A Method for Malicious Network Packet Detection based on Anomalous TTL Values
Main Article Content
Abstract
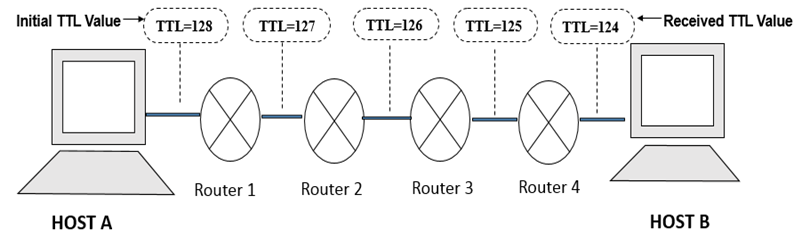
In the current digital age, a pervasive shift towards digitalization is evident in all aspects of life, encompassing entertainment, education, business, and more. Consequently, the demand for internet access has surged, paralleled therefore unfortunate escalation in cybercrimes. This study undertakes an exploration into the intrinsic nature of network packets, aiming to discern their potential for malice or legitimacy. In the internet, 32 intermediate nodes are encountered by a Network packet before it reaches its final host. Our findings suggest that the time-to-live (TTL) parameter in certain IP packets diverges from the initial TTL by more than 32 intermediary hops. It's likely that these packets are generated by specialized software. We anticipate that malicious IP packets exhibit unconventional TTL values, influenced by factors such as the source machine's operating system and protocols like TCP/ICMP/UDP, etc. To gauge the effectiveness and value of the proposed method, an experiment was conducted utilizing the SNORT NIDS system. Filtering rules based on signatures were formulated to thoroughly analyze the traffic. Real network data, along with DARPA and MACCDC 2012 datasets, were employed as inputs for the SNORT NIDS, and it has been observed that the suggested approach successfully detects the anomalous network packets.
Article Details
References
Andrew S. Tanenbaum, "Computer networks":4th Edition, 9788131701980,
Forouzan, Behrouz A.. TCP/IP Protocol Suite. United Kingdom, McGraw-Hill, 2002.
Roberto Di Pietro, Luigi Mancini, "Intrusion Detection Systems", ISBN: 9780387772660, Germany, Springer US, 2008.
“Subin’s blog” https://subinsb.com/default-device-ttl-values/
“OSTECHNIX” https://ostechnix.com/identify-operating-system-ttl-ping/
SNORT, "https://www.snort.org/", Network Intrusion Detection System.
“Manual_Snort”http://manual-snort-org.s3-website-us-east-1.amazonaws.com/node32.html
“ResearchGate”https://www.researchgate.net/figure/Operating-Systems-TTL-Values_tbl1_260288614
Yamada, R. and Goto, S., 2013. Using abnormal TTL values to detect malicious IP packets. Proceedings of the Asia-Pacific Advanced Network, 34, pp.27-34.
Paxson, V., 1997. End-to-end routing behavior in the Internet. IEEE/ACM transactions on Networking, 5(5), pp.601-615.Q. Scheitle, O. Gasser, P. Emmerich, and G. Carle, “Carrier-Grade Anomaly Detection Using Time-to-Live Header Information,” 2016, [Online]. Available: http://arxiv.org/abs/1606.07613
Kushwah, D., Singh, R.R. and Tomar, D.S., 2019, January. An Approach to Meta-Alert Generation for Anomalous TCP Traffic. In International Conference on Security & Privacy (pp. 193-216). Springer, Singapore.
Ahmed Al-Hunaiyyan, Asaad Alzayed, Rana Alhajri, Abdulwahed Khalfan. (2023). Using Social Networking Sites for Requirements Elicitation: Perspectives and Challenges. International Journal of Intelligent Systems and Applications in Engineering, 11(4s), 357–368. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2675.
Jin, C., Wang, H. and Shin, K.G., 2003, October. Hop-count filtering: an effective defense against spoofed DDoS traffic. In Proceedings of the 10th ACM conference on Computer and communications security (pp. 30-41).
Vanaubel, Y., Pansiot, J. J., Mérindol, P., & Donnet, B. (2013, October). Network fingerprinting: TTLbased router signatures. In Proceedings of the 2013 conference on Internet measurement conference (pp. 369-376).
