AODV (ST_AODV) on MANETs with Path Security and Trust-based Routing
Main Article Content
Abstract
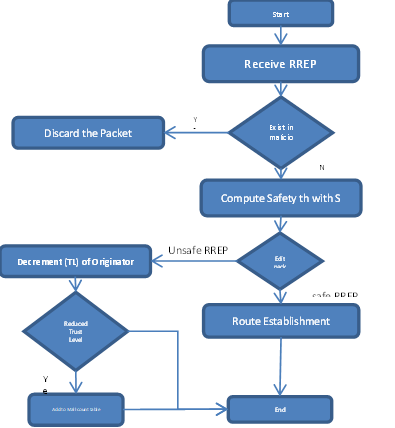
The nodes of the MANET are connected by an autonomous that has no predetermined structure (Mobile ad hoc Network). When a node's proximity to other nodes is maintained dynamically via the use of relying nodes, the MANET network's node-to-node connection is un-trusted because of node mobility. If a node relies on self-resources at any point in time, it runs the risk of acting as a selfish or malicious node, the untrusted selfish or malicious node in the network. An end-to-end routing route that is secure has been presented to enhance the security of the path based on the AODV routing protocol using ST AODV (Secure and Trust ADV). To do this, we must first identify the selfish/malicious nodes in the network and analyse their past activity to determine their current trust levels. A node's stage of belief is indicated by the packet messages it sends. In order to resolve each route, trust must be identified and the path's metadata in RREP must be updated.
Article Details
References
Vijaya Bhaskar Ch, Dr. D S R Murthy, “A path Recovery AODV optimistic Secure Route Reply Protocol in Ad Hoc Mobile Networks,” International Journal of Emerging Technologies and Innovative Research www.jetir.org (ISSN-2349-5162), © 2020 JETIR October 2020, Volume 7, Issue 10, DOI: http://doi.one/10.1729/Journal.24671, Impact Factor: 5.87, ISSN: 2349-5162. http://www.jetir.org/view?paper=JETIR2010063.
K. Cheng, “Smart Phone for Mobile Communication Community,” International Journal of e-Education, e-Business, e-Management and e-Learning, vol. 3, no. 5, 2013.
Y. Mao, J. Wang, B. Sheng, F. Wu, “Building smartphone Ad-Hoc networks with long-range radios” In 2015 IEEE 34th International Performance Computing and Communications Conference (IPCCC), pp. 1-8, 2015.
M. Corson, J. Macker, G. Cirincione, “Internet-based mobile ad hoc networking”, IEEE internet computing, vol. 3, no. 4, pp. 63-70., 1999.
X. Fan, J. Cao, Y. Liu, Y. He, “Gossip-based Cooperative Caching for Mobile Phone Games in IMANETs,” In Parallel and Distributed Systems (ICPADS), 2011 IEEE 17th International Conference, pp. 465-472, 2011.
S. Lim, W. Lee, G. Cao, C. Das, “Cache invalidation strategies for internet-based mobile ad hoc networks,” Computer Communications, vol. 30, no. 8, pp. 1854-1869, 2007.
Vijaya Bhaskar Ch, D.S.R. Murthy,” Qos Metrics for an end to end Stable Routing in MANET,” International Journal of Computer Sciences and Engineering, Vol.6, Issue.12, pp.57-61,Dec-2018,CrossRef-DOI: https://doi.org/10.26438/ijcse/v6i12.5761, E-ISSN: 2347-2693.https://www.ijcseonline.org/full_paper_view.php?paper_id=3293.
H. Yang, H. Luo, F. Ye, S. Lu, L. Zhang, “Security in mobile ad hoc networks: challenges and solutions,” IEEE wireless communications, vol. 11, no. 1, pp. 38-47, 2004.
M. Alani, “MANET security: A survey. In Control System”, Computing and Engineering (ICCSCE), 2014 IEEE International Conference on, pp. 559-564, 2014.
D. Aarti, “Study Of Manet: Characteristics, challenges, application and security attacks,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 3, no. 5, pp. 252-257, 2013.
J. Hoebeke, I. Moerman, B. Dhoedt, P. Demeester, “An overview of mobile ad hoc networks: applications and challenges”, Journal- Communications Network, vol. 3, no. 3, pp. 60-66, 2004.
Vijaya Bhaskar.ch, Dr. D.S.R.Murthy, “ A reliable Routing Approach in Mobile AdHoc Network based on genetic Algorithms” International Journal of Research in Computer and Communication Technology, (IJRCCT) ISSN(o) 2278-5841, ISSN(P) 2320-5156, www.IJRCCT.org, Vol 2, Issue 10, October- 2013, SJIF impact factor 3.751. Corpus ID: 2427122.
S. Umang, B. Reddy, M. Hoda, “Enhanced intrusion detection system for malicious node detection in ad hoc routing protocols using minimal energy consumption,” IET Communications, vol. 4, no. 17, pp. 2084-2094, 2010.
