Secure Authentication Scheme for the Internet of Things
Main Article Content
Abstract
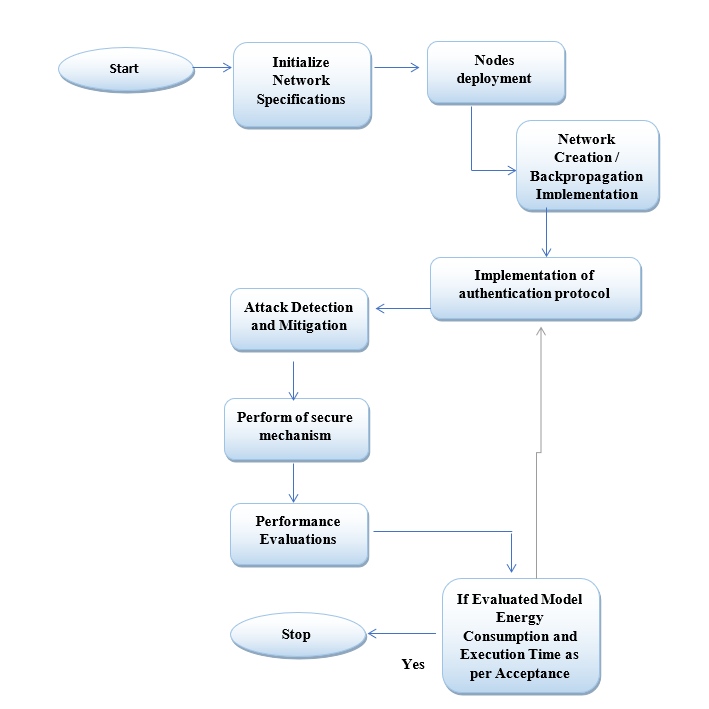
The Internet of Things (IoT) is based on an extensive and wide range of interconnected heterogeneous units’ general applications, including healthcare systems, environmental monitoring, household automation, and business automation. This work presents an approach variant of the elliptic curve; The cryptography approach is implemented to provide more security with fewer key sizes and with protocol enhancements to perform an efficient authentication process. In the process of authenticating the device, we use the Electronic Product Code (EPC) as a key to authentication, where the overhead of giving input is removed. Mention the methods followed to meet all your performance metrics (minimum execution time; low energy consumption, and qualitative comparison). This proposed scheme (i.e., the energy consumption of 0.27 mJ, the reduction in end delay of 0.058 sec., the reduction in the computation cost, and being more resistant to attack) is compared with other recent authentication protocols. The proposed system creates a secure network to lessen the damage if there is an attack in the IoT environment. The performance evaluation results indicate that the proposed scheme has a lower energy consumption and a more resistant authentication scheme, and we observe a trade-off between security and the lightweight factor.
Article Details
References
HaiYang Zhang;Yanli Ma;Benzhen Guo;Zhe Xu Light-weight IoT Gateway with Embedded Web Server 2020 12th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC) Year: 2020 DOI: 10.1109/IEEE Hangzhou, China
Hui Xia; Zhetao Li; Yuhui Zheng; Anfeng Liu; Young-June Choi; Hiroo Sekiya A Novel Light-Weight Subjective Trust Inference Framework in MANETs IEEE Transactions on Sustainable Computing Year: 2020 DOI: 10.1109/TSUSC.2018.281721
Xin Li; Guoliang Wei; Derui Ding; Shuai Liu Recursive Filtering for Time-Varying Discrete Sequential Systems Subject to Deception Attacks: Weighted Try-Once-Discard Protocol IEEE Transactions on Systems, Man, and Cybernetics: Systems Year: 2020
Jong-Young Choi;Jiwoong Park;Sung-Hwa Lim;Young-Bae Ko A RSSI-Based Mesh Routing Protocol based IEEE 802.11p/WAVE for Smart Pole Networks 2021 23rd International Conference on Advanced Communication Technology (ICACT) Year: 2021
Gyula Simon; Márk Rátosi Characterization and Measurement of Performance Properties of the UFSOOK Camera Communication Protocol IEEE Transactions on Instrumentation and Measurement Year: 2020
Ahmed Alrehaili; Aabid Mir POSTER: Blockchain-based Key Management Protocol for Resource-Constrained IoT Devices 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH) Year: 2020
Shafkat Islam;Shahriar Badsha; Shamik Sengupta, A Light-weight Blockchain Architecture for V2V Knowledge Sharing at Vehicular Edges 2020 IEEE International Smart Cities Conference (ISC2) Year: 2020
Kanthi Sree Addanki, Secure and Lightweight Authentication Protocols for Devices in Internet of Things, Computer Science and Engineering, National Institute of Technology Rourkela 2016.
