Leveraging Machine Learning for Network Intrusion Detection in Social Internet Of Things (SIoT) Systems
Main Article Content
Abstract
This research investigates the application of machine learning models for network intrusion detection in the context of Social Internet of Things (SIoT) systems. We evaluate Convolutional Neural Network with Generative Adversarial Network (CNN+GAN), Generative Adversarial Network (GAN), and Logistic Regression models using the CIC IoT Dataset 2023. CNN+GAN emerges as a promising approach, exhibiting superior performance in accurately identifying diverse intrusion types. Our study emphasizes the significance of advanced machine learning techniques in enhancing SIoT security by effectively detecting anomalous behaviours within socially interconnected environments. The findings provide practical insights for selecting suitable intrusion detection methods and highlight the need for ongoing research to address evolving intrusion scenarios and vulnerabilities in SIoT ecosystems.
Article Details
References
Bace, R.; Mell, P. Intrusion Detection Systems; NIST Special Publication on Intrusion Detection Systems; NIST: Gaithersburg, MD,USA, 2001.
Mbona, I.; Eloff, J.H.P. Detecting Zero-Day Intrusion Attacks Using Semi-Supervised Machine Learning Approaches. IEEE Access 2022, 10, 69822–69838.
Mishra, P.; Varadharajan, V.; Tupakula, U.; Pilli, E.S. A Detailed Investigation and Analysis of Using Machine Learning Techniquesfor Intrusion Detection. IEEE Commun. Surv. Tutor. 2019, 21, 686–728.
Dhanabal, L.; Shantharajah, S.P. A Study on NSL-KDD Dataset for Intrusion Detection system Based on Classi?cation Algorithms.Int. J. Adv. Res. Comput. Commun. Eng. 2015, 4, 446–452.
Olouhal, O.U.; Yange, T.S.; Okerekel, G.E.; Bakpol, F.S. Cutting Edge Trends in Deception Based Intrusion Detection Systems-ASurvey. J. Inf. Secur. 2021, 12, 250–269.
Asharf, J.; Moustafa, N.; Khurshid, H.; Debie, E.; Haider, W.; Wahab, A. A Review of Intrusion Detection Systems Using Machineand Deep Learning in Internet of Things: Challenges, Solutions and Future Directions. Electronics 2020, 9, 1177.
Prashanth, S.K.; Shitharth, S.; Praveen Kumar, B.; Subedha, V.; Sangeetha, K. Optimal Feature Selection Based on EvolutionaryAlgorithm for Intrusion Detection. SN Comput. Sci. 2022, 3, 439.
Sheikh, M.S.; Peng, Y. Procedures, Criteria, and Machine Learning Techniques for Network Traf?c Classi?cation: A Survey. IEEEAccess 2022, 10, 61135–61158.
NSL-KDD Dataset. Available online:https://www.unb.ca/cic/datasets/nsl.html.
Lin, Z.; Shi, Y.; Xue, Z. IDSGAN: Generative adversarial networks for attack generation against intrusion detection. arXiv 2021,arXiv:1809.02077.
Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative adversarialnetworks. Commun. ACM 2020, 63, 11, 139–144.
Ring, M.; Schlör, D.; Landes, D.; Hotho, A. Flow-based network traf?c generation using Generative Adversarial Networks.Comput. Secur. 2019, 82, 156–172.
Zhu, Y.; Cui, L.; Ding, Z.; Li, L.; Liu, Y.; Hao, Z. Black box attack and network intrusion detection using machine learning formalicious traf?c. Comput. Secur. 2022, 123, 102922.
Balyan, A.K.; Ahuja, S.; Lilhore, U.K.; Sharma, S.K.; Manoharan, P.; Algarni, A.D.; Elmannai, H.; Raahemifar, K. A HybridIntrusion Detection Model Using EGA-PSO and Improved Random Forest Method. Sensors 2022, 22, 5986.