J. Ren, J. Guo, W. Qian, H. Yuan, X. Hao, and H. Jingjing, “Building an Effective Intrusion Detection System by Using Hybrid Data Optimization Based on Machine Learning Algorithms,” Secur. Commun. Networks, vol. 2019, 2019, doi: 10.1155/2019/7130868
R. T. Gaddam and M. Nandhini, “An analysis of various SNORT based techniques to detect and prevent intrusions in networks: Proposal with code refactoring SNORT tool in Kali Linux environment,” Proc. Int. Conf. Inven. Commun. Comput. Technol. ICICCT 2017, no. Icicct, pp. 10–15, 2017, doi: 10.1109/ICICCT.2017.7975177.
M. Albanese, E. Battista, and S. Jajodia, “A deception based approach for defeating OS and service fingerprinting,” 2015 IEEE Conf. Commun. NetworkSecurity, CNS 2015, pp. 317–325, 2015, doi: 10.1109/CNS.2015.7346842.
R. Harang and P. Guarino, “Clustering of SNORT alerts to identify patterns and reduce analyst workload,” Proc. - IEEE Mil. Commun. Conf. MILCOM, pp. 1–6, 2012, doi: 10.1109/MILCOM.2012.6415777.
R. Harang and P. Guarino, “Clustering of SNORT alerts to identify patterns and reduce analyst workload,” Proc. - IEEE Mil. Commun. Conf. MILCOM, pp. 1–6, 2012, doi: 10.1109/MILCOM.2012.6415777.
1999 DARPA Intrusion Detection Evaluation Dataset- https://www.ll.mit.edu/r-d/datasets/1999-darpaintrusion-detection-evaluation-dataset
https://www.netresec.com/?page=MACCDC "National CyberWatch Mid-Atlantic Collegiate Cyber Defense Competition (MACCDC)"
G. D. Kurundkar, N. A. Naik, and S. D. Khamitkar, “Network Intrusion Detection using SNORT,” Int. J. Eng. Res. Appl., vol. 2, no. 2, pp. 1288–1296, 2012.
R. R. Kompella, S. Singh, and G. Varghese, “On scalable attack detection in the network,” IEEE/ACM Trans. Netw., vol. 15, no. 1, pp. 14–25, 2007, doi: 10.1109/TNET.2006.890115.
V. A. Grønland, “Building IDS rules by means of a honeypot,” Dep. Comput. Sci. Media Technol. Gjøvik Univ. Coll. 2006, vol. 77, 2006, [Online]. Available: http://brage.bibsys.no/hig/handle/URN:NBN:no-bibsys_brage_4248%5Cnhttp://brage.bibsys.no/hig/bitstream/URN:NBN:no-bibsys_brage_4248/1/Gronland - Building ids rules by means of a honeypot.pdf%5Cnhttp://brage.bibsys.no/hig/handle/URN:NBN:no-bibsys_brage_424
R. Beverly, “A robust classifier for passive tcp/ip fingerprinting,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 3015, pp. 158–167, 2004, doi: 10.1007/978-3-540-24668-8_16.
M. Roesch, “SNORT - Lightweight intrusion detection for networks,” Proc. 13th Conf. Syst. Adm. LISA 1999, pp. 229–238, 1999.
Kshirsagar, D. R. . (2021). Malicious Node Detection in Adhoc Wireless Sensor Networks Using Secure Trust Protocol. Research Journal of Computer Systems and Engineering, 2(2), 12:16. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/26.
Kumar, Vinod, and Om Prakash Sangwan. "Signature based intrusion detection system using SNORT." International Journal of Computer Applications & Information Technology 1.3 (2012): 35-41.
Z. Zhou, Z. Chen, T. Zhou, and X. Guan, “The study on network intrusion detection system of SNORT,” 2010 Int. Conf. Netw. Digit. Soc. ICNDS 2010, vol. 2, pp. 194–196, 2010, doi: 10.1109/ICNDS.2010.5479341.
Singh, R.R. and Tomar, D.S., 2015. Network forensics: detection and analysis of stealth port scanning attack. International Journal of Computer Networks and Communications Security, 3(2), pp.33-42.
Kushwah D, Singh RR, Tomar DS. An approach to meta-alert generation for anomalous tcp traffic. InSecurity and Privacy: Second ISEA International Conference, ISEA-ISAP 2018, Jaipur, India, January, 9–11, 2019, Revised Selected Papers 2 2019 (pp. 193-216). Springer Singapore.