9/7 LIFT Reconfigurable Architecture Implementation for Image Authentication
Main Article Content
Abstract
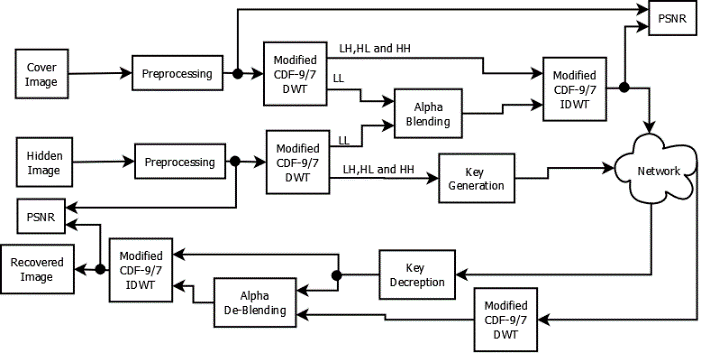
Considering the information system medical images are the most sensitive and critical types of data. Transferring medical images over the internet requires the use of authentication algorithms that are resistant to attacks. Another aspect is confidentiality for secure storage and transfer of medical images. The proposed study presents an embedding technique to improve the security of medical images. As a part of preprocessing that involves removing the high-frequency components, Gaussian filters are used. To get LL band features CDF9/7 wavelet is employed. In a similar way, for the cover image, the LL band features are obtained. In order to get the 1st level of encryption the technique of alpha blending is used. It combines the LL band features of the secret image and cover images whereas LH, HL, and HH bands are applied to Inverse CDF 9/7. The resulting encrypted image along with the key obtained through LH, HL, and HH bands is transferred. The produced key adds an extra layer of protection, and similarly, the receiver does the reverse action to acquire the original secret image. The PSNR acquired from the suggested technique is compared to PSNR obtained from existing techniques to validate the results. Performance is quantified in terms of PSNR. A Spartan 6 FPGA board is used to synthesize the complete architecture in order to compare hardware consumption.
Article Details
References
Maureen N. Hood, Hugh Scott,” Introduction to Picture Archive and Communication Systems”, Journal of Radiology Nursing, Volume 25, Issue 3, 2006, Pages 69-74, ISSN 1546-0843, doi:10.1016/j.jradnu.2006.06.003.
Nyeem H, Boles W, Boyd C. “A review of medical image watermarking requirements for teleradiology”. J Digital Imaging. 2013 Apr;26(2):326-43. doi: 10.1007/s10278-012-952 7-x.
P. B, R. Harish, S. B and V. M, "Image Steganography using RSA Algorithm for Secure Communication," 2021 IEEE International Conference on Mobile Networks and Wireless Communications (ICMNWC), 2021,pp.1-5,doi:10.1109/ ICM NWC52512.2021. 9688352.
L. Negi and L. Negi, "Image Steganography Using Steg with AES and LSB," 2021 IEEE 7th International Conference on Computing, Engineering and Design (ICCED),2021,pp.1-6,doi: 10.1109/ICCED53389. 2021 .9664834.
S.S.Yadahalli, S.Rege and R. Sonkusare, "Implementation and analysis of image steganography using Least Significant Bit and Discrete Wavelet Transform techniques",5th International Conference on Communication and Electronics Systems (ICCES2020),pp.13251330,doi:10.1109/ICCES48766.2020.137 887 .
Ravi, G. ., Das, M. S. ., & Karmakonda, K. . (2023). Energy Efficient Data Aggregation Scheme using Improved LEACH Algorithm for IoT Networks. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 174 –. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2521
M. K. Hasan et al., "Lightweight Encryption Technique to Enhance Medical Image Security on Internet of Medical Things Applications", in IEEE Access, vol. 9, pp. 47731-47742, 2021, doi: 10.1109/ ACCESS. 2021. 3061710.