Notom Ajaykumar, Mrinal Sarvagya, Parag Parandkar, A novel security algorithm ECC-L for wireless sensor network, Internet technology letter Volume3, Issue3, May/June 2020.
S. Chatterjee, A. K. Das, and J. K. Sing, “A novel and efficient user access control scheme for wireless body area sensor networks,” Journal of King Saud University-Computer and Information Sciences, vol. 26, no. 2, pp. 181–201, 2014.
Abosata N, Al-Rubaye S, Inalhan G. Lightweight Payload Encryption-Based Authentication Scheme for Advanced Metering Infrastructure Sensor Networks. Sensors (Basel). 2022;22(2):534. Published 2022 Jan 11. doi:10.3390/s22020534
S Ebrahimi, S Bayat-Sarmadi , Lightweight Fuzzy Extractor Based on LPN for Device and Biometric Authentication in IoT, - IEEE Internet of Things Journal, 2021
Bouguera, T.; Diouris, J.-F.; Chaillout, J.-J.; Jaouadi, R.; Andrieux, G. Energy Consumption Model for Sensor Nodes Based on LoRa and LoRaWAN. Sensors 2018, 18, 2104.
Modieginyane, Kgotlaetsile & Malekian, Reza & Letswamotse, Babedi. (2019). Flexible network management and application service adaptability in software defined wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing. 10. 1-10. 10.1007/s12652-018-0766-7.
A. Srivastava and A. Kumar, "A back propagation NN to optimize the IoT network," 2022, pp. 1-4, doi: 10.1109/ICCCI54379.2022.9740861.
Dengmei Xiang, Xuelian Li, Juntao Gao, Xiachuan Zhang, A secure and efficient certificateless signature scheme for Internet of Things, Ad Hoc Networks, Volume 124, 2022
Prakasam P, Madheswaran M, Sujith KP, Sayeed MS. Low Latency, Area and Optimal Power Hybrid Lightweight Cryptography Authentication Scheme for Internet of Things Applications. Wireless Personal Communications. 2022 May 4:1-5. https://doi.org/10.1007/s11277-022-09748-1
King-Hang Wang, Chien-Ming Chen, Weicheng Fang, Tsu-Yang Wu, A secure authentication scheme for Internet of Things, Pervasive and Mobile Computing, Volume 42,2017,Pages 15-26, https://doi.org/10.1016/j.pmcj.2017.09.004.
Park, K.; Park, Y. On the Security of a Lightweight and Secure Access Authentication Scheme for Both UE and mMTC Devices in 5G Networks. Appl. Sci. 2022, 12, 4265. https://doi.org/10.3390/app12094265
Bin Hu, Wen Tang, Qi Xie,A two-factor security authentication scheme for wireless sensor networks in IoT environments, Neurocomputing,Volume 500,2022,Pages 741-749, https://doi.org/10.1016/j.neucom.2022.05.099.
Bhanu Chander & Gopalakrishnan Kumaravelan (2022) An Improved 2-Factor Authentication Scheme for WSN Based on ECC, IETE Technical Review, DOI: 10.1080/02564602.2022.2055671 Zhongliang Xie, Lingyun Jiang. (2020). An improved authentication scheme for Internet of things. IOP Conference Series: Materials Science and Engineering. 715. 012031 https://doi.org/10.1088/1757-899X/715/1/012031
Zhanat Kenzhebayeva, Zhanar Akhmetova, Rysgul Bainazarova, Zhanar Kazhenova, Aigul Sariyeva. (2021). Simplified and Secure Authentication Scheme for the Internet of Things. Journal of Theoretical and Applied Information Technology.99 (23):5774-5782.
