BLA2C2: Design of a Novel Blockchain-based Light-Weight Authentication & Access Control Layer for Cloud Deployments
Main Article Content
Abstract
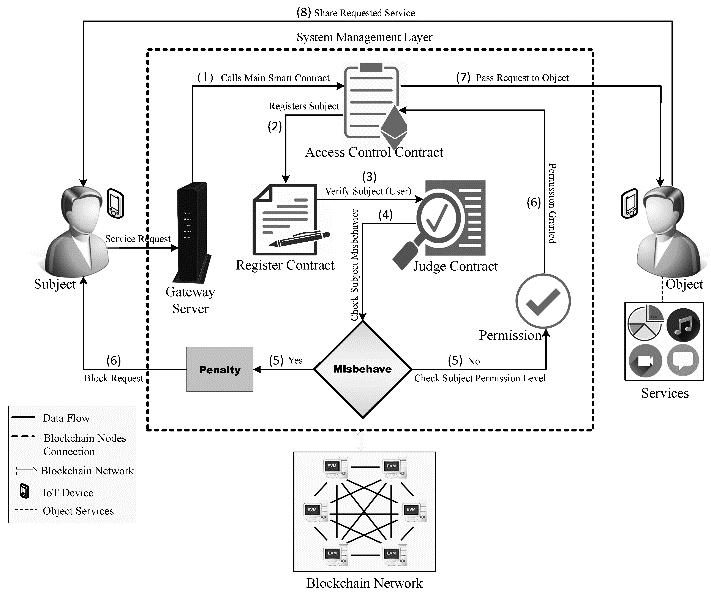
Cloud deployments are consistently under attack, from both internal and external adversaries. These attacks include, but are not limited to brute force, masquerading, improper access, session hijacking, cross site scripting (XSS), etc. To mitigate these attacks, a wide variety of authentication & access control models are proposed by researchers, and each of them vary in terms of their internal implementation characteristics. It was observed that these models are either highly complex, or lack in terms of security under multiple attacks, which limits their applicability for real-time deployments. Moreover, some of these models are not flexible and cannot be deployed under dynamic cloud scenarios (like constant reconfigurations of Virtual Machines, dynamic authentication use-cases, etc.). To overcome these issues, this text proposes design of a novel blockchain-based Light-weight authentication & access control layer that can be used for dynamic cloud deployments. The proposed model initially applies a header-level light-weight sanitization layer that removes Cross Site Scripting, SQL Injection, and other data-level attacks. This is followed by a light-weight authentication layer, that assists in improving login-level security for external attacks. The authentication layer uses IP matching with reverse geolocation mapping in order to estimate outlier login attempts. This layer is cascaded with an efficient blockchain-based access control model, which assists in mitigating session hijacking, masquerading, sybil and other control-level attacks. The blockchain model is developed via integration of Grey Wolf Optimization (GWO) to reduce unnecessary complexities, and provides faster response when compared with existing blockchain-based security deployments. Efficiency of the model was estimated in terms of accuracy of detection for different attack types, delay needed for detection of these attacks, and computational complexity during attack mitigation operations. This performance was compared with existing models, and it was observed that the proposed model showcases 8.3% higher accuracy, with 10.5% lower delay, and 5.9% lower complexity w.r.t. standard blockchain-based & other security models. Due to these enhancements, the proposed model was capable of deployment for a wide variety of large-scale scenarios.
Article Details
References
S. Bhatt, T. K. Pham, M. Gupta, J. Benson, J. Park and R. Sandhu, "Attribute-Based Access Control for AWS Internet of Things and Secure Industries of the Future," in IEEE Access, vol. 9, pp. 107200-107223, 2021, doi: 10.1109/ACCESS.2021.3101218.
S. Fugkeaw, "A Fine-Grained and Lightweight Data Access Control Model for Mobile Cloud Computing," in IEEE Access, vol. 9, pp. 836-848, 2021, doi: 10.1109/ACCESS.2020.3046869.
C. Yang, L. Tan, N. Shi, B. Xu, Y. Cao and K. Yu, "AuthPrivacyChain: A Blockchain-Based Access Control Framework With Privacy Protection in Cloud," in IEEE Access, vol. 8, pp. 70604-70615, 2020, doi: 10.1109/ACCESS.2020.2985762.