N. Arya, U. Singh, S. Singh, “Detecting and avoiding of wormhole attack and collaborative black hole attack on MANET using trusted AODV routing algorithm,” IEEE International Conference on Computer Communication and Control, IC4 2015, pp. 6–11, 2015.
S. Tan, K. Kim, “Secure route discovery for preventing black hole attacks on AODV-based MANETs,” Proceedings - 2013 IEEE International Conference on High-Performance Computing and Communications, HPCC 2013 and 2013 IEEE International Conference on Embedded and Ubiquitous Computing, EUC 2013, pp. 1159–1164, 2014.
I. Ullah, S. Rehman, “Analysis of Black Hole attack on MANETs Using different MANET routing protocols,” 2010.
R. Glabbeek, P. Höfner, M. Portmann, W. Tan, “Modelling and verifying the AODV routing protocol,” Distributed Computing, vol. 29, no. 4, pp. 279–315, 2016.
I. Woungang, S. Dhurandher, M. Ge, R. Peddi, “A DSR-based routing protocol for mitigating blackhole attacks on mobile ad hoc networks,” Security and Communication Networks, 2013.
V. Singla, P. Kakkar, S. Lecturer, “Traffic Pattern-based performance comparison of Reactive and Proactive protocols of Mobile Ad-hoc Networks,” International Journal of Computer Applications, vol. 5, no. 10, pp. 975–8887, 2010.
P. Jacquet, P. Muhlethaler, T. Clausen, A. Laouiti, A. Qayyum, L. Viennot, “Optimized Link State Routing Protocol for Ad Hoc Networks,” IEEE International Multi-Topic Conference, Lahore, Pakistan, pp. 28-30, 2001.
A. Khatkar, Y. Singh, “Performance Evaluation of Hybrid Routing Protocols in Mobile Ad Hoc Networks,” 2012 Second International Conference on Advanced Computing & Communication Technologies, pp. 542–545, 2012.
S. Marti, T. Giuli, K. Lai, M. Baker, “Mitigating routing misbehavior in mobile ad hoc networks,” Proceedings of the 6th Annual International Conference on Mobile Computing and Networking (MobiCom), pp. 255-265, 2000.
S. Banerjee, “Detection/removal of cooperative black and gray hole attack in mobile ad-hoc networks,” World Congress proceedings on engineering and computer science, pp. 22-24, 2008.
L. Tamilselvan, V. Sankaranarayanan., "Prevention of black hole attack in MANET," The 2nd International Conference on Wireless Broadband and Ultra Wideband Communications IEEE, p. 21, 2007.
R. Jhaveri, S. Patel, D. Jinwala, “Improving route discovery for AODV to prevent black hole and gray hole attacks in MANETs,” INFOCOMP Journal of Computer Science, vol. 11, no. 1, pp. 1-12., 2012.
R. Jhaveri, “MR-AODV: A Solution to Mitigate Blackhole and Grayhole Attacks in AODV Based MANETs,” IEEE Third International Conference on Advanced Computing & Communication Technologies, pp. 254-260, 2013.
C. Bettstetter, H. Hartenstein, X. Pérez-Costa, “Stochastic properties of the random waypoint mobility model,” Wireless Networks, vol. 10, no. 5, pp. 555-567., 2004.
R. Jain, “The art of computer systems performance analysis: techniques for experimental design, measurement, simulation, and modeling,” John Wiley & Sons, 1990.
Vijaya Bhaskar ch, Dr. D.S.R.Murthy, “Create Communication Model For Manet Routing Protocol” - Make in India – A new initiative for IT and Business Excellence –October 27-28, 2016, SNIST.
Vijaya Bhaskar Ch, Dr. D.S.R.Murthy, Dr. V. Kakulapati, “Alternative Reliable routing for Reactive based routing used on recovery management in AODV route optimistic properties.” Proceedings of the 12th INDIACom; INDIACom-2018; IEEE Conference ID: 42835 2018 © INDIACom-2018; ISSN 0973-7529; ISBN 978-93-80544-28-1. IEEE Conference ID: 42835.
P. Goyal, V. Parmar, R. Rishi, “Manet: vulnerabilities, challenges, attacks, application,” IJCEM International Journal of Computational Engineering & Management, vol. 11, pp. 32-37, 2011.
X. Liu, Z. Fang, L. Shi, “Securing Vehicular Ad Hoc Networks. 2007 2nd International Conference on Pervasive Computing and Applications, vol. 15, no. 1, pp. 424–429, 2007
F. Tseng, L. Chou, H. Chao, “A survey of black hole attacks in wireless mobile ad hoc networks,” Human-centric Computing and Information Sciences, vol. 1, no. 1, 2011. learning and depression discrimination." IEEE Access 8 (2020): 30332-30342.