Muhammad H. Alharbi, Omar H. Alhazmi. (2021). User Authentication Scheme for Internet of Things Using Near-Field Communication. International Journal of Reliability, Quality and Safety Engineering. 27(5). 2040012. https://doi.org/10.1142/S0218539320400124
Hash-Based Signature for Flexibility Authentication of IoT Devices. HAN Songshen, XU Kaiyong, ZHU Zhiqiang, GUO Songhui, LIU Haidong, LI Zuohui. Wuhan University Journal of Natural Sciences 2022, Vol.27 No.1, 001-010. DOI https://doi.org/10.1051/wujns/2022271001
Lee, Young-Sil & Alasaarela, Esko & Lee, Hoonjae. (2014). An Efficient Encryption Scheme using Elliptic Curve Cryptography (ECC) with Symmetric Algorithm for Healthcare System. International Journal of Security and Its Applications. 8. 63-70. 10.14257/ijsia.2014.8.3.07.
Chien-Ming Chen, Xuanang Li, Shuangshuang Liu, Mu-En Wu, Saru Kumari, "Enhanced Authentication Protocol for the Internet of Things Environment", Security and Communication Networks, vol. 2022, Article ID 8543894, 13 pages, 2022. https://doi.org/10.1155/2022/8543894
Ummer Iqbal, Aditya Tandon, Sonali Gupta, Arvind R. Yadav, Rahul Neware, Fraol Waldamichael Gelana, "A Novel Secure Authentication Protocol for IoT and Cloud Servers", Wireless Communications and Mobile Computing, vol. 2022, Article ID 7707543, 17 pages, 2022. https://doi.org/10.1155/2022/7707543
Li Z, Li J, Zhao S, Chen X, Feng K, Wang W (2022) A blockchain-based lightweight identity authentication scheme for the IEDs of security and stability control system. PLoS ONE 17(3): e0265937. https://doi.org/10.1371/journal.pone.0265937
Bhanu Chander & Gopalakrishnan Kumaravelan (2022) An Improved 2-Factor Authentication Scheme for WSN Based on ECC, IETE Technical Review, DOI: 10.1080/02564602.2022.2055671
S. Chatterjee, A. K. Das, and J. K. Sing, “A novel and efficient user access control scheme for wireless body area sensor networks,” Journal of King Saud University-Computer and Information Sciences, vol. 26, no. 2, pp. 181–201, 2014.
Qing Fan, Jianhua Chen, Lazarus Jegatha Deborah, Min Luo, A secure and efficient authentication and data sharing scheme for Internet of Things based on blockchain, Journal of Systems Architecture, Volume 117, 2021,102112, ISSN 1383-7621,https://doi.org/10.1016/j.sysarc.2021.102112.
Saraireh, J., & Joudeh, H. (2022). An Efficient Authentication Scheme for Internet of Things. International Journal of Communication Networks and Information Security (IJCNIS), 13(3). https://doi.org/10.17762/ijcnis.v13i3.3422
Jain K, Kumar A, Singh A. Data transmission reduction techniques for improving network lifetime in wireless sensor networks: An up-to-date survey from 2017 to 2022. Trans Emerging Tel Tech. 2022; e4674. doi: 10.1002/ett.4674
Yadav, C.S., Gupta, S. A Review on Malware Analysis for IoT and Android System. SN COMPUT. SCI. 4, 118 (2023). https://doi.org/10.1007/s42979-022-01543-w
Szymoniak, S.; Kesar, S. Key Agreement and Authentication Protocols in the Internet of Things: A Survey. Appl. Sci. 2023, 13, 404. https://doi.org/10.3390/ app13010404
Foroozan Ghosairi Darbandeh, Masoumeh Safkhani, SAPWSN: A Secure Authentication Protocol for Wireless Sensor Networks, Computer Networks,Volume 220,2023,109469,ISSN 1389-1286,https://doi.org/10.1016/j.comnet.2022.109469.
Srivastava, A., Kumar, A. (2022). A Review of Network Optimization on the Internet of Things. In: Saini, H.S., Sayal, R., Govardhan, A., Buyya, R. (eds) Innovations in Computer Science and Engineering. Lecture Notes in Networks and Systems, vol 385. Springer, Singapore. https://doi.org/10.1007/978-981-16-8987-1_6
A. Srivastava and A. Kumar, "A Review on Authentication Protocol and ECC in IOT," 2021 International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), 2021, pp. 312-319, doi: 10.1109/ICACITE51222.2021.9404766.