Secure Digital Information Forward Using Highly Developed AES Techniques in Cloud Computing
Main Article Content
Abstract
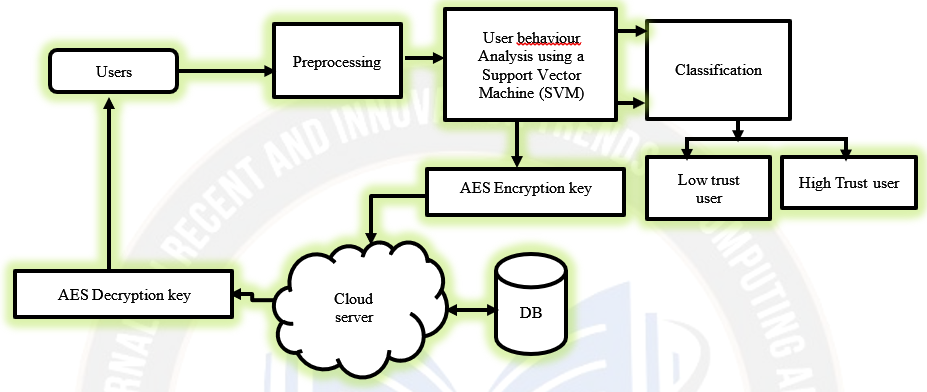
Nowadays, in communications, the main criteria are ensuring the digital information and communication in the network. The normal two users' communication exchanges confidential data and files via the web. Secure data communication is the most crucial problem for message transmission networks. To resolve this problem, cryptography uses mathematical encryption and decryption data on adaptation by converting data from a key into an unreadable format. Cryptography provides a method for performing the transmission of confidential or secure communication. The proposed AES (Advanced Encryption Standard)-based Padding Key Encryption (PKE) algorithm encrypts the Data; it generates the secret key in an unreadable format. The receiver decrypts the data using the private key in a readable format. In the proposed PKE algorithm, the sender sends data into plain Text to cypher-text using a secret key to the authorized person; the unauthorized person cannot access the data through the Internet; only an authorized person can view the data through the private key. A method for identifying user groups was developed. Support vector machines (SVM) were used in user behaviour analysis to estimate probability densities so that each user could be predicted to launch applications and sessions independently. The results of the proposed simulation offer a high level of security for transmitting sensitive data or files to recipients compared to other previous methods and user behaviour analysis.
Article Details
References
J. Shen, H. Yang, P. Vijayakumar and N. Kumar, "A Privacy-Preserving and Untraceable Group Data Sharing Scheme in Cloud Computing," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 4, pp. 2198-2210, 1 July-Aug. 2022, DOI: 10.1109/TDSC.2021.3050517.
S. Sushma, P. Srilatha and G. Srinivas, "Efficient Integrity Checking and Secured Data Sharing in Cloud," 2022 International Conference on Innovative Computing, Intelligent Communication and Smart Electrical Systems (ICSES), 2022, pp. 1-4, DOI: 10.1109/ICSES55317.2022.9914256.
V. K. Singh, N. Bharathiraja, S. Arun, D. B. David, R. Krishnamoorthy and R. Thiagarajan, "Secure Shared Data in the Private Cloud With an EA Algorithm," 2022 8th International Conference on Smart Structures and Systems (ICSSS), 2022, pp. 1-6, DOI: 10.1109/ICSSS54381.2022.9782299.
X. Luo, H. Wang, J. Dong, C. Zhang and T. Wu, "Achieving Privacy-preserving Data Sharing for Dual Clouds," 2022 IEEE International Conferences on Internet of Things (iThings) and IEEE Green Computing & Communications (GreenCom) and IEEE Cyber, Physical & Social Computing (CPSCom) and IEEE Smart Data (SmartData) and IEEE Congress on Cybernetics (Cybernetics), 2022, pp. 139-146, DOI: 10.1109/iThings-GreenCom-CPSCom-SmartData-Cybermatics55523.2022.00059.
J. Chang, B. Shao, Y. Ji and G. Bian, "Comment on “A Lightweight Auditing Service for Shared Data With Secure User Revocation in Cloud Storage”," in IEEE Transactions on Services Computing, vol. 15, no. 5, pp. 2633-2634, 1 Sept.-Oct. 2022, DOI: 10.1109/TSC.2021.3056660.
