IoT-based Secure Data Transmission Prediction using Deep Learning Model in Cloud Computing
Main Article Content
Abstract
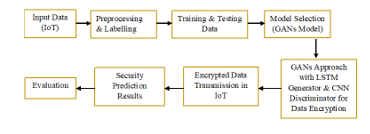
The security of Internet of Things (IoT) networks has become highly significant due to the growing number of IoT devices and the rise in data transfer across cloud networks. Here, we propose Generative Adversarial Networks (GANs) method for predicting secure data transmission in IoT-based systems using cloud computing. We evaluated our model’s attainment on the UNSW-NB15 dataset and contrasted it with other machine-learning (ML) methods, comprising decision trees (DT), random forests, and support vector machines (SVM). The outcomes demonstrate that our suggested GANs model performed better than expected in terms of precision, recall, F1 score, and area under the receiver operating characteristic curve (AUC-ROC). The GANs model generates a 98.07% accuracy rate for the testing dataset with a precision score of 98.45%, a recall score of 98.19%, an F1 score of 98.32%, and an AUC-ROC value of 0.998. These outcomes show how well our suggested GANs model predicts secure data transmission in cloud-based IoT-based systems, which is a crucial step in guaranteeing the confidentiality of IoT networks.
Article Details
References
H. Qiao, J. O. Blech, and H. Chen, “A Machine learning based intrusion detection approach for industrial networks,” in 2020 IEEE International Conference on Industrial Technology (ICIT), 2020. doi: 10.1109/ICIT45562.2020.9067253
S. K. Nukavarapu and T. Nadeem, “Securing edge-based IoT networks with semi-supervised GANs,” in 2021 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), 2021. doi: https://doi.org/10.1109/PerComWorkshops51409.2021.9431112.
K. L. Neela and V. Kavitha, “Blockchain based Chaotic Deep GAN Encryption scheme for securing medical images in a cloud environment,” Appl. Intell., 2022. doi: https://doi.org/10.1007/s10489-022-03730-x
N. McLaughlin et al., “Deep Android Malware Detection,” in Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, 2017. doi: https://doi.org/10.1145/3029806.3029823
A. Ferdowsi and W. Saad, “Deep learning for signal authentication and security in massive internet-of-things systems,” IEEE Trans. Commun., vol. 67, no. 2, pp. 1371–1387, 2019. doi: https://doi.org/10.1109/TCOMM.2018.2878025.
T. Shibahara, T. Yagi, M. Akiyama, D. Chiba, and T. Yada, “Efficient dynamic malware analysis based on network behavior using deep learning,” in 2016 IEEE Global Communications Conference (GLOBECOM), 2016. doi: 10.1109/GLOCOM.2016.7841778.
S. Mizuno, M. Hatada, T. Mori, and S. Goto, “BotDetector: A robust and scalable approach toward detecting malware-infected devices,” in 2017 IEEE International Conference on Communications (ICC), Paris, France, 2017, pp. 1-7 2017. doi: https://doi.org/10.1109/ICC.2017.7997372.
D. Min, Z. Xiao, B. Sheng, H. Quanyong, and P. Xuwei, “Design and implementation of heterogeneous IOT gateway based on dynamic priority scheduling algorithm,” Trans. Inst. Meas. Control, vol. 36, no. 7, pp. 924–931, 2014. doi: 10.1177/0142331214527600
D. Berman, A. Buczak, J. Chavis, and C. Corbett, “A survey of deep learning methods for cyber security,” Information (Basel), vol. 10, no. 4, p. 122, 2019. doi: https://doi.org/10.3390/info10040122.
A. H. Syed and T. Khan, “Machine learning-based application for predicting risk of type 2 diabetes mellitus (T2DM) in Saudi Arabia: A retrospective cross-sectional study,” IEEE Access, vol. 8, pp. 199539–199561, 2020. doi: https://doi.org/10.1109/ACCESS.2020.3035026.
D. Sivaganesan, “Design and development Ai-enabled edge computing for intelligent-iot applications,” December 2019, vol. 2019, no. 02, pp. 84–94, 2019. doi: 10.36548/jtcsst.2019.2.002
S. K. Sood, “Mobile fog based secure cloud-IoT framework for enterprise multimedia security,” Multimed. Tools Appl., vol. 79, no. 15–16, pp. 10717–10732, 2020. doi: https://doi.org/10.1007/s11042-019-08573-2
D. S. Smys, D. A. Basar, and D. H. Wang, “CNN based flood management system with IoT sensors and cloud data,” December 2020, vol. 2, no. 4, pp. 194–200, 2020. doi: https://doi.org/10.36548/jaicn.2020.4.001.
D. R. Bestak and D. S. Smys, “Big data analytics for smart cloud-fog based applications,” December 2019, vol. 2019, no. 02, pp. 74–83, 2019. doi: DOI: https://doi.org/10.36548/jtcsst.2019.2.001.
R. Denis and P. Madhubala, “Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare systems,” Multimed. Tools Appl., vol. 80, no. 14, pp. 21165–21202, 2021. doi: https://doi.org/10.1007/s11042-021-10723-4
B. Kolosnjaji, A. Zarras, G. Webster, and C. Eckert, “Deep learning for classification of malware system call sequences,” in AI 2016: Advances in Artificial Intelligence, Cham: Springer International Publishing, 2016, pp. 137–149. doi: https://doi.org/10.1007/978-3-319-50127-7_11.
J. Wu, W. Xia, G. Zhu, H. Liu, L. Ma, and J. Xiong, “Image encryption based on adversarial neural cryptography and SHA controlled chaos,” J. Mod. Opt., vol. 68, no. 8, pp. 409–418, 2021. doi: https://doi.org/10.1080/09500340.2021.1900440.
Y. Ding, F. Tan, Z. Qin, M. Cao, K.-K. R. Choo, and Z. Qin, “DeepKeyGen: A deep learning-based stream cipher generator for medical image encryption and decryption,” IEEE Trans. Neural Netw. Learn. Syst., vol. 33, no. 9, pp. 4915–4929, 2022. doi: https://doi.org/10.1109/TNNLS.2021.3062754.