Moulded RSA and DES (MRDES) Algorithm for Data Security
Main Article Content
Abstract
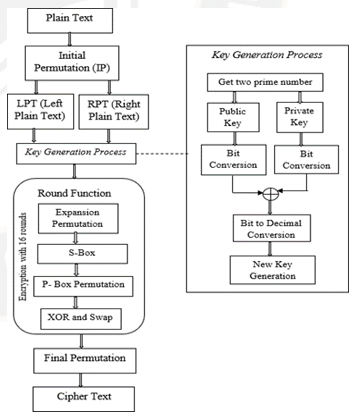
In the recent days transmission of large amount of data through online is very prominent. Security is necessary while transmitting large amount of data. Since the data may belost or hacked at some point of transmission. Normally there are three important factors interms of security. They are key generation, encryption and decryption. There are two types of crypto system namely symmetric cryptosystem and asymmetric cryptosystem. There are many publicly available cryptosystems. It may lead the intruders to view the original message sent by the sender using all the possible keys. In order to provide secure transmission of data, a novel encryption algorithm is proposed by analyzing all the existing algorithms. The existing Rivest–Shamir–Adleman (RSA) and Data encryption standard (DES) algorithm are moulded together rto produce the proposed MRDES encryption algorithm. The performance of the proposed Moulded RSA and DES is higher than the existing encryption algorithms and provides higher data security.
Article Details
References
R.A Popa, and Zeldovich, “Multi-Key Searchable Encryption”, IACR Cryptologye Print Archive, pp.508, 2013.
C.K. Chu, S.S. Chow, W.G. Tzeng, J. Zhou, and R.H. Deng, “Key Aggregate Cryptosystem for Scalable Data Sharing in Cloud Storage”, IEEE Transactions on Parallel and Distributed Systems, vol.25, no.2, pp.468-477, 2014.
M.S.P. Jadhav, and B.R. walkar, “Efficient Cloud Computing with Secure Data Storage using AES”, International Journal of Advanced Research in Computer and Communication Engineering, vol. 4, issue 6, pp. 377-381, 2015.
P.V. Nithyabharathi, T. Kowsalya, and V. Baskar, “To Enhance Multimedia Security in Cloud Computing Environment Using RSA and AES”, International Journal of Science, Engineering and Technology Research (IJSETR), vol. 3, no. 2, pp.341-345, 2014.
Ghavghave, S. Rashmi, and Deepali M. Khatwar, “Architecture for Data Security in Multi-Cloudusing AES-256 Encryption Algorithm”, International Journal on Recent and Innovation Trends in Computing and Communication, PP. 2321-8169, May 2015.
D.W. Chadwick, and K. Fatema, “A Privacy Preserving Authorization System for the Cloud”, J.Computing System Science, vol. 78, no. 5, pp.1359-1373, 2012.
S. Hou, T.Uehara, S.M.Yiu, L.C.K.Huiand K.P.Chow, “Privacy Preserving Confidential Forensic Investigation for Shared or Remote Servers”, Proceeding of 7th International Conference on Intelligent Information Hiding and Multimedia Signal Processing, IEEE, 2011, pp: 378-383, DOI: http://dx.doi.org/10.1109/IIHMSP.2011.28
S. Pearson Y. Shen and M. Mowbray, “A privacy manager for cloud computing”, In:Jaatun, M.G,G. Zhao and C. Rong (Eds.), CloudCom. LNCS 5931, Springer-Verlag, Berlin, Heidelberg, pp: 90-106. 2009.
Rizvi, Sam, “Performance analysis of AES and Two Fish Encryption Schemes”, International Conference on Communication Systems and Network Technologies.58, 2011.
D. Deepali Rane, “Superiority Two fish over Blowfish”, International Journal of Scientific research and management (IJSRM), vol. 4, pp. 2321-3418, 2016.
K. Lakshmi Narayanan, “Performance Evaluation of Cryptographic Algorithms: AES and Blowfish”, International Journal of Technology and Engineering Science [IJTES]TM, vol.1,no. 7, pp. 1064-1069. 34. 2013.
Thakur, Jawahar, and Nagesh Kumar, “DES, AES and Blowfish: Symmetric key cryptography algorithm ssimulation-based performance analysis”, International journal of emerging technology and advanced engineering, pp.6-12. February 2011.
Monika Agrawal and Pradeep Moshra, “A Comparative Survey on Symmetric Key Encryption Algorithm”, International Journal on Computer Science and Engineering(IJCSE),2014.
Ayushi, “A Symmetric Key Cryptographic Algorithm”, International Journal of Computer Applications (IJCA), ISSN:0975– 8887)Vol. 1– No.15, 2010.
SuyashVerma, Rajnish Choubey and RoopaliSoni, “An Efficient Developed New Symmetric Key Cryptography Algorithm for Information Security”, International Journal of Emerging Technology and Advanced Engineering, ISSN 2250-2459, vol.2, no.7, 2012.
Prerna Mahajan and Abhishek Sachdeva, “A Study of Encryption Algorithms AES, DES and RSA for Security”, Global Journal of Computer Science and Technology Network,Web & Security, Volume13, Issue15, Version 1.0, 2013.
Abhishek Joshi, Mohammad Wazid and R. H. Goudarc, “An Efficient Cryptographic Schemefor Text Message Protection against Brute Force and Cryptanalytic Attacks”, International Conference on Intelligent Computing, Communication & Convergence(ICCC), 2014.
Ashraf Odeh, Shadi R. Masadeh and Ahmad Azzazi, “A Performance Evaluation of Common Encryption Techniques with Secure Watermark System(SWS)”, International Journal of Network Security & Its Applications (IJNSA), Vol.7, No.3, 2015.
A.K. Bermani, T.A. Murshedi, and Z. A. Abod, “A hybrid cryptography technique for data storage on cloud computing”, Journal of Discrete Mathematical Sciences and Cryptography, vol. 24, no. 6, pp. 1613-1624, 2021.
E.Y. Baagyere, P. A. N., Agbedemnab, Z. Qin, M. I. Daabo, and Z. Qin, “A multi-layered data encryption and decryption scheme based on genetic algorithm and residual numbers”. IEEEAccess, 8, pp.100438-100447, 2020.
P. Chinnasamy, S. Padmavathi, R. Swathy, and S. Rakesh, “Efficient data security using hybrid cryptography on cloud computing”, InInventive Communication and Computational Technologies, pp.537-547, Springer, Singapore, 2021.