Secure Communication Model for Dynamic Task Offloading in Multi-Cloud Environment
Main Article Content
Abstract
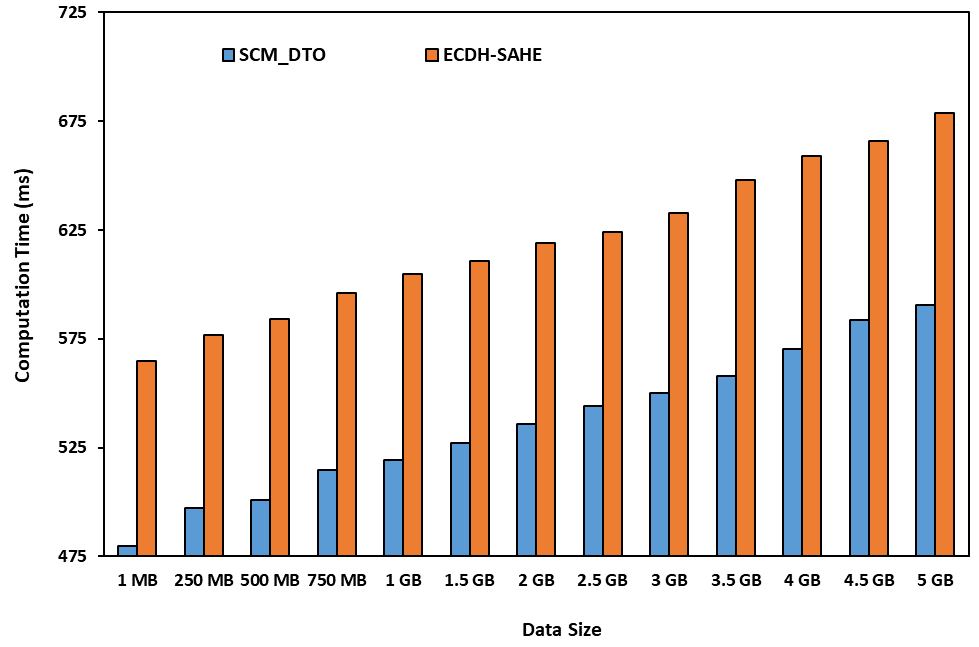
As the data is increasing day-by-day, the mobile device storage space is not sufficient to store the complete information and also the computation capacity also is a limited resource which is not sufficient for performing all the required computations. Hence, cloud computing technology is used to overcome these limitations of the mobile device. But security is the main concern in the cloud server. Hence, secure communication model for dynamic task offloading in multi-cloud environment is proposed in this paper. Cloudlet also is used in this model. Triple DES with 2 keys is used during the communication process between the mobile device and cloudlet. Triple DES with 3 keys is used by the cloudlet while offloading the data to cloud server. AES is used by the mobile device while offloading the data to the cloud server. Computation time, communication time, average running time, and energy consumed by the mobile device are the parameters which are used to evaluate the performance of the proposed system, SCM_DTO. The performance of the proposed system, SCM_DTO is compared with ECDH-SAHE and is proved to be performing better.
Article Details
References
Luo, S., Wen, Y., Xu, W. and Puthal, D., 2019. Adaptive task offloading auction for industrial CPS in mobile edge computing. IEEE Access, 7, pp.169055-169065.
Ren, J., Li, J., Liu, H. and Qin, T., 2021. Task offloading strategy with emergency handling and blockchain security in SDN-empowered and fog-assisted healthcare IoT. Tsinghua Science and Technology, 27(4), pp.760-776.
Rahbari, D. and Nickray, M., 2020. Task offloading in mobile fog computing by classification and regression tree. Peer-to-Peer Networking and Applications, 13(1), pp.104-122.
Jacek Marecki, & Dr. Sunita Chaudhary. (2022). Electrical Structure for Embedded Commuter Vision for Automobile Sector. Acta Energetica, (02), 44–51. Retrieved from http://actaenergetica.org/index.php/journal/article/view/468
Nguyen, D.C., Pathirana, P.N., Ding, M. and Seneviratne, A., 2020. Privacy-preserved task offloading in mobile blockchain with deep reinforcement learning. IEEE Transactions on Network and Service Management, 17(4), pp.2536-2549.