R. Mendes, T. Oliveira, V. Cogo, N. Neves and A. Bassani, "Charon: A Secure Cloud-of-Clouds System for Storing and Sharing Big Data," in IEEE Transactions on Cloud Computing, vol. 9, no. 4, pp. 1349-1361, 1 Oct.-Dec. 2021, DOI: 10.1109/TCC.2019.2916856.
J. Li, D. Yang and K. Zhang, "Secure Data Sharing Algorithm for Privacy Protection of Industrial Internet," 2021 IEEE Conference on Telecommunications, Optics and Computer Science (TOCS), 2021, pp. 202-208, DOI: 10.1109/TOCS53301.2021.9688774.
J. Shen, H. Yang, P. Vijayakumar and N. Kumar, "A Privacy-Preserving and Untraceable Group Data Sharing Scheme in Cloud Computing," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 4, pp. 2198-2210, 1 July-Aug. 2022, DOI: 10.1109/TDSC.2021.3050517.
k. Xue, N. Gai, J. Hong, D. S. L. Wei, P. Hong and N. Yu, "Efficient and Secure Attribute-Based Access Control With Identical Sub-Policies Frequently Used in Cloud Storage," in IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 1, pp. 635-646, 1 Jan.-Feb. 2022, DOI: 10.1109/TDSC.2020.2987903.
F. Wang, J. Wang and S. Shi, "Efficient Data Sharing With Privacy Preservation Over Lattices for Secure Cloud Storage," in IEEE Systems Journal, vol. 16, no. 2, pp. 2507-2517, June 2022, DOI: 10.1109/JSYST.2021.3077236.
S. Li, J. Han, D. Tong and J. Cui, "Redactable Signature-Based Public Auditing Scheme With Sensitive Data Sharing for Cloud Storage," in IEEE Systems Journal, vol. 16, no. 3, pp. 3613-3624, Sept. 2022, DOI: 10.1109/JSYST.2022.3159832
C. Hahn, J. Kim, H. Kwon and J. Hur, "Efficient IoT Management With Resilience to Unauthorized Access to Cloud Storage," in IEEE Transactions on Cloud Computing, vol. 10, no. 2, pp. 1008-1020, 1 April-June 2022, DOI: 10.1109/TCC.2020.2985046.
E. B. Sifah, Q. Xia, K. O. -B. O. Agyekum, H. Xia, A. Smahi and J. Gao, "A Blockchain Approach to Ensuring Provenance to Outsourced Cloud Data in a Sharing Ecosystem," in IEEE Systems Journal, vol. 16, no. 1, pp. 1673-1684, March 2022, DOI: 10.1109/JSYST.2021.3068224.
S. Son, D. Kwon, J. Lee, S. Yu, N. -S. Jho and Y. Park, "On the Design of a Privacy-Preserving Communication Scheme for Cloud-Based Digital Twin Environments Using Blockchain," in IEEE Access, vol. 10, pp. 75365-75375, 2022, DOI: 10.1109/ACCESS.2022.3191414.
S. Qi, Y. Lu, W. Wei and X. Chen, "Efficient Data Access Control With Fine-Grained Data Protection in Cloud-Assisted IIoT," in IEEE Internet of Things Journal, vol. 8, no. 4, pp. 2886-2899, 15 Feb.15, 2021, DOI: 10.1109/JIOT.2020.3020979.
S. -S. Zhang, X. Liang, Y. -D. Wei and X. Zhang, "On Structural Features, User Social Behavior, and Kinship Discrimination in Communication Social Networks," in IEEE Transactions on Computational Social Systems, vol. 7, no. 2, pp. 425-436, April 2020, DOI: 10.1109/TCSS.2019.2962231.
P. Mehetrey, B. Shahriari and M. Moh, "Collaborative Ensemble-Learning Based Intrusion Detection Systems for Clouds," 2016 International Conference on Collaboration Technologies and Systems (CTS), 2016, pp. 404-411, DOI: 10.1109/CTS.2016.0078.
P. Jha and A. Sharma, "Framework to Analyze Malicious Behaviour in Cloud Environment using Machine Learning Techniques," 2021 International Conference on Computer Communication and Informatics (ICCCI), 2021, pp. 1-12, DOI: 10.1109/ICCCI50826.2021.9402671.