Robust Deep Learning Based Framework for Detecting Cyber Attacks from Abnormal Network Traffic
Main Article Content
Abstract
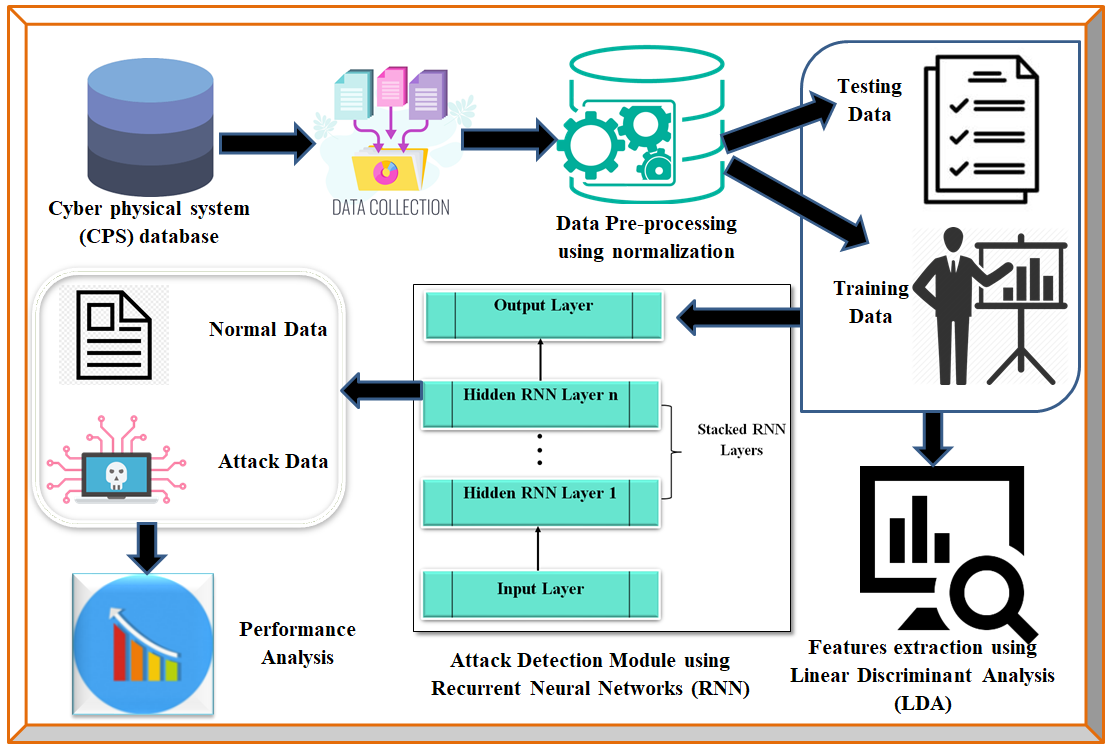
The internet's recent rapid growth and expansion have raised concerns about cyberattacks, which are constantly evolving and changing. As a result, a robust intrusion detection system was needed to safeguard data. One of the most effective ways to meet this problem was by creating the artificial intelligence subfields of machine learning and deep learning models. Network integration is frequently used to enable remote management, monitoring, and reporting for cyber-physical systems (CPS). This work addresses the primary assault categories such as Denial of Services(DoS), Probe, User to Root(U2R) and Root to Local(R2L) attacks. As a result, we provide a novel Recurrent Neural Networks (RNN) cyberattack detection framework that combines AI and ML techniques. To evaluate the developed system, we employed the Network Security Laboratory-Knowledge Discovery Databases (NSL-KDD), which covered all critical threats. We used normalisation to eliminate mistakes and duplicated data before pre-processing the data. Linear Discriminant Analysis(LDA) is used to extract the characteristics. The fundamental rationale for choosing RNN-LDA for this study is that it is particularly efficient at tackling sequence issues, time series prediction, text generation, machine translation, picture descriptions, handwriting recognition, and other tasks. The proposed model RNN-LDA is used to learn time-ordered sequences of network flow traffic and assess its performance in detecting abnormal behaviour. According to the results of the experiments, the framework is more effective than traditional tactics at ensuring high levels of privacy. Additionally, the framework beats current detection techniques in terms of detection rate, false positive rate, and processing time.
Article Details
References
W. Duo, M. Zhou, and A. Abusorrah, “A Survey of Cyber Attacks on Cyber Physical Systems: Recent Advances and Challenges,” IEEE/CAA Journal of Automatica Sinica, vol. 9, no. 5, pp. 784–800, May 2022.
C. Kwon and I. Hwang, “Reachability Analysis for Safety Assurance of Cyber-Physical Systems Against Cyber Attacks,” IEEE Transactions on Automatic Control, vol. 63, no. 7, pp. 2272–2279, Jul. 2018.
