Integrating the EGC, EF, and ECS Trio Approaches to Ensure Security and Load Balancing in the Cloud
Main Article Content
Abstract
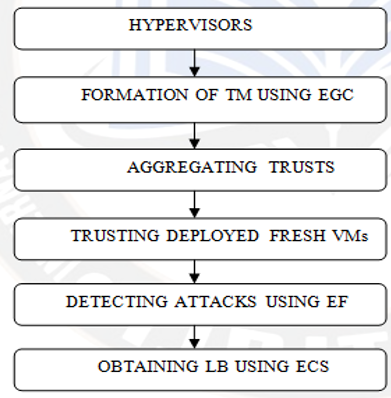
According to data protection studies, "Distributed Denial-of-Service (DDoS)" threats have cost governments and businesses throughout the globe a large number of financial resources. Despite this, the existing practices fall short of the standards set by "Cloud Computing (CC)" monitoring technology. They ignore the "Intrusion Detection Systems (IDS)" techniques, which take advantage of the CC's multiple tenants and elasticity qualities, and also the hardware limitations. Attackers are finding increasing ways to effectively exploit them because of their rising complexity. DDoS assaults of this scale have never been observed online before 2018. As online services get more popular, so does the amount of DDoS assaults and malevolent hackers leading to terrible. Numerous IDS for DDoS are already in place to address this problem. One of the most challenging aspects of virtualization is establishing a "Trust Model (TM)" between the many "Virtual Machines (VMs)". The lack of a standard formulation for generating a TM would be the primary reason. As a consequence, the integrity of every VM might not have been recognized by an independent trust, which might lead to a decrease in trust value. In this research for TM creation, "Enhanced Graph Based Clustering (EGC)" is proposed, while "Enhanced Fuzzy (EF)" is used for detecting attacks, and the "Enhanced Cuckoo Search (ECS)" method is used to find the ideal "Load Balancing (LB)" distribution. By creating a new TM, the proposed (EGC-EF-ECS) system strengthens trust value. To expand the CC model's stability, it optimizes attacker recognition percentage and makes better use of resources by restricting each VM's processing, bandwidth, and storage requirements. The proposed EGC-EF-ECS outperformed the previously used BPA-SAB, and DCRI-RI approaches in terms of the "Intrusion-Detection-Rate (IDR)", "Load-Balancing-Efficiency (LBE)", and "Data-Accessing-Time (DAT)" evaluation metrics.
Article Details
References
T. Alam, “Cloud computing and its role in the information technology”, IAIC Transactions on Sustainable Digital Innovation (ITSDI), vol. 1, no. 2, pp. 108–115, 2020.
J. Muda, S. Tumsa, A. Tuni, and D. P. Sharma, “Cloud-enabled E-governance framework for citizen-centric services”, Journal of Computer and Communications, vol. 8, no. 7, pp. 63–78, 2020.
A. A. Khan, A. A. Laghari, S. Awan, and A. K. Jumani, “Fourth industrial revolution application: network forensics cloud security issues”, Security Issues and Privacy Concerns in Industry 4.0 Applications, pp. 15–33, 2021.
Sun. X, Liu. P, Singhal. A, "Toward Cyber resiliency in the Context of Cloud Computing [Resilient Security]". IEEE Secur. Priv. 2018, 16, 71–75.
X. Lu, Z. Pan, and H. Xian, “An efficient and secure data sharing scheme for mobile devices in cloud computing”, Journal of Cloud Computing, vol. 9, no. 1, pp. 60–13, 2020.
J. Li, H. Yan, and Y. Zhang, “Identity-based privacy-preserving remote data integrity checking for cloud storage”, IEEE Systems Journal, vol. 15, no. 1, pp. 577–585, 2021.
H.-Y. Lin and Y.-M. Hung, “An improved proxy Re-encryption scheme for IoT-based data outsourcing services in clouds”, Sensors, vol. 21, no. 1, p. 67, 2020.
Abraham, A.T., Thomson Fredrik, E.J. (2021). "Analysis of Task Scheduling Algorithms in Cloud Computing", Turkish Online Journal of Qualitative Inquiry (TOJQI), 12(2), 722–742.
M. Ghobaei-Arani, A. Shahidinejad, "An efficient resource provisioning approach for analyzing cloud workloads: a metaheuristic-based clustering approach", J. Supercomput., 77 (2021), pp. 711-750.
A.S. Voros, et al."The SMART4ALL High Performance Computing Infrastructure: Sharing high-end hardware resources via cloud-based microservices", 2021 31st International Conference on Field-Programmable Logic and Applications (FPL) (2021), pp. 384-385.
D’Silva. D, Ambawade D.D. "Building a zero trust architecture using Kubernetes", In Proceedings of the 2021 6th international conference for convergence in technology (i2ct), Maharashtra, India, 2–4 April 2021; pp. 1–8.
Albuali. A, Mengistu. T, Che. D, "ZTIMM: A zero-trust-based identity management model for volunteer cloud computing", In Proceedings of the International Conference on Cloud Computing, Honolulu, HI, USA, 18–20 September 2020; Springer: Cham, Switzerland, 2020; pp. 287–294.
T. Adityasaisrinivas, K. Govinda, S. S. Manivannan, and E. Swetha, “Analysis of load balancing algorithms using cloud analyst”, International Journal of Recent Technology and Engineering, vol. 6, pp. 684–687, 2019.
S. K. Mishra, B. Sahoo, and P. P. Parida, “Load balancing in cloud computing: a big picture”, Journal of King Saud University - Computer and Information Sciences, vol. 32, no. 2, pp. 149–158, 2020.
S. Y. Mohamed, M. H. N. Taha, H. N. Elmahdy, and H. Harb, “A proposed load balancing algorithm over cloud computing (balanced throttled)”, International Journal of Recent Technology and Engineering, vol. 10, no. 2, pp. 28–33, 2021.
Abraham, A.T., Thomson Fredrik, E.J. (2022). Ensuring the Security and Load Balancing in the Cloud Environment by BPA-SAB Method. In: Hu, YC., Tiwari, S., Trivedi, M.C., Mishra, K.K. (eds) Ambient Communications and Computer Systems. Lecture Notes in Networks and Systems, vol 356. Springer, Singapore. https://doi.org/10.1007/978-981-16-7952-0_37.
Abraham, A.T., Thomson Fredrik, E.J. (2022). Ensuring the security and balancing the load in the cloud computing by DCRI-RI hybrid method. International Journal of Health Sciences, 6(S2), 9776–9793. https://doi.org/10.53730/ijhs.v6nS2.7559.