Z. Wang, Z. Zhang and J. Jiang, "Multi-Feature Fusion based Image Steganography using GAN", 2021 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), 2021, pp. 280-281, doi: 10.1109/ ISSREW 53611. 2 021.00079.
P.A, U. R, J. N and P. S, "Securing Medical Images using Encryption and LSB Steganography",2021 International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT), 2021, pp. 1-5, doi: 10.1109/ICAECT49130.2021.9392396.
Prof. Deepanita Mondal. (2018). Analysis and Evaluation of MAC Operators for Fast Fourier Transformation. International Journal of New Practices in Management and Engineering, 7(01), 01 - 07. https://doi.org/10.17762/ijnpme.v7i01.62
M. A. Usman and M. R. Usman, "Using image steganography for providing enhanced medical data security", 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), 2018, pp. 1-4, doi: 10.1109/CCNC.2018.8319263.
A. Srivastava, S. K. Awasthi, S. Javed, S. Gautam, N. Kishore and R. Bakthula, "Seeded One Time Pad for Security of Medical Images in Health Information", 2018 4th International Conference on Computing Communication and Atomation (ICCCA), 2018, pp. 1-6, doi: 10.1109/CCAA.2018.8777701.
Rodríguez, M., Jovanovi?, A., Petrova, M., Merwe, M. van der, & Levi, S. Predicting Customer Lifetime Value with Regression Models. Kuwait Journal of Machine Learning, 1(4). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/144
Prakash Marakumbi, Satish Bhairannawar “Efficient reconfigurable architecture to enhance medical image security”, Indonesian Journal of Electrical Engineering and Computer Science Vol. 30, No. 3, June 2023, pp. 1516~1524 ISSN: 2502-4752, DOI: 10.11591/ijeecs.v30.i3.pp1516-1524.
P. T. Akkasaligar and S. Biradar, "Medical Image Compression and Encryption using Chaos based DNA Cryptography", 2020 IEEE Bangalore Humanitarian Technology Conference (B-HTC), 2020, pp. 1-5, doi: 10.1109/B-HTC509 70.2020.
M. A. W. Shalaby, M. T. Saleh and H. N. Elmahdy, "Enhanced Arnold’s Cat Map-AES Encryption Technique for Medical Images", 2020 2nd Novel Intelligent and Leading Emerging Sciences Conference (NILES), 2020, pp. 288-295, doi: 10.1109/NILES50944.2020.9257876.
Y. Ding et al., "DeepEDN: A Deep-Learning-Based Image Encryption and Decryption Network for Internet of Medical Things", in IEEE Internet of Things Journal, vol. 8, no. 3, pp. 1504-1518, 1 Feb.1, 2021, doi: 10.1109/JIOT.2020.3012452.
S. T. Kamal, K. M. Hosny, T. M. Elgindy, M. M. Darwish and M. M. Fouda, "A New Image Encryption Algorithm for Grey and Color Medical Images", in IEEE Access, vol. 9, pp. 37855-37865,2021, doi: 10.1109/ACCESS.2021. 3063237.
A. Shankar and A. Kannammal, "A Hybrid Of Watermark Scheme With Encryption To Improve Security Of Medical Images", 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), 2021, pp. 226-233, doi: 10.1109/ICICV50876 .2021. 9388616.
J. Zhou, J. Li and X. Di, "A Novel Lossless Medical Image Encryption Scheme Based on Game Theory With Optimized ROI Parameters and Hidden ROI Position", in IEEE Access, vol. 8, pp. 122210-122228, 2020, doi: 10.1109/ACCESS .2020 .3007550.
Renato Costa, Deep Reinforcement Learning for Autonomous Robotics , Machine Learning Applications Conference Proceedings, Vol 2 2022.
P. Sarosh, S. A. Parah and G. Mohiuddin Bhat, "Fast Image Encryption Framework for Medical Images", 2021 2nd International Conference on Intelligent Engineering and Management (ICIEM), 2021, pp. 149-154, doi: 10.1109/ICIEM 51511.2021.9445362.
