jiun Lin,Yuh-Yih Lu “Visual Secret Sharing for Copyright Protection and Authentication of Colour Images”,2015 Third International Conference on Robot, Vision and Signal Processing.
Prof. Rathod V U Raisoni: N. P. Sable, R. Sonkamble, V. U. Rathod, S. Shirke, J. Y. Deshmukh, and G. T. Chavan, “Web3 Chain Authentication and Authorization Security Standard (CAA)”, IJRITCC, vol. 11, no. 5, pp. 70–76, May 2023.
Prof. Rathod V U Raisoni: N. P. Sable, V. U. Rathod, R. Sable and G. R. Shinde, "The Secure E-Wallet Powered by Blockchain and Distributed Ledger Technology," 2022 IEEE Pune Section International Conference (PuneCon), Pune, India, 2022, pp. 1-5, doi: 10.1109/PuneCon55413.2022.10014893.
Zellar, P. I. . (2021). Business Security Design Improvement Using Digitization. International Journal of New Practices in Management and Engineering, 10(01), 19–21. https://doi.org/10.17762/ijnpme.v10i01.98
Prof. Rathod V U Raisoni: N. P. Sable, V. U. Rathod, P. N. Mahalle and D. R. Birari, "A Multiple Stage Deep Learning Model for NID in MANETs," 2022 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 2022, pp. 1-6, doi: 10.1109/ESCI53509.2022.9758191.
Prof. Rathod V U Raisoni: N. P. Sable, M. D. Salunke, V. U. Rathod and P. Dhotre, "Network for Cross-Disease Attention to the Severity of Diabetic Macular Edema and Joint Retinopathy," 2022 International Conference on Smart Generation Computing, Communication and Networking (SMART GENCON), Bangalore, India, 2022, pp. 1-7, doi: 10.1109/SMARTGENCON56628.2022.10083936.
Prof. Rathod V U Raisoni: Vijay U. Rathod* & Shyamrao V. Gumaste, “EFFECT OF DEEP CHANNEL TO IMPROVE PERFORMANCE ON MOBILE AD-HOC NETWORKS”, J. Optoelectron. Laser, vol. 41, no. 7, pp. 754–756, Jul. 2022.
Christopher Davies, Matthew Martinez, Catalina Fernández, Ana Flores, Anders Pedersen. Applying Recommender Systems in Educational Platforms. Kuwait Journal of Machine Learning, 2(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/171
Prof. Rathod V U Raisoni: V. U. Rathod and S. V. Gumaste, “Role of Neural Network in Mobile Ad Hoc Networks for Mobility Prediction”, Int. j. commun. netw. inf. secur., vol. 14, no. 1s, pp. 153–166, Dec. 2022.
Mangesh D. Salunke, Ruhi Kabra, “Denial-of-Service Attack Detection”, International Journal of Innovative Research in Advanced Engineering (IJIRAE) ISSN: 2349-2163 Volume 1 Issue 11.
Mangesh D. Salunke, Ruhi Kabra, Ashish Kumar, “Layered architecture for DoS attack detection system by combine approach of Naive bays and Improved K-means Clustering Algorithm”, International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056 Volume: 02 Issue: 03 | June-2015.
Salunke M.D, Kumbharkar P.B., YK Sharma, “A Proposed Methodology to Prevent a Ransomware Attack”, International Journal of Recent Technology and Engineering (IJRTE) ISSN: 2277-3878, Volume-9 Issue-1, May 2020.
Wiling, B. (2021). Locust Genetic Image Processing Classification Model-Based Brain Tumor Classification in MRI Images for Early Diagnosis. Machine Learning Applications in Engineering Education and Management, 1(1), 19–23. Retrieved from http://yashikajournals.com/index.php/mlaeem/article/view/6
Salunke M.D, Kumbharkar P.B., YK Sharma, “A Survey on Ransomware attack: Detection Technique”, Dogo Rangsang Research Journal www.drsrjournal.com ISSN: 2347-7180 Vol-10 Issue-06 No. 14 June 2020.
Prof. Nilesh N. Thorat,” Visual Cryptography Schemes for Secret Colour Image Sharing using General Access Structure and Stamping Algorithm”, International Journal of Engineering Research & Technology (IJERT”, ISSN: 2278-0181, Vol. 4 Issue 03, March-2015.
Maria Gonzalez, Machine Learning for Anomaly Detection in Network Security , Machine Learning Applications Conference Proceedings, Vol 1 2021.
Prof. N. N. Thorat,” Embedded Visual Cryptography for Secret Colour Images Sharing using Stamping Algorithm, Encryption and Decryption technique”, IJARCCE, ISSN (Online) 2278-1021, Vol. 5, Issue 2, February 2016.
Prof. Rathod V U Raisoni: V. U. Rathod and S. V. Gumaste, “Role of Deep Learning in Mobile Ad-hoc Networks”, IJRITCC, vol. 10, no. 2s, pp. 237–246, Dec. 2022.
Prof. Rathod V U Raisoni: N. P. Sable, V. U. Rathod, P. N. Mahalle, and P. N. Railkar, “An Efficient and Reliable Data Transmission Service using Network Coding Algorithms in Peer-to-Peer Network”, IJRITCC, vol. 10, no. 1s, pp. 144–154, Dec. 2022.