S. A. Chaudhry, K. Yahya, F. Al-Turjman and M. -H. Yang, "A Secure and Reliable Device Access Control Scheme for IoT Based Sensor Cloud Systems," in IEEE Access, vol. 8, pp. 139244-139254, 2020, doi: 10.1109/ACCESS.2020.3012121.
R. Ahuja and S. K. Mohanty, "A Scalable Attribute-Based Access Control Scheme with Flexible Delegation cum Sharing of Access Privileges for Cloud Storage," in IEEE Transactions on Cloud Computing, vol. 8, no. 1, pp. 32-44, 1 Jan.-March 2020, doi: 10.1109/TCC.2017.2751471.
A. Bakas, H. -V. Dang, A. Michalas and A. Zalitko, "The Cloud we Share: Access Control on Symmetrically Encrypted Data in Untrusted Clouds," in IEEE Access, vol. 8, pp. 210462-210477, 2020, doi: 10.1109/ACCESS.2020.3038838.
G. Ra, D. Kim, D. Seo and I. Lee, "A Federated Framework for Fine-Grained Cloud Access Control for Intelligent Big Data Analytic by Service Providers," in IEEE Access, vol. 9, pp. 47084-47095, 2021, doi: 10.1109/ACCESS.2021.3067958.
J. Park, R. Sandhu, M. Gupta and S. Bhatt, "Activity Control Design Principles: Next Generation Access Control for Smart and Collaborative Systems," in IEEE Access, vol. 9, pp. 151004-151022, 2021, doi: 10.1109/ACCESS.2021.3126201.
L. Gao, Z. Yan and L. T. Yang, "Game Theoretical Analysis on Acceptance of a Cloud Data Access Control System Based on Reputation," in IEEE Transactions on Cloud Computing, vol. 8, no. 4, pp. 1003-1017, 1 Oct.-Dec. 2020, doi: 10.1109/TCC.2016.2632110.
B. Celiktas, I. Celikbilek and E. Ozdemir, "A Higher-Level Security Scheme for Key Access on Cloud Computing," in IEEE Access, vol. 9, pp. 107347-107359, 2021, doi: 10.1109/ACCESS.2021.3101048.
S. Guan and S. Niu, "Stability-Based Controller Design of Cloud Control System With Uncertainties," in IEEE Access, vol. 9, pp. 29056-29070, 2021, doi: 10.1109/ACCESS.2021.3059766.
S. Guan and S. Niu, "Stability-Based Controller Design of Cloud Control System With Uncertainties," in IEEE Access, vol. 9, pp. 29056-29070, 2021, doi: 10.1109/ACCESS.2021.3059766.
Z. Zhang, Z. Yang, X. Du, W. Li, X. Chen and L. Sun, "Tenant-Led Ciphertext Information Flow Control for Cloud Virtual Machines," in IEEE Access, vol. 9, pp. 15156-15169, 2021, doi: 10.1109/ACCESS.2021.3051061.
S. Xiong, Q. Ni, L. Wang and Q. Wang, "SEM-ACSIT: Secure and Efficient Multiauthority Access Control for IoT Cloud Storage," in IEEE Internet of Things Journal, vol. 7, no. 4, pp. 2914-2927, April 2020, doi: 10.1109/JIOT.2020.2963899.
Y. Verginadis et al., "Context-Aware Policy Enforcement for PaaS-Enabled Access Control," in IEEE Transactions on Cloud Computing, vol. 10, no. 1, pp. 276-291, 1 Jan.-March 2022, doi: 10.1109/TCC.2019.2927341.
J. Cui, B. Li, H. Zhong, G. Min, Y. Xu and L. Liu, "A Practical and Efficient Bidirectional Access Control Scheme for Cloud-Edge Data Sharing," in IEEE Transactions on Parallel and Distributed Systems, vol. 33, no. 2, pp. 476-488, 1 Feb. 2022, doi: 10.1109/TPDS.2021.3094126.
K. Edemacu, B. Jang and J. W. Kim, "Efficient and Expressive Access Control With Revocation for Privacy of PHR Based on OBDD Access Structure," in IEEE Access, vol. 8, pp. 18546-18557, 2020, doi: 10.1109/ACCESS.2020.2968078.