S. Tepjit, I. Horváth, and Z. Rusák, “The state of framework development for implementing reasoning mechanisms in smart cyber-physical systems: A literature review,” Journal of Computational Design and Engineering, vol. 6, no. 4, pp. 527–541, Apr. 2019.
M. Yildirim, “Artificial Intelligence-Based Solutions for Cyber Security Problems,” Artificial Intelligence Paradigms for Smart Cyber-Physical Systems, pp. 68–86, 2021.
H. Yang, K. Zhan, M. Kadoch, Y. Liang, and M. Cheriet, “BLCS: Brain-Like Distributed Control Security in Cyber Physical Systems,” IEEE Network, vol. 34, no. 3, pp. 8–15, May 2020.
R. Prasad and V. Rohokale, “Artificial Intelligence and Machine Learning in Cyber Security,” Cyber Security: The Lifeline of Information and Communication Technology, pp. 231–247, Oct. 2019.
Ahmed, M., Mahmood, A.N., Hu, J.: ‘A survey of network anomaly detection techniques’, J. Netw. Comput. Appl., 2016, 60, pp. 19–31
R. Kumar and R. Tripathi, “DBTP2SF: A deep blockchain-based trustworthy privacy-preserving secured framework in industrial Internet of Things systems,” Trans. Emerg. Telecommun. Technol., vol. 32, no. 4, 2021, Art. no. e4222.
S. Latif, Z. Idrees, J. Ahmad, L. Zheng, and Z. Zou, “A blockchain-based architecture for secure and trustworthy operations in the industrial Internet of Things,” J. Ind. Inf. Integr., vol. 21, 2021, Art. no. 100190.
Singh, K., Dhindsa, K. S., & Nehra, D. (2020). T-CAD: A threshold based collaborative DDOS attack detection in multiple autonomous systems. Journal of Information Security and Applications, 51, 102457.
Sharma, A., Agrawal, C., Singh, A., & Kumar, K. (2020). Real-Time DDOS Detection Based on Entropy Using Hadoop Framework. In Computing in Engineering and Technology (pp. 297-305).
D. K. Jain, S. K. S. Tyagi, M. Prakash and L. Natrayan, "Metaheuristic Optimization-Based Resource Allocation Technique for Cybertwin-Driven 6G on IoE Environment," in IEEE Transactions on Industrial Informatics, vol. 18, no. 7, pp. 4884-4892, July 2022, doi: 10.1109/TII.2021.3138915.
S. A. Ludwig, “Intrusion detection of multiple attack classes using a deep neural net ensemble,” in Proceedings of 2017 IEEE Symposium Series on Computational Intelligence (SSCI), IEEE, Honolulu,HI, USA, November 2017.
K.-D. Lu, G.-Q. Zeng, X. Luo, J. Weng, W. Luo, and Y. Wu, “Evolutionary deep belief network for cyber-attack detection in industrial automation and control system,” IEEE Trans. Ind. Informat., vol. 17, no. 11, pp. 7618–7627, Nov. 2021.
T. T. Huong et al., “Lockedge: Low-complexity cyberattack detection in IoT edge computing,” IEEE Access, vol. 9, pp. 29696–29710, 2021
J. Kim, N. Shin, S. Y. Jo, and S. H. Kim, “Method of intrusion detection using deep neural network,” in 2017 IEEE International Conference on Big Data and Smart Computing (BigComp), pp. 313–316, Jeju, 2017.
M. A. Ferrag, L. Maglaras, S. Moschoyiannis, and H. Janicke, “Deep learning for cyber security intrusion detection: approaches, datasets, and comparative study,” Journal of Information Security and Applications, vol. 50, p. 102419
R. Vinayakumar, M. Alazab, K. P. Soman, P. Poornachandran, A. Al-Nemrat, and S. Venkatraman, “Deep learning approach for intelligent intrusion detection system,” IEEE Access, vol. 7, pp. 41525–41550, 2019.
T. Erpek, Y. E. Sagduyu, and Y. Shi, “Deep learning for launching and mitigating wireless jamming attacks,” IEEE Transactions on Cognitive Communications and Networking, vol. 5, no. 1, pp. 2–14, 2018
M. Yousefi-Azar, V. Varadharajan, L. Hamey, and U. Tupakula, “Autoencoder-based feature learning for cyber security applications,” in Proceedings of 2017 International Joint Conference on Neural Networks (IJCNN), IEEE, San Diego, CA, USA, pp. 3854–3861, June 2017.
