Analysing the Security Aspects of IoT using Blockchain and Cryptographic Algorithms
Main Article Content
Abstract
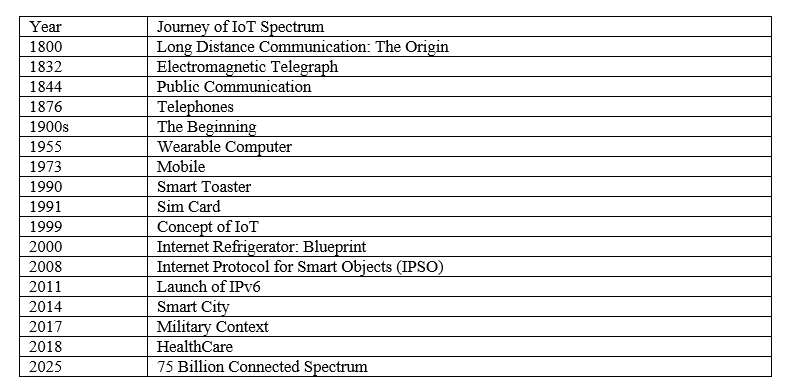
Technological advancement is a never-ending field that shows its evolution from time to time. In 1832, with the invention of the electromagnetic telegraph, the era of the Internet of Things (IoT) began. Within the time of 190 years, this technological domain has revolutionized IoT and made it omnipresent. However, with this evolved and omnipresent nature of IoT, many drawbacks, privacy, interoperability, and security issues have also been generated. These different concerns should be tackled with some newer technologies rather than the conventional ones as somehow, they are only the generator of those issues. Outdated Security could be an appropriate issue of IoT along with the centralized point of failure. It also possesses more concerns and challenges to tackle. On the other side, there is a visible solution to address the challenges of IoT in this developing domain of technology. The visible approach is Blockchain which acted as the backbone in securing Bitcoin in 2008, which was created by the pseudo group named Satoshi Nakamoto. Blockchain has evolved from Blockchain 1.0 to Blockchain 4.0 as the latest one depicts its amalgamation with another component of Industry 4.0 i.e., Artificial Intelligence (AI). AI will give the ability to think logically and like humans. In addition to this SMART solution, there is also an advanced cryptographical technique known as the Elliptic Curve Digital Signature Algorithm (ECDSA) which can enhance the security spectrum of IoT if applied appropriately. This paper produces a vision to enhance and optimize the security of IoT using a network peer-to-peer technology Blockchain along with advanced cryptography.
Article Details
References
Saleh, M. E., Aly, A. A., & Omara, F. A. (2016). Data security using cryptography and steganography techniques. International Journal of Advanced Computer Science and Applications, 7(6), 390-397.
Roberts, W. (1843). History of Letter-writing: From the Earliest Period to the Fifth Century... W. Pickering.
Kotola, B. S. (2020). Application of modulus theory to crytographic system. International Journal of Advanced Research in Engineering and Applied Sciences, 9(1), 19-33.
Adhikari, M. R., & Adhikari, A. (2014). Introduction to Mathematical Cryptography. In Basic Modern Algebra with Applications (pp. 517-584). Springer, New Delhi.
Tulpan, D., Regoui, C., Durand, G., Belliveau, L., & Léger, S. (2013). HyDEn: a hybrid steganocryptographic approach for data encryption using randomized error-correcting DNA codes. BioMed research international, 2013.
Kaur, A., Verma, H. K., & Singh, R. K. (2012). 3D (4 X 4 X 4)-Playfair Cipher. International Journal of Computer Applications, 51(2).
Lozupone, V. (2018). Analyze encryption and public key infrastructure (PKI). International Journal of Information Management, 38(1), 42-44.
Verma, R., Dhanda, N., & Nagar, V. (2022). Enhancing Security with In-Depth Analysis of Brute-Force Attack on Secure Hashing Algorithms. In Proceedings of Trends in Electronics and Health Informatics (pp. 513-522). Springer, Singapore.
Al-Duri, A. S. (2021). Enigma Evolution & Cryptanalysis. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(14), 5566-5569.
Cawthorne, N. (2014). Alan Turing: The Enigma Man. Arcturus Publishing.
Rousseau, R. (2002). Claude Shannon: scientist-engineer. Journal of Henan Normal University, 30(4), 1-13.
Arnold, M., Bellamy, R. K., Hind, M., Houde, S., Mehta, S., Mojsilovi?, A., ... & Varshney, K. R. (2019). FactSheets: Increasing trust in AI services through supplier's declarations of conformity. IBM Journal of Research and Development, 63(4/5), 6-1.