J. Li, J. Ma, Y. Miao, R. Yang, X. Liu and K. -K. R. Choo, "Practical Multi-Keyword Ranked Search With Access Control Over Encrypted Cloud Data," in IEEE Transactions on Cloud Computing, vol. 10, no. 3, pp. 2005-2019, 1 July-Sept. 2022, doi: 10.1109/TCC.2020.3024226.
J. Ning, Z. Cao, X. Dong, K. Liang, L. Wei and K. -K. R. Choo, "CryptCloud$^+$+: Secure and Expressive Data Access Control for Cloud Storage," in IEEE Transactions on Services Computing, vol. 14, no. 1, pp. 111-124, 1 Jan.-Feb. 2021, doi: 10.1109/TSC.2018.2791538.
K. Huang, "Secure Efficient Revocable Large Universe Multi-Authority Attribute-Based Encryption for Cloud-Aided IoT," in IEEE Access, vol. 9, pp. 53576-53588, 2021, doi: 10.1109/ACCESS.2021.3070907.
L. Guo, X. Yang and W. -C. Yau, "TABE-DAC: Efficient Traceable Attribute-Based Encryption Scheme With Dynamic Access Control Based on Blockchain," in IEEE Access, vol. 9, pp. 8479-8490, 2021, doi: 10.1109/ACCESS.2021.3049549.
S. Qi, Y. Lu, W. Wei and X. Chen, "Efficient Data Access Control With Fine-Grained Data Protection in Cloud-Assisted IIoT," in IEEE Internet of Things Journal, vol. 8, no. 4, pp. 2886-2899, 15 Feb.15, 2021, doi: 10.1109/JIOT.2020.3020979.
N. Gholipoor, S. Parsaeefard, M. R. Javan, N. Mokari, H. Saeedi and H. Pishro-Nik, "Resource Management and Admission Control for Tactile Internet in Next Generation of Radio Access Network," in IEEE Access, vol. 8, pp. 136261-136277, 2020, doi: 10.1109/ACCESS.2020.3011466.
J. LI, N. CHEN and Y. ZHANG, "Extended File Hierarchy Access Control Scheme with Attribute-Based Encryption in Cloud Computing," in IEEE Transactions on Emerging Topics in Computing, vol. 9, no. 2, pp. 983-993, 1 April-June 2021, doi: 10.1109/TETC.2019.2904637.
H. Ma, R. Zhang, S. Sun, Z. Song and G. Tan, "Server-Aided Fine-Grained Access Control Mechanism with Robust Revocation in Cloud Computing," in IEEE Transactions on Services Computing, vol. 15, no. 1, pp. 164-173, 1 Jan.-Feb. 2022, doi: 10.1109/TSC.2019.2925028.
C. Hahn, J. Kim, H. Kwon and J. Hur, "Efficient IoT Management With Resilience to Unauthorized Access to Cloud Storage," in IEEE Transactions on Cloud Computing, vol. 10, no. 2, pp. 1008-1020, 1 April-June 2022, doi: 10.1109/TCC.2020.2985046.
H. Huang, Q. Tu, C. Jiang and M. Pan, "Nonsingular Terminal Sliding Mode Control Based on Sensor-Cloud System for Permanent Magnet in-Wheel Motor," in IEEE Access, vol. 8, pp. 140399-140410, 2020, doi: 10.1109/ACCESS.2020.3011922.
J. -B. Lee, T. -H. Yoo, E. -H. Lee, B. -H. Hwang, S. -W. Ahn and C. -H. Cho, "High-Performance Software Load Balancer for Cloud-Native Architecture," in IEEE Access, vol. 9, pp. 123704-123716, 2021, doi: 10.1109/ACCESS.2021.3108801.
S. T. Alshammari, K. Alsubhi, H. M. A. Aljahdali and A. M. Alghamdi, "Trust Management Systems in Cloud Services Environment: Taxonomy of Reputation Attacks and Defense Mechanisms," in IEEE Access, vol. 9, pp. 161488-161506, 2021, doi: 10.1109/ACCESS.2021.3132580.
H. Wang, D. He and J. Han, "VOD-ADAC: Anonymous Distributed Fine-Grained Access Control Protocol with Verifiable Outsourced Decryption in Public Cloud," in IEEE Transactions on Services Computing, vol. 13, no. 3, pp. 572-583, 1 May-June 2020, doi: 10.1109/TSC.2017.2687459.