A. Javaid, Q. Niyaz, W. Sun, and M. Alam, “A deep learning approach for network intrusion detection system,” in Proceedings of the 9th EAI International Conference on Bio-Inspired Information and Communications Technologies (formerly BIONETICS), pp. 21–26, New York, NY, USA, December 2016.
F. Farahnakian and J. Heikkonen, “A deep auto-encoder based approach for intrusion detection system,” in Proceedings of 2018 20th International Conference on Advanced Communication Technology (ICACT), IEEE, Chuncheon, South Korea, pp. 178–183, July 2018.
Marteau, P.F. Sequence covering for efficient host-based intrusion detection. IEEE Trans. Inf. Forensics Secur. 2018, 14, 994–1006.
Aburomman, A.A.; Reaz, M.B.I. A novel SVM-kNN-PSO ensemble method for intrusion detection system. Appl. Soft Comput. 2016, 38, 360–372.
S. ur Rehman et al., “DIDDOS: An approach for detection and identification of distributed denial of service (DDoS) cyberattacks using gated recurrent units (GRU),” Future Gener. Comput. Syst., vol. 118, pp. 453–466, 2021.
Y. Jia, F. Zhong, A. Alrawais, B. Gong, and X. Cheng, “Flowguard: An intelligent edge defense mechanism against IoT DDoS attacks,” IEEE Internet Things J., vol. 7, no. 10, pp. 9552–9562, Oct. 2020.
Virupakshar, K.B.; Asundi, M.; Channal, K.; Shettar, P.; Patil, S.; Narayan, D. Distributed denial of service (DDoS) attacks detection system for OpenStack-based private cloud. Procedia Comput. Sci. 2020, 167, 2297–2307.
Lian, W.; Nie, G.; Jia, B.; Shi, D.; Fan, Q.; Liang, Y. An Intrusion Detection Method Based on Decision Tree-Recursive Feature Elimination in Ensemble Learning. Math. Probl. Eng. 2020, 2020, 2835023.
Gu, J.; Wang, L.; Wang, H.; Wang, S. A novel approach to intrusion detection using SVM ensemble with feature augmentation. Comput. Secur. 2019, 86, 53–62.
Jiang, K.; Wang, W.; Wang, A.; Wu, H. Network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access 2020, 8, 32464–32476.
Andresini, G.; Appice, A.; Di Mauro, N.; Loglisci, C.; Malerba, D. Multi-channel deep feature learning for intrusion detection. IEEE Access 2020, 8, 53346–53359.
Alsirhani, A.; Sampalli, S.; Bodorik, P. DDoS detection system: Using a set of classification algorithms controlled by fuzzy logic system in apache spark. IEEE Trans. Netw. Serv. Manag. 2019, 16, 936–949. [CrossRef]
Yao, H.; Fu, D.; Zhang, P.; Li, M.; Liu, Y. MSML: A novel multilevel semi-supervised machine learning framework for intrusion detection system. IEEE Internet Things J. 2018, 6, 1949–1959.
Sharath, M.N., Rajesh, T.M. & Patil, M. Design of optimal metaheuristics-based pixel selection with homomorphic encryption technique for video steganography. Int. j. inf. technology. 14, 2265–2274 (2022). https://doi.org/10.1007/s41870-022-01005-9
Zhenwei Zhao, Xiaoming Li, Bing Luan, Weining Jiang, Weidong Gao, Secure Internet of Things (IoT) using a Novel Brooks Iyengar Quantum Byzantine Agreement-centered blockchain Networking (BIQBA-BCN) Model in Smart Healthcare, Information Sciences, 2023,https://doi.org/10.1016/j.ins.2023.01.020
Alharbi, M.,Gupta, S. et al. Mobility aware load balancing using Kho–Kho optimization algorithm for hybrid Li-Fi and Wi-Fi network. Wireless Networks (2023). https://doi.org/10.1007/s11276-022-03225-0
D. Paulraj, P. Ezhumalai & M. Prakash (2022) A Deep Learning Modified Neural Network(DLMNN) based proficient sentiment analysis technique on Twitter data, Journal of Experimental & Theoretical Artificial Intelligence, DOI: 10.1080/0952813X.2022.2093405
Harinder Singh, D. Ramya, Nayani Sateesh, Rohit Anand, Swarnjit Singh, Artificial intelligence-based quality of transmission predictive model for cognitive optical networks, Optik, Vol. 257, 2022,https://doi.org/10.1016/j.ijleo.2022.168789
B.T. Geetha, P. Santhosh Kumar, B. Sathya Bama, Chiranjit Dutta, D. Vijendra Babu, Green energy aware and cluster-based communication for future load prediction in IoT, Sustainable Energy Technologies and Assessments, Vol.52,2022,102244, https://doi.org/10.1016/j.seta.2022.102244.