A Novel Hybrid Spotted Hyena-Swarm Optimization (HS-FFO) Framework for Effective Feature Selection in IOT Based Cloud Security Data
Main Article Content
Abstract
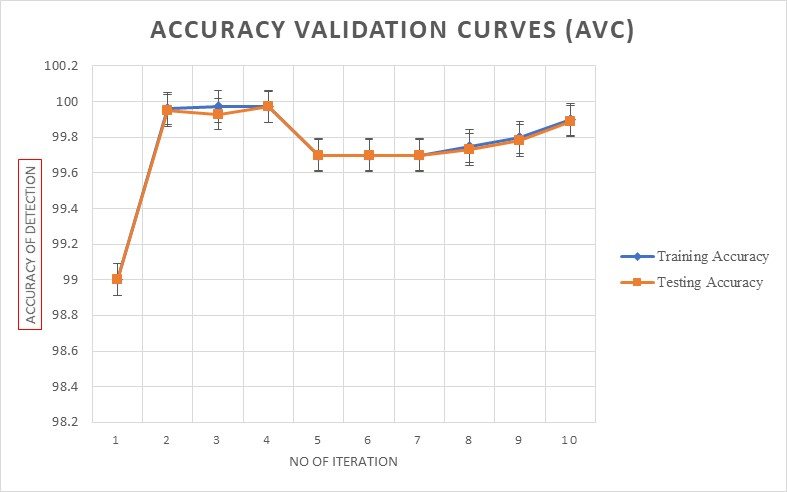
Internet of Things (IoT) has gained its major insight in terms of its deployment and applications. Since IoT exhibits more heterogeneous characteristics in transmitting the real time application data, these data are vulnerable to many security threats. To safeguard the data, machine and deep learning based security systems has been proposed. But this system suffers the computational burden that impedes threat detection capability. Hence the feature selection plays an important role in designing the complexity aware IoT systems to defend the security attacks in the system. This paper propose the novel ensemble of spotted hyena with firefly algorithm to choose the best features and minimise the redundant data features that can boost the detection system's computational effectiveness. Firstly, an effective firefly optimized feature correlation method is developed. Then, in order to enhance the exploration and search path, operators of fireflies are combined with Spotted Hyena to assist the swarms in leaving the regionally best solutions. The experimentation has been carried out using the different IoT cloud security datasets such as NSL-KDD-99 , UNSW and CIDCC -001 datasets and contrasted with ten cutting-edge feature extraction techniques, like PSO (particle swarm optimization), BAT, Firefly, ACO(Ant Colony Optimization), Improved PSO, CAT, RAT, Spotted Hyena, SHO and BOC(Bee-Colony Optimization) algorithms. Results demonstrates the proposed hybrid model has achieved the better feature selection mechanism with less convergence time and aids better for intelligent threat detection system with the high performance of detection.
Article Details
References
Lim, S.Y.; Kiah, M.M.; Ang, T.F. Security Issues and Future Challenges of Cloud Service Authentication.Polytech. Hung. 2017, 14, 69–89.
Borylo, P.; Tornatore, M.; Jaglarz, P.; Shahriar, N.; Cholda, P.; Boutaba, R. Latency and energy-aware provisioning of network slices in cloud networks. Comput. Commun. 2020, 157, 1–19.
Carmo, M.; Dantas Silva, F.S.; Neto, A.V.; Corujo, D.; Aguiar, R. Network-Cloud Slicing Definitions for Wi-Fi Sharing Systems to Enhance 5G Ultra-Dense Network Capabilities. Wirel. Commun. Mob. Comput. 2019, 2019, 1–17.
Dang, L.M.; Piran, M.; Han, D.; Min, K.; Moon, H. A Survey on Internet of Things and Cloud Computing for healthcare. Electronics 2019, 8, 768.
Srinivasamurthy, S.; Liu, D. Survey on Cloud Computing Security. 2020. Available online: https://www.semanticscholar.org/ (accessed on 19 July 2020).
Mathkunti, N. Cloud Computing: Security Issues. Int. J. Comput. Commun. Eng. 2014, 3, 259–263
Stefan, H.; Liakat, M. Cloud Computing Security Threats And Solutions. J. Cloud Comput. 2015, 4, 1.
Palumbo, F.; Aceto, G.; Botta, A.; Ciuonzo, D.; Persico, V.; Pescapé, A. Characterizing Cloud-to-user Latency as perceived by AWS and Azure Users spread over the Globe. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Taipei, Taiwan, 7–11 December 2019; pp. 1–6.
