A Novel Design to Minimise the Energy Consumption and Node Traversing in Blockchain Over Cloud Using Ensemble Cuckoo Model
Main Article Content
Abstract
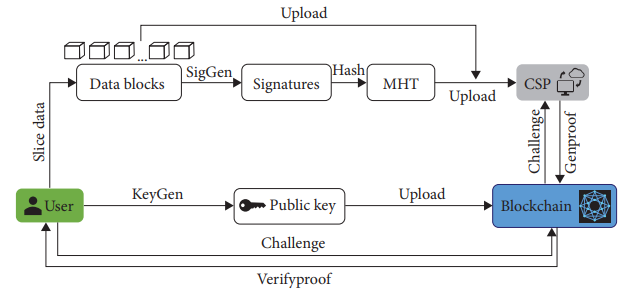
The article outlines the Blockchain’s behavioral model for services. Their reliability is proven through the use of experimental evidence. The authors highlight the major technical aspects and characteristics that are associated with the transmission of data through the network. The authors define the scheme for the network, which works with blockchain transactions, and the relationship between network characteristics on parameters used by the application. They examine the use of this model to identification of the blockchain service and also the likelihood of existing security mechanisms that are based on the technology being bypassed. Additionally, the article provides guidelines to conceal the Blockchain's traffic profile to make it more difficult for its detection in the information network. This study offers a thorough analysis of blockchain-based trust models applied to cloud computing. The paper highlights the challenges that remain unsolved and offers suggestions for future studies in the area based on new cloud-edge trust management system and double-blockchain structure, which is a cloud-based transaction model. The paper also identifies the existing challenges and offers suggestions for future studies in the area based on new cloud-edge trust management system and double-blockchain structure, which is a cloud-based transaction model. The flow of the network will be supported by models that are enhanced by cuckoo to frame the perfect network transform of data from one point to cluster, or alternatively.
Article Details
References
S. Nepal, S. Chen, J. Yao, and D. Thilakanathan, “DIaaS: Data Integrity as a Service in the Cloud,” in Proceedings of the 2011 IEEE 4th International Conference on Cloud Computing, pp. 308–315, IEEE, Washington, DC, USA, 2011.
T. Ristenpart, E. Tromer, H. Shacham, and S. Savage, “Hey, you, get off of my cloud: exploring information leakage in third-party compute clouds,” in Proceedings of the 16th ACM Conference on Computer and Communications Security, pp. 199–212, ACM, New York, NY, USA, 2009.
G. Ateniese, R. Burns, R. Curtmola et al., “Provable data possession at untrusted stores,” in Proceedings of the 14th ACM Conference on Computer and Communications Security, pp. 598–609, ACM, New York, NY, USA, 2007.
M. Crosby, P. Pattanayak, S. Verma, and V. Kalyanaraman, “Blockchain technology: beyond bitcoin,” Applied Innovation, vol. 71, no. 2, pp. 6–10, 2016.
W. S. H. M. W. Ahmad, N. A. M. Radzi, F. S. Samidi et al., “5G technology: towards dynamic spectrum sharing using cognitive radio networks,” IEEE Access, vol. 8, pp. 14460–14488, 2020.
J. Su, R. Xu, S. Yu, B. Wang, and J. Wang, “Idle slots skipped mechanism based tag identification algorithm with enhanced collision detection,” KSII Transactions on Internet and Information Systems, vol. 14, no. 5, pp. 2294–2309, 2020.
J. Su, R. Xu, S. Yu, B. Wang, and J. Wang, “Redundant rule detection for software-defined networking,” KSII Transactions on Internet and Information Systems, vol. 14, no. 6, pp. 2735–2751, 2020.
X. Jiang, J. Yu, J. Yan, and R. Hao, “Enabling efficient and verifiable multi-keyword ranked search over encrypted cloud data,” Information Sciences, vol. 403-404, pp. 22–41, 2017.
Z. Zhou, Q. M. J. Wu, Y. Yang, and X. Sun, “Region-level visual consistency verification for large-scale partial-duplicate image search,” ACM Transactions on Multimedia Computing, Communications, and Applications, vol. 16, no. 2, pp. 1–25, 2020.
Z. Zhou, Y. Mu, and Q. M. J. Wu, “Coverless image steganography using partial-duplicate image retrieval,” Soft Computing, vol. 23, no. 13, pp. 4927–4938, 2019.
