Color Image Encryption using Chaotic Algorithm and 2D Sin-Cos Henon Map for High Security
Main Article Content
Abstract
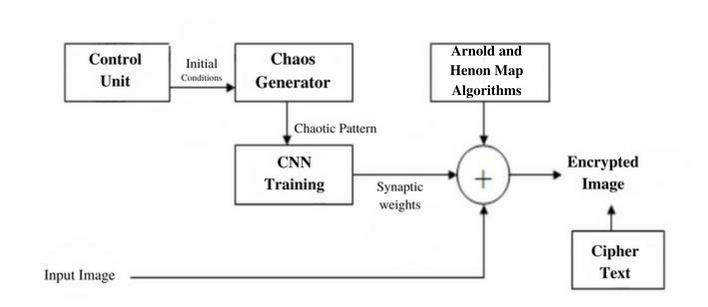
In every form of electronic communication, data security must be an absolute top priority. As the prevalence of Internet and other forms of electronic communication continues to expand, so too does the need for visual content. There are numerous options for protecting transmitted data. It's important that the transmission of hidden messages in images remain unnoticed to avoid raising any red flags. In this paper, we propose a new deep learning-based image encryption algorithm for safe image retrieval. The proposed algorithm employs a deep artificial neural network model to extract features via sample training, allowing for more secure image network transmission. The algorithm is incorporated into a deep learning-based image retrieval process with Convolution Neural Networks(CNN), improving the efficiency of retrieval while also guaranteeing the security of ciphertext images. Experiments conducted on five different datasets demonstrate that the proposed algorithm vastly improves retrieval efficiency and strengthens data security. Also hypothesised a 2D Sin-Cos-Henon (2D-SCH)-based encryption algorithm for highly secure colour images. We demonstrate that this algorithm is secure against a variety of attacks and that it can encrypt all three colour channels of an image simultaneously.
Article Details
References
Zhang, Qing, et al. “Image Security Retrieval Based on Chaotic Algorithm and Deep Learning.” IEEE Access, vol. 10, Institute of Electrical and Electronics Engineers (IEEE), 2022,pp.67210–18.Crossref, https://doi.org/10.1109/access.2022.3185421.
Pan, Hailan, et al. “Research on Digital Image Encryption Algorithm Based on Double Logistic Chaotic Map.” EURASIP Journal on Image and Video Processing, vol. 2018, no. 1, Springer Science and Business Media LLC, Dec. 2018. Crossref, https://doi.org/10.1186/s13640-018-0386-3.
Geng, Qiang, and Huifeng YAN. “Application of Image Encryption Algorithm for Wireless Sensor Network in the Security Analysis of Public Big Data.” Hindawi Wireless Communications and Mobile Computing Volume 2022, 13 Apr. 2022, doi.org/10.1155/2022/6186275.
Cheng, Zhiqiang, et al. “2D Sin-Cos-Henon Map for Color Image Encryption With High Security.” Journal of Applied Mathematics, edited by Tudor Barbu, vol. 2022, Hindawi Limited,Aug.2022,pp.1–11.Crossref, https://doi.org/10.1155/2022/9508749.
Shah, Jalpa, and JS Dhobi. “REVIEW OF IMAGE ENCRYPTION AND DECRYPTION TECHNIQUES FOR 2D IMAGES.” International Journal of Engineering Technologies and Management Research, vol. 5, no. 1, Granthaalayah Publications and Printers, Feb. 2020, pp. 81–84. Crossref, doi:10.29121/ijetmr.v5.i1.2018.49.
“Classical Image Encryption and Decryption.” International Journal of Science and Research (IJSR), vol. 4, no. 11, International Journal of Science and Research, Nov. 2015, pp. 607–12. Crossref, doi:10.21275/v4i11.sub159282.
Kanagalakshm, K., & Mekala, M. (2016, July 15). Enhanced Blowfish Algorithm for Image Encryption and Decryption with Supplementary Key. International Journal of Computer Applications,146(5),41–52. https://doi.org/10.5120/ijca2016910707
Pushkaran,Dhanya,andNeethuBhaskar.“AESENCRYPTION ENGINE FOR MANY CORE PROCESSOR ARRAYS FOR ENHANCED SECURITY.” IAEME, Dec. 2014, www.iaeme.com/IJECET.asp.
Daemen, Joan, and Vincent Rijmen. “The First 10 Years of Advanced Encryption.” IEEE Security & Privacy Magazine, vol. 8, no. 6, Institute of Electrical and Electronics Engineers (IEEE),Nov.2010,pp.72–74.Crossref, doi:10.1109/msp.2010.193.
Huang, X., Dong, Y., Ye, G., Yap, W. S., & Goi, B. M. (2023, February). Visually meaningful image encryption algorithm based on digital signature. Digital Communications and Networks,9(1),159–165. https://doi.org/10.1016/j.dcan.2022.04.028
Welba, C., Ramachandran, D., Noura, A., Tamba, V. K., Kingni, S. T., Ntsama, P. E., & Ele, P. (2022, February 28). Josephson Junction Model: FPGA Implementation and Chaos-Based Encryption of sEMG Signal through Image Encryption Technique. Complexity, 2022, 1–14. https://doi.org/10.1155/2022/4510236
Sreelaja, N. K., and N. K. Sreeja. “An Image Edge Based Approach for Image Password Encryption.” Security and Communication Networks, vol. 9, no. 18, Wiley, Dec. 2016, pp. 5733–45. Crossref, doi:10.1002/sec.1732.
Laiphrakpam, D. S., & Khumanthem, M. S. (2017, October). Medical image encryption based on improved ElGamal encryption technique. Optik, 147, 88–102. https://doi.org/10.1016/j.ijleo.2017.08.028
Zhou, N., Pan, S., Cheng, S., & Zhou, Z. (2016, August). Image compression–encryption scheme based on hyper-chaotic system and 2D compressive sensing. Optics & Laser Technology,82,121–133, https://doi.org/10.1016/j.optlastec.2016.02.018
Tong, X. J., Zhang, M., Wang, Z., & Ma, J. (2016, February 4). A joint color image encryption and compression scheme based on hyper-chaotic system. Nonlinear Dynamics, 84(4), 2333–2356. https://doi.org/10.1007/s11071-016-648-x
Survey of 3D Chaotic Map Techniques for Image Encryption. (2015, December 5). International Journal of Science and Research (IJSR), 4(12), 1000–1004. https://doi.org/10.21275/v4i12.nov152193
Xu, Y., & Zhen, X. (2022). Image encryption using improved Cubic map and Henon map. ITM Web of Conferences, 45, 02011. https://doi.org/10.1051/itmconf/20224502011
Enhancement Of Better Image Detection Using Encryption And Decryption Techniques. (2018, January 30). International Journal of Recent Trends in Engineering and Research,375–382. https://doi.org/10.23883/ijrter.conf.20171225.057.4wpxm