Hussein, N.H.; Khalid, A. A survey of Cloud Computing Security challenges and solutions. Int. J. Comput.Sci. Inf. Secur. 2017, 1, 52–56.
Le Duc, T.; Leiva, R.G.; Casari, P.; Östberg, P.O. Machine Learning Methods for Reliable Resource Provisioning in Edge-Cloud Computing: A Survey. ACM Comput. Surv. 2019, 52, 1–39.
Callara, M.; Wira, P. User Behavior Analysis with Machine Learning Techniques in Cloud Computing Architectures. In Proceedings of the 2018 International Conference on Applied Smart Systems, Médéa, Algeria, 24–25 November 2018; pp. 1–6.
Khan, A.N.; Fan, M.Y.; Malik, A.; Memon, R.A. Learning from Privacy Preserved Encrypted Data on Cloud Through Supervised and Unsupervised Machine Learning. In Proceedings of the International Conference on Computing, Mathematics and Engineering Technologies, Sindh, Pakistan, 29–30 January 2019; pp. 1–5.
Khilar, P.; Vijay, C.; Rakesh, S. Trust-Based Access Control in Cloud Computing Using Machine Learning. In Cloud Computing for Geospatial Big Data Analytics; Das, H., Barik, R., Dubey, H., Roy, D., Eds.; Springer: Cham, Switzerland, 2019; Volume 49, pp. 55–79.
Bhamare, D.; Salman, T.; Samaka, M.; Erbad, A.; Jain, R. Feasibility of Supervised Machine Learning for Cloud Security. In Proceedings of the International Conference on Information Science and Security, Jaipur, India, 16–20 December 2016; pp. 1–5.
Li, C.; Song, M.; Zhang, M.; Luo, Y. Effective replica management for improving reliability and availability in edge-cloud computing environment. J. Parallel Distrib. Comput. 2020, 143, 107–128.
M. A. Elsayed and M. Zulkernine, "PredictDeep: Security Analytics as a Service for Anomaly Detection and Prediction," in IEEE Access, vol. 8, pp. 45184-45197, 2020, doi: 10.1109/ACCESS.2020.2977325.
D. C. Nguyen, P. N. Pathirana, M. Ding and A. Seneviratne, "Secure Computation Offloading in Blockchain Based IoT Networks With Deep Reinforcement Learning," in IEEE Transactions on Network Science and Engineering, vol. 8, no. 4, pp. 3192-3208, 1 Oct.-Dec. 2021, doi: 10.1109/TNSE.2021.3106956.
J. C. Kimmel, A. D. Mcdole, M. Abdelsalam, M. Gupta and R. Sandhu, "Recurrent Neural Networks Based Online Behavioural Malware Detection Techniques for Cloud Infrastructure," in IEEE Access, vol. 9, pp. 68066-68080, 2021, doi: 10.1109/ACCESS.2021.3077498.
G. Loukas, T. Vuong, R. Heartfield, G. Sakellari, Y. Yoon and D. Gan, "Cloud-Based Cyber-Physical Intrusion Detection for Vehicles Using Deep Learning," in IEEE Access, vol. 6, pp. 3491-3508, 2018, doi: 10.1109/ACCESS.2017.2782159.
S. Garg, K. Kaur, N. Kumar, G. Kaddoum, A. Y. Zomaya and R. Ranjan, "A Hybrid Deep Learning-Based Model for Anomaly Detection in Cloud Datacenter Networks," in IEEE Transactions on Network and Service Management, vol. 16, no. 3, pp. 924-935, Sept. 2019, doi: 10.1109/TNSM.2019.2927886.
P. Abirami, S. Vijay Bhanu and T. K. Thivakaran, "Crypto-Deep Reinforcement Learning Based Cloud Security For Trusted Communication," 2022 4th International Conference on Smart Systems and Inventive Technology (ICSSIT), 2022, pp. 1-10, doi: 10.1109/ICSSIT53264.2022.9716429.
Y. Tao, J. Qiu and S. Lai, "A Hybrid Cloud and Edge Control Strategy for Demand Responses Using Deep Reinforcement Learning and Transfer Learning," in IEEE Transactions on Cloud Computing, vol. 10, no. 1, pp. 56-71, 1 Jan.-March 2022, doi: 10.1109/TCC.2021.3117580.
S. Hizal, Ü. ÇAVU?O?LU and D. AKGÜN, "A new Deep Learning Based Intrusion Detection System for Cloud Security," 2021 3rd International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), 2021, pp. 1-4, doi: 10.1109/HORA52670.2021.9461285.