S. J. De and S. Ruj, "Efficient Decentralized Attribute Based Access Control for Mobile Clouds," in IEEE Transactions on Cloud Computing, vol. 8, no. 1, pp. 124-137, 1 Jan.-March 2020, doi: 10.1109/TCC.2017.2754255.
K. Xue, N. Gai, J. Hong, D. S. L. Wei, P. Hong and N. Yu, "Efficient and Secure Attribute-Based Access Control With Identical Sub-Policies Frequently Used in Cloud Storage," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 1, pp. 635-646, 1 Jan.-Feb. 2022, doi: 10.1109/TDSC.2020.2987903.
J. Hong et al., "TAFC: Time and Attribute Factors Combined Access Control for Time-Sensitive Data in Public Cloud," in IEEE Transactions on Services Computing, vol. 13, no. 1, pp. 158-171, 1 Jan.-Feb. 2020, doi: 10.1109/TSC.2017.2682090.
Z. Ghaffar, S. Ahmed, K. Mahmood, S. H. Islam, M. M. Hassan and G. Fortino, "An Improved Authentication Scheme for Remote Data Access and Sharing Over Cloud Storage in Cyber-Physical-Social-Systems," in IEEE Access, vol. 8, pp. 47144-47160, 2020, doi: 10.1109/ACCESS.2020.2977264.
K. Edemacu, B. Jang and J. W. Kim, "Collaborative Ehealth Privacy and Security: An Access Control With Attribute Revocation Based on OBDD Access Structure," in IEEE Journal of Biomedical and Health Informatics, vol. 24, no. 10, pp. 2960-2972, Oct. 2020, doi: 10.1109/JBHI.2020.2973713.
R. Xu, J. Joshi and P. Krishnamurthy, "An Integrated Privacy Preserving Attribute-Based Access Control Framework Supporting Secure Deduplication," in IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 2, pp. 706-721, 1 March-April 2021, doi: 10.1109/TDSC.2019.2946073. A. Saini, Q. Zhu, N. Singh, Y. Xiang, L. Gao and Y. Zhang, "A Smart-Contract-Based Access Control Framework for Cloud Smart Healthcare System," in IEEE Internet of Things Journal, vol. 8, no. 7, pp. 5914-5925, 1 April1, 2021, doi: 10.1109/JIOT.2020.3032997.
S. Xu, J. Ning, X. Huang, J. Zhou and R. H. Deng, "Server-Aided Bilateral Access Control for Secure Data Sharing With Dynamic User Groups," in IEEE Transactions on Information Forensics and Security, vol. 16, pp. 4746-4761, 2021, doi: 10.1109/TIFS.2021.3113516.
W. Susilo, P. Jiang, J. Lai, F. Guo, G. Yang and R. H. Deng, "Sanitizable Access Control System for Secure Cloud Storage Against Malicious Data Publishers," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 3, pp. 2138-2148, 1 May-June 2022, doi: 10.1109/TDSC.2021.3058132.
Y. Hou, S. Garg, L. Hui, D. N. K. Jayakody, R. Jin and M. S. Hossain, "A Data Security Enhanced Access Control Mechanism in Mobile Edge Computing," in IEEE Access, vol. 8, pp. 136119-136130, 2020, doi: 10.1109/ACCESS.2020.3011477.
R. Ghazal, A. K. Malik, N. Qadeer, B. Raza, A. R. Shahid and H. Alquhayz, "Intelligent Role-Based Access Control Model and Framework Using Semantic Business Roles in Multi-Domain Environments," in IEEE Access, vol. 8, pp. 12253-12267, 2020, doi: 10.1109/ACCESS.2020.2965333.
X. Yang, R. Lu, J. Shao, X. Tang and A. A. Ghorbani, "Achieving Efficient Secure Deduplication With User-Defined Access Control in Cloud," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 1, pp. 591-606, 1 Jan.-Feb. 2022, doi: 10.1109/TDSC.2020.2987793.
S. Xu, Y. Li, R. H. Deng, Y. Zhang, X. Luo and X. Liu, "Lightweight and Expressive Fine-Grained Access Control for Healthcare Internet-of-Things," in IEEE Transactions on Cloud Computing, vol. 10, no. 1, pp. 474-490, 1 Jan.-March 2022, doi: 10.1109/TCC.2019.2936481.