Secure Message Dissemination with QoS Guaranteed Routing in Internet of Vehicles
Main Article Content
Abstract
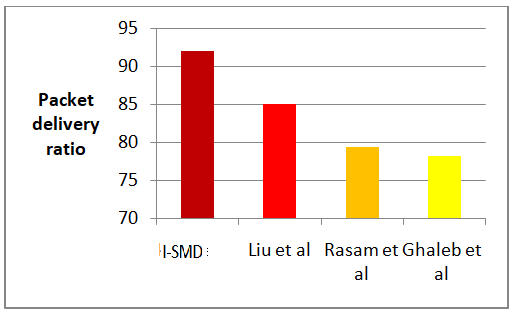
Internet of Vehicles (IoV) is a variant of vehicular adhoc network (VANET) where vehicles can communicate with other vehicles, infrastructure devices, parking lots and even pedestrians. Communication to other entities is facilitates through various services like DSRC, C2C-CC. Fake messages can be propagated by attackers for various selfish needs. Complex authentication procedures can affect the propagation of emergency messages. Thus a light weight mechanism to ensure the trust of messages without affecting the delivery deadlines for emergency messages. Addressing this problem, this work proposes a clustering based network topology for IoV where routing is optimized for message dissemination of various classes using hybrid meta-heuristics. In addition, two stage message authentication technique combining collaborative authentication with Bayesian filtering is proposed to verify the authenticity of message. Through simulation analysis, the proposed solution is found to detect fake messages with an accuracy of 96% with 10% lower processing delay compared to existing works.
Article Details
References
S. Latif, S. Mahfooz, B. Jan, N. Ahmad, Y. Cao, M. Asif, A comparative study of scenario-driven multi-hop broadcast protocols for vanets, Veh. Commun. 12 (2018) 88–109
S. Latif, S. Mahfooz, B. Jan, N. Ahmad, Y. Cao, M. Asif, A comparative study of scenario-driven multi-hop broadcast protocols for vanets, Veh. Commun. 12 (2018) 88–109
W. Li, H. Song, Art: an attack-resistant trust management scheme for securing vehicular ad hoc networks, IEEE Trans. Intell. Transp. Syst. 17 (4) (2016) 960–969
Ullah, Noor & Kong, Xiangjie & Tolba, Amr & Alrashoud, Mubarak & Xia, Feng. (2020). Emergency warning messages dissemination in vehicular social networks: A trust based scheme. Vehicular Communications. 100199. 10.1016/j.vehcom.2019.100199.
A. Dua, N. Kumar, S. Bawa, Reidd: reliability-aware intelligent data dissemination protocol for broadcast storm problem in vehicular ad hoc networks, Telecommun. Syst. 64 (3) (2017) 439–458
Liu J, Yang W, Zhang J, Yang C. Detecting false messages in vehicular ad hoc networks based on a traffic flow model. International Journal of Distributed Sensor Networks. 2020;16(2).
S. Park and C. C. Zou, "Reliable Traffic Information Propagation in Vehicular Ad-Hoc Networks," 2008 IEEE Sarnoff Symposium, Princeton, NJ, USA, 2008, pp. 1-6
Arshad, M., Ullah, Z., Ahmad, N. et al. A survey of local/cooperative-based malicious information detection techniques in VANETs. J Wireless Com Network 2018, 62 (2018).
Mr. R. Senthil Ganesh. (2019). Watermark Decoding Technique using Machine Learning for Intellectual Property Protection . International Journal of New Practices in Management and Engineering, 8(03), 01 - 09. https://doi.org/10.17762/ijnpme.v8i03.77.