Coppersmith, D. (1994). The Data Encryption Standard (DES) and its strength against attacks. IBM journal of research and development, 38(3), 243-250.
Ingle, S. S., Bhalekar, P. M., & Pathak, K. S. (2014). Using Advanced Encryption Standard (AES) Algorithm Upgrade the Security Level of ATM Banking Systems. Int. J. Res. Sci. Technol., 1(2), 1-7.
Bektas, Y. (2001). Displaying the American genius: the electromagnetic telegraph in the wider world. The British Journal for the History of Science, 34(2), 199-232.
Verma, R., Dhanda, N., & Nagar, V. (2022). Security Concerns in IoT Systems and Its Blockchain Solutions. In Cyber Intelligence and Information Retrieval (pp. 485-495). Springer, Singapore.
Verma, R., Dhanda, N., Nagar, V. (2023). Towards a Secured IoT Communication: A Blockchain Implementation Through APIs. In: Singh, P.K., Wierzcho?, S.T., Tanwar, S., Rodrigues, J.J.P.C., Ganzha, M. (eds) Proceedings of Third International Conference on Computing, Communications, and Cyber-Security. Lecture Notes in Networks and Systems, vol 421. Springer, Singapore. https://doi.org/10.1007/978-981-19-1142-2_53
Verma, R., Dhanda, N., Nagar, V. (2023). Application of Truffle Suite in a Blockchain Environment. In: Singh, P.K., Wierzcho?, S.T., Tanwar, S., Rodrigues, J.J.P.C., Ganzha, M. (eds) Proceedings of Third International Conference on Computing, Communications, and Cyber-Security. Lecture Notes in Networks and Systems, vol 421. Springer, Singapore. https://doi.org/10.1007/978-981-19-1142-2_54
Ghosh, A., Anwar, F., Sarkar, A., Sarkar, S., Bose, S., Aditya, S., & Saha, D. (2021). Applications of Blockchain Technology in Financial & Personal Data Security. American Journal of Electronics & Communication, 2(2), 5-11.
???????, ?. ?., ?????????, ?. ?., ????????, ?. ?., ????????, ?. ?., & ????????, ?. ?. (2020). Analysis and solution of the conceptual and terminological problem of the Blockchain concept definition. European scientific journal of Economic and Financial innovation, (2), 14-36.
Perera, S., Nanayakkara, S., Rodrigo, M. N. N., Senaratne, S., & Weinand, R. (2020). Blockchain technology: Is it hype or real in the construction industry?. Journal of Industrial Information Integration, 17, 100125.
Shrimali, B., & Patel, H. B. (2021). Blockchain state-of-the-art: architecture, use cases, consensus, challenges and opportunities. Journal of King Saud University-Computer and Information Sciences.
Panda, M. (2014). Security in wireless sensor networks using cryptographic techniques. American Journal of Engineering Research (AJER), 3(01), 50-56.
Hasanova, H., Baek, U. J., Shin, M. G., Cho, K., & Kim, M. S. (2019). A survey on blockchain cybersecurity vulnerabilities and possible countermeasures. International Journal of Network Management, 29(2), e2060.
Jamgekar, R. S., & Joshi, G. S. (2013). File encryption and decryption using secure RSA. International Journal of Emerging Science and Engineering (IJESE), 1(4), 11-14.
Johnson, D., Menezes, A., & Vanstone, S. (2001). The elliptic curve digital signature algorithm (ECDSA). International journal of information security, 1(1), 36-63.
Madhuravani, B., & Murthy, D. S. R. (2013). Cryptographic hash functions: SHA family. Int J Innov Technol Explor Eng, 2, 326-9.
Kong, J. H., Ang, L. M., & Seng, K. P. (2015). A comprehensive survey of modern symmetric cryptographic solutions for resource constrained environments. Journal of Network and Computer Applications, 49, 15-50.
Akinyede, R. O., Adegbenro, S. O., & Omilodi, B. M. (2020). A security model for preventing e-Commerce related crimes. Applied Computer Science, 16(3), 30-41. doi:10.23743/acs-2020-19.
Rajat Verma, Namrata Dhanda, Vishal Nagar, "Enhancing & Optimizing Security of IoT Systems using Different Components of Industry 4.0." International Journal of Engineering Trends and Technology, vol. 70, no. 7, pp. 147-157, 2022. Crossref, https://doi.org/10.14445/22315381/IJETT-V70I7P216
Verma, R., Dhanda, N., & Nagar, V. (2020). Addressing the issues & challenges of internet of things using blockchain technology. International Journal of Advanced Science and Technology, 29, 10074–10082.