C. Karri and M. S. R. Naidu, "Deep Learning Algorithms for Secure Robot Face Recognition in Cloud Environments," 2020 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), 2020, pp. 1021-1028, doi: 10.1109/ISPA-BDCloud-SocialCom-SustainCom51426.2020.00154.
W. Wang, X. Du, D. Shan, R. Qin and N. Wang, "Cloud Intrusion Detection Method Based on Stacked Contractive Auto-Encoder and Support Vector Machine," in IEEE Transactions on Cloud Computing, vol. 10, no. 3, pp. 1634-1646, 1 July-Sept. 2022, doi: 10.1109/TCC.2020.3001017.
Q. Lio, J. Li, Y. Zhou and L. Liao “Using spotted hyena optimizer for training feedforward neural networks,” Cognitive Systems Research, vol. 65, pp. 1-16, 2021.
K. Sood, A. Jain and A. Verma, "A hybrid task scheduling approach using firefly algorithm and gravitational search algorithm," 2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), 2017, pp. 2997-3002, doi: 10.1109/ICECDS.2017.8390005.
I. Butun, S. D. Morgera and R. Sankar, “A survey of intrusion detection systems in wireless sensor networks,” IEEE Communications Surveys & Tutorials, vol. 16, no. 1, pp. 266-282, 2014.
I. Andrea, C. Chrysostomou and G. Hadjichristofi, “Internet of Things: security vulnerabilities and challenges,” in Proceedings of IEEE Symposium on Computers and Communication, pp. 180-187, 2015
M. A. Patel and M. M. Patel, “Wormhole attack detection in wireless sensor network,” in Proceedings of International Conference on Inventive Research in Computing Applications, pp. 269-274, 2018.
W. F. de Silva, R. Spolon, R. S. Lobato, A. M. Júnior and M. A. C. Humber, "Particle Swarm Algorithm Parameters Analysis for Scheduling Virtual Machines in Cloud Computing," 2020 15th Iberian Conference on Information Systems and Technologies (CISTI), 2020, pp. 1-6, doi: 10.23919/CISTI49556.2020.9141021.
X. Li, N. Luo, D. Tang, Z. Zheng, Z. Qin and X. Gao, "BA-BNN: Detect LDoS Attacks in SDN Based on Bat Algorithm and BP Neural Network," 2021 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), 2021, pp. 300-307, doi: 10.1109/ISPA-BDCloud-SocialCom-SustainCom52081.2021.00050.
Y. Liu, X. Wang, M. Cheng, J. Wang and Y. Zhang, "An Efficient Task Offloading Strategy in Cloud-Edge Computing Under Deadline Constraints," 2020 IEEE 22nd International Conference on High Performance Computing and Communications; IEEE 18th International Conference on Smart City; IEEE 6th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), 2020, pp. 661-667, doi: 10.1109/HPCC-SmartCity-DSS50907.2020.00085.
Z. -G. Chen et al., "Multiobjective Cloud Workflow Scheduling: A Multiple Populations Ant Colony System Approach," in IEEE Transactions on Cybernetics, vol. 49, no. 8, pp. 2912-2926, Aug. 2019, doi: 10.1109/TCYB.2018.2832640.
Z. Zhou, F. Li, J. H. Abawajy and C. Gao, "Improved PSO Algorithm Integrated With Opposition-Based Learning and Tentative Perception in Networked Data Centres," in IEEE Access, vol. 8, pp. 55872-55880, 2020, doi: 10.1109/ACCESS.2020.2981972.
R. Pushpa and M. Siddappa, "Adaptive Hybrid Optimization Based Virtual Machine Placement in Cloud Computing," 2022 4th International Conference on Smart Systems and Inventive Technology (ICSSIT), 2022, pp. 1-9, doi: 10.1109/ICSSIT53264.2022.9716298.
Z. Xu, X. Liang, M. He and H. Chen, "Multiple Adaptive Strategies-based Rat Swarm Optimizer," 2021 IEEE 7th International Conference on Cloud Computing and Intelligent Systems (CCIS), 2021, pp. 159-163, doi: 10.1109/CCIS53392.2021.9754632.
Kaur, Amandeep & Dhiman, Gaurav & Garg, Meenakshi. (2021). Task Scheduling in Cloud Computing Using Spotted Hyena Optimizer. 10.4018/978-1-7998-5040-3.ch009.
Ulah, Arif & Mohd Nawi, Nazri & Uddin, Jamal & Baseer, Samad. (2019). Artificial Bee Colony algorithm used for load balancing in cloud computing: Review. IAES International Journal of Artificial Intelligence (IJ-AI). 8. 156-167. 10.11591/ijai.v8.i2.pp156-167.