Li, Y., Zeng, D., Gu, L., Zhu, A. and Chen, Q., 2020, December. Task offloading in trusted execution environment empowered edge computing. In 2020 IEEE 26th International Conference on Parallel and Distributed Systems (ICPADS) (pp. 316-323). IEEE.
Gudni Johannesson, & Nazzal Salem. (2022). Design Structure of Compound Semiconductor Devices and Its Applications. Acta Energetica, (02), 28–35. Retrieved from http://actaenergetica.org/index.php/journal/article/view/466
Kim, S., 2020. New application task offloading algorithms for edge, fog, and cloud computing paradigms. Wireless Communications and Mobile Computing, 2020.
Qureshi, D. I. ., & Patil, M. S. S. . (2022). Secure Sensor Node-Based Fusion by Authentication Protocol Using Internet of Things and Rfid. Research Journal of Computer Systems and Engineering, 3(1), 48–55. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/41
Li, J., Dai, M. and Su, Z., 2020. Energy-aware task offloading in the Internet of Things. IEEE Wireless Communications, 27(5), pp.112-117.
Guo, H., Liu, J., Ren, J. and Zhang, Y., 2020. Intelligent task offloading in vehicular edge computing networks. IEEE Wireless Communications, 27(4), pp.126-132.
Samad, A. . (2022). Internet of Things Integrated with Blockchain and Artificial Intelligence in Healthcare System. Research Journal of Computer Systems and Engineering, 3(1), 01–06. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/34
Cozzolino, V., Tonetto, L., Mohan, N., Ding, A.Y. and Ott, J., 2022. Nimbus: Towards Latency-Energy Efficient Task Offloading for AR Services. IEEE Transactions on Cloud Computing.
Ben Ammar, M., Ben Dhaou, I., El Houssaini, D., Sahnoun, S., Fakhfakh, A. and Kanoun, O., 2022. Requirements for Energy-Harvesting-Driven Edge Devices Using Task-Offloading Approaches. Electronics, 11(3), p.383.
Maloth, Bhav Singh. (2016). Privacy-Preserving Scalar Product Computation over Personal Health Records. International Journal of Computer Engineering In Research Trends. 3. 42-46.
Chiba, Z., El Kasmi Alaoui, M. S., Abghour, N., & Moussaid, K. (2022). Automatic Building of a Powerful IDS for The Cloud Based on Deep Neural Network by Using a Novel Combination of Simulated Annealing Algorithm and Improved Self- Adaptive Genetic Algorithm. International Journal of Communication Networks and Information Security (IJCNIS), 14(1). https://doi.org/10.17762/ijcnis.v14i1.5264 (Original work published April 12, 2022)
(2022). Bug2 algorithm-based data fusion using mobile element for IoT-enabled wireless sensor networks. Measurement: Sensors. 100548. 10.1016/j.measen.2022.100548.
Roy, S. S., Mallik, A., Gulati, R., Obaidat, M. S., & Krishna, P. V. (2017, January). A deep learning based artificial neural network approach for intrusion detection. In International Conference on Mathematics and Computing (pp. 44-53). Springer, Singapore
Abouhogail, R. A. (2022). Untraceable Authentication Protocol for IEEE802.11s Standard. International Journal of Communication Networks and Information Security (IJCNIS), 13(3). https://doi.org/10.17762/ijcnis.v13i3.5090 (Original work published December 25, 2021)
Viswanathan, P., & Krishna, P. V. (2013). A joint FED watermarking system using spatial fusion for verifying the security issues of teleradiology. IEEE Journal of Biomedical and Health Informatics, 18(3), 753-764.
Maloth, Bhav Singh & Lakshmi, M & Kumar, Dr & Parashuram, N. (2017). International Journal on Recent and Innovation Trends in Computing and Communication Improved Trial Division Algorithm by Lagrange"s Interpolation Function. International Journal on Recent and Innovation Trends in Computing and Communication. 5. 1227-1231.
Maloth, Bhav Singh & Anusha, R. & Reddy, R. & Devi, S.Chaya. (2013). Augmentation of Information Security by Cryptography in Cloud Computing. www.ijcst.com. 4.