Vaccari, I.; Carlevaro, A.; Narteni, S.; Cambiaso, E.; Mongelli, M. eXplainable and Reliable Against Adversarial Machine Learningin Data Analytics. IEEE Access 2022, 10, 83949–83970.
Dhabliya, M. D. . (2021). Cloud Computing Security Optimization via Algorithm Implementation. International Journal of New Practices in Management and Engineering, 10(01), 22–24. https://doi.org/10.17762/ijnpme.v10i01.99
Fasci, L.S.; Fisichella, G.L.; Qian, C. Disarming visualization-based approaches in malware detection systems. Comput. Secur.2023, 126, 103062.
TensorFlow. 2022. Available online:https://www.tensor?ow.org.
Shitharth, S.; Prince Winston, D. An enhanced optimization-based algorithm for intrusion detection in SCADA network. Comput.Secur. 2017, 70, 16–26.
Neto, E. C. P., Dadkhah, S., & Ghorbani, A. A. (2022). Collaborative DDoS Detection in Distributed Multi-Tenant IoT using Federated Learning. In Proceedings of the 2022 19th Annual International Conference on Privacy, Security & Trust (PST) (pp. 1–10). Fredericton, NB, Canada.
Kaur, B., Dadkhah, S., Xiong, P., Iqbal, S., Ray, S., & Ghorbani, A. A. (2021). Verification based scheme to restrict IoT attacks. In Proceedings of the 2021 IEEE/ACM 8th International Conference on Big Data Computing, Applications and Technologies (BDCAT’21) (pp. 63–68). Leicester, UK.
Velarde-Alvarado, P., Gonzalez, H., Martínez-Peláez, R., Mena, L. J., Ochoa-Brust, A., Moreno-García, E., ... Ostos, R. (2022). A novel framework for generating personalized network datasets for NIDS based on traffic aggregation. Sensors, 22(4), 1847.
Sharma, S., & Kaushik, B. (2019). A survey on internet of vehicles: Applications, security issues & solutions. Vehicular Communications, 20, 100182.
Guerra, J. L., Catania, C., & Veas, E. (2022). Datasets are not enough: Challenges in labeling network traffic. Computers & Security, 120, 102810.
Sa?, M., Dadkhah, S., Shoeleh, F., Mahdikhani, H., Molyneaux, H., & Ghorbani, A. A. (2022). A Survey on IoT Profiling, Fingerprinting, and Identification. ACM Transactions on Internet of Things, 3(1), 1–39.
Elghalhoud, O., Naik, K., Zaman, M., & Goel, N. (2022). Data balancing and hyper-parameter optimization for machine learning algorithms for secure IoT networks. In Proceedings of the 18th ACM International Symposium on QoS and Security for Wireless and Mobile Networks (pp. 71–78). Montreal, QC, Canada.
Abrishami, M., Dadkhah, S., Neto, E. C. P., Xiong, P., Iqbal, S., Ray, S., & Ghorbani, A. A. (2022). Label Noise Detection in IoT Security based on Decision Tree and Active Learning. In Proceedings of the 2022 IEEE 19th International Conference on Smart Communities: Improving Quality of Life Using ICT, IoT and AI (HONET) (pp. 46–53). Marietta, GA, USA.
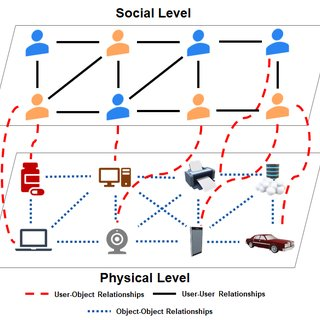
Nie, L., Wu, Y., Wang, X., Guo, L., Wang, G., Gao, X., & Li, S. (2021). Intrusion detection for secure social internet of things based on collaborative edge computing: a generative adversarial network-based approach. IEEE Transactions on Computational Social Systems, 9(1), 134-145.