A. Belazi, M. Talha, S. Kharbech and W. Xiang, "Novel Medical Image Encryption Scheme Based on Chaos and DNA Encoding", in IEEE Access, vol. 7, pp. 36667-36681, 2019, doi: 10.1109/ACCESS.2019.2906292.
Vanitha, V., Akila, D.” Bio-medical Image Encryption Using the Modified Chaotic Image Encryption Method”, Lecture Notes in Computational Vision and Biomechanics, (2023)vol 37. Springer, Singapore. https://doi.org/10.1007/978-981-19-01 51-5_20
Paul, A., Kandar, S. & Dhara, B.C. “Image encryption using permutation generated by modified Regula-Falsi method”. Appl Intell 52, 10979–10998 (2022). https://doi.org/10.1007/s10489-021-03063-1
Yousif, S.F., Abboud, A.J. & Alhumaima, R.S. “A new image encryption based on bit replacing, chaos and DNA coding techniques”, Multimed Tools Appl 81, 27453–27493 (2022). https://doi.org/10.1007/s11042-022-12762-x
Ismail, R., Fattah, A., Saqr, H.M. et al. “An efficient medical image encryption scheme for (WBAN) based on adaptive DNA and modern multi chaotic map". Multimed Tools Appl (2022). https://doi.org/10.1007/s11042-022-13343-8
Sayantam Sarkar and Satish S Bhairannawar, “Efficient FPGA Architecture of Optimized Haar Wavelet Transform for Image and Video Processing Applications”, Journal of Multi dimensional Systems and Signal Processing, Springer, Vol. 32, pp. 821-844, April 2021 (DOI: 10.1007/s11045-020-00759-4).
Anbumani V,Soviya S, Sneha S and Saran L, “Speed and Power Efficient Vedic Multiplier using Adders with MUX”, IEEE Innovations in Power and Advanced Computing Technologies (i-PACT), pp. 1-5, 2021.DOI: 10.1109/i-PACT5 2 855.2021.9696992
Datasheet of Digilent ATLYS FPGA board. [Online] Available at:https://reference.digilentinc.com/_media/atlys:atlys:atlys_ rm .pdf.
Steven T. Karris. “Introduction to Simulink with Engineering Applications”. Gatesmark Publishing, 2nd edition, 2006.
Charls H. Roth (Jr.), “Digital System Design using VHDL”, Cengage Learning, 2006.
AyaJaradat, EyadTaqieddin and MoadMowafi, “A High-Capacity Image steganography Method Using Chaotic Particle Swarm Optimization”, Security and Communication Networks, Hindawi, pp. 1-11, 2021.
Qureshi, D. I. ., & Patil, M. S. S. . (2022). Secure Sensor Node-Based Fusion by Authentication Protocol Using Internet of Things and Rfid. Research Journal of Computer Systems and Engineering, 3(1), 48–55. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/41
P. K. Muhuri, Z. Ashraf and S. Goel, “A novel image steganographic method based on integer wavelet transformation and particle swarm optimization,” Applied Soft Computing, Elsevier, vol. 92, pp. 1-41, 2020.
A.H. Mohsin, A. A. Zaidan, B. B. Zaidan and Salem Garfan “New method of image steganography based on particle swarm optimization algorithm in spatial domain for high embedding capacity,” IEEE Access, vol. 7, pp. 168994–169010, 2019.
Nikhil Simha H.N., Pradeep M. Prakash, Suraj S. Kashyap , Sayantam Sarkar "FPGA Implementation of Image Steganography Using Haar DWT and Modified LSB Techniques." IEEE International Conference on Advances in Computer Applications (ICACA), pp 26-31, 2016
Jatin Chaudhari and K.R.Bhatt, “FPGA Implementation of Image Steganography: A Retrospective”, International Journal of Engineering Development and Research, pp. 2117-2121, Volume 2, Issue 2, 2014.