G. Ateniese, R. Di Pietro, L. V. Mancini, and G. Tsudik, “Scalable and efficient provable data possession,” in Proceedings of the 4th International Conference on Security and Privacy in Communication Netowrks, pp. 1–10, ACM, New York, NY, USA, 2008.
C. C. Erway, A. K¨upç¨u, C. Papamanthou, and R. Tamassia, “Dynamic provable data possession,” ACM Transactions on Information and System Security, vol. 17, no. 4, pp. 1–29, 2015.
C. Wang, S. S. M. Chow, Q. Wang, K. Ren, and W. Lou, “Privacy-preserving public auditing for secure cloud storage,” IEEE Transactions on Computers, vol. 62, no. 2, pp. 362–375, 2013.
E. Zhou, Z. Li, H. Guo, and Y. Jia, “An improved data integrity verification scheme in cloud storage system,” Acta Electronica Sinica, vol. 42, no. 1, pp. 150–154, 2014.
Y. Zhu, H. Wang, Z. Hu et al., “Dynamic audit services forintegrity verification of outsourced storages in clouds,” “, ACM, in Proceedings of the 2011 ACM Symposium on Applied Computing, pp. 1550–1557, ACM, New York, NY, USA, 2011.
Y. Zhu, G. J. Ahn, H. Hu et al., “Dynamic audit services for outsourced storages in clouds,” IEEE Transactions on Services Computing, vol. 6, no. 2, pp. 227–238, 2011.
K. Yang and X. Jia, “An efficient and secure dynamic auditing protocol for data storage in cloud computing,” IEEE Transactions on Parallel and Distributed Systems, vol. 24, no. 9, pp. 1717–1726, 2012.
J. Ni, Y. Yu, Y. Mu, and Q. Xia, “On the security of an efficient dynamic auditing protocol in cloud storage,” IEEE Transactions on Parallel and Distributed Systems, vol. 25, no. 10, pp. 2760-2761, 2013.
G. Xu, Y. Bai, C. Yan et al., “Check algorithm of data integrity verification results in Big data storage,” Journal of Computer Research and Development, vol. 54, no. 11, pp. 2487–2496, 2017.
W. Shen, J. Qin, J. Yu, R. Hao, and J. Hu, “Enabling identitybased integrity auditing and data sharing with sensitive information hiding for secure cloud storage,” IEEE Transactions on Information Forensics and Security, vol. 14, no. 2, pp. 331–346, 2019.
A. Li, S. Tan, and Y. Jia, “A method for achieving provable data integrity in cloud computing,” Ee Journal of Supercomputing, vol. 75, no. 1, pp. 92–108, 2019.
H. Zhu, Y. Yuan, Y. Chen et al., “A secure and efficient data integrity verification scheme for cloud-IoT based on short signature,” IEEE Access, vol. 7, pp. 90036–90044, 2019.
K. Huang, M. Xian, S. Fu, and J. Liu, “Securing the cloud storage audit service: defending against frame and collude attacks of third party auditor,” IET Communications, vol. 8, no. 12, pp. 2106–2113, 2014.
Y. Wu, X. Lin, X. Lu, J. Su, and P. Chen, “A secure light-weight public auditing scheme in cloud computing with potentially malicious third-party auditor,” IEICE Transactions on Information and Systems, vol. E99.D, no. 10, pp. 2638–2642, 2016.
Shere, R., Shrivastava, S., & Pateriya, R. K. (2017). CloudSim Framework for Federation of identity management in Cloud Computing. International Journal of Computer Engineering in Research Trends, 4(6), 269–276.
PRAVEEN KUMAR, & S.NAGA LAKSHMI. (2015). Efficient Data Access Control for Multi-Authority Cloud Storage using CP-ABE. International Journal of Computer Engineering in Research Trends, 2(12), 1182-1187. Retrieved from https://www.ijcert.org.
Prakash, P. S., Janardhan, M., Sreenivasulu, K., Saheb, S. I., Neeha, S., & Bhavsingh, M. (2022). Mixed linear programming for charging vehicle scheduling in large-scale rechargeable WSNs. Journal of Sensors, 2022, 1-13. doi:10.1155/2022/8373343
Yedukondalu, G., Samunnisa, K., Bhavsingh, M., Raghuram, I. S., & Lavanya, A. (2022). MOCF: A multi-objective clustering framework using an improved particle swarm optimization algorithm. International Journal on Recent and Innovation Trends in Computing and Communication, 10(10), 143-154. doi:10.17762/ijritcc.v10i10.5743