Mohamed TM, Ahmed IZ, Sadek RA. Efficient VANET safety message delivery and authenticity with privacy preservation. PeerJ Comput Sci. 2021 May 4;7:e519
Chen Chen (2010). A Trust-based Message Evaluation and Propagation Framework in Vehicular Ad-Hoc Networks. UWSpace. http://hdl.handle.net/10012/4929
C. Zhang, K. Chen, X. Zeng and X. Xue, "Misbehavior Detection Based on Support Vector Machine and Dempster-Shafer Theory of Evidence in VANETs," in IEEE Access, vol. 6, pp. 59860-59870, 2018
Aslan, M., Sen, S. (2019). Evolving Trust Formula to Evaluate Data Trustworthiness in VANETs Using Genetic Programming. In: Kaufmann, P., Castillo, P. (eds) Applications of Evolutionary Computation. EvoApplications 2019. Lecture Notes in Computer Science(), vol 11454. Springer, Cham
Mujahid Muhammad, Paul Kearney, Adel Aneiba, Junaid Arshad, Andreas Kunz. RMCCS: RSSI-based Message Consistency Checking Scheme for V2V Communications. In Sabrina De Capitani di Vimercati, Pierangela Samarati, editors, Proceedings of the 18th International Conference on Security and Cryptography, SECRYPT 2021, July 6-8, 2021. pages 722-727, SCITEPRESS
Rassam, Murad & Ghaleb, Fuad & Zainal, Anazida & Maarof, Mohd. (2019). Detecting Bogus Information Attack in Vehicular Ad Hoc Network: A Context-Aware Approach.
Mohannad O. Rawashdeh, Sayel M. Fayyad, Sulieman Abu-Ein, Waleed Momani, Zaid Abulghanam, A. M. Maqableh. (2023). Intelligent Automobiles Diagnostic System. International Journal of Intelligent Systems and Applications in Engineering, 11(4s), 458–465. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2703.
Ghaleb, F.A.; Maarof, M.A.; Zainal, A.; Al-Rimy, B.A.S.; Saeed, F.; Al-Hadhrami, T. Hybrid and Multifaceted Context-Aware Misbehavior Detection Model for Vehicular Ad Hoc Network. IEEE Access 2019, 7, 159119–159140.
Sharshembiev, K.; Yoo, S.M.; Elmahdi, E.; Kim, Y.K.; Jeong, G.H. Fail-Safe Mechanism Using Entropy Based Misbehavior Classification and Detection in Vehicular Ad Hoc Networks. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA, 14–17 July 2019; pp. 123–128
Guo, J.; Li, X.; Liu, Z.; Ma, J.; Yang, C.; Zhang, J.; Wu, D. TROVE: A context-awareness trust model for VANETs using reinforcement learning. IEEE Internet Things J. 2020, 7, 6647–6662.
Sedjelmaci, H.; Senouci, S.M.; Abu-Rgheff, M.A. An efficient and lightweight intrusion detection mechanism for service-oriented vehicular networks. IEEE Internet Things J. 2014, 1, 570–577.
Steffy, A. D. . (2021). Dimensionality Reduction Based Diabetes Detection Using Feature Selection and Machine Learning Architectures. Research Journal of Computer Systems and Engineering, 2(2), 45:50. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/32.
Zaidi, K.; Milojevic, M.B.; Rakocevic, V.; Nallanathan, A.; Rajarajan, M. Host-Based Intrusion Detection for VANETs: A Statistical Approach to Rogue Node Detection. IEEE Trans. Veh. Technol. 2016, 65, 6703–6714
Liang, J.; Lin, Q.; Chen, J.; Zhu, Y. A Filter Model Based on Hidden Generalized Mixture Transition Distribution Model for Intrusion Detection System in Vehicle Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2019, 10, 2707–2722.
L. Kou, G. Markowsky, and L. Berman. A fast algorithm for steiner trees. Acta Informatica, 15:141–145, 1981
S. Saremi, S. Mirjalili, and A. Lewis, ``Grasshopper optimisation algorithm: Theory and application,'' Adv. Eng. Softw., vol. 105, pp. 30_47, Mar. 2017.