A Hybrid Multi-user Cloud Access Control based Block Chain Framework for Privacy Preserving Distributed Databases
Main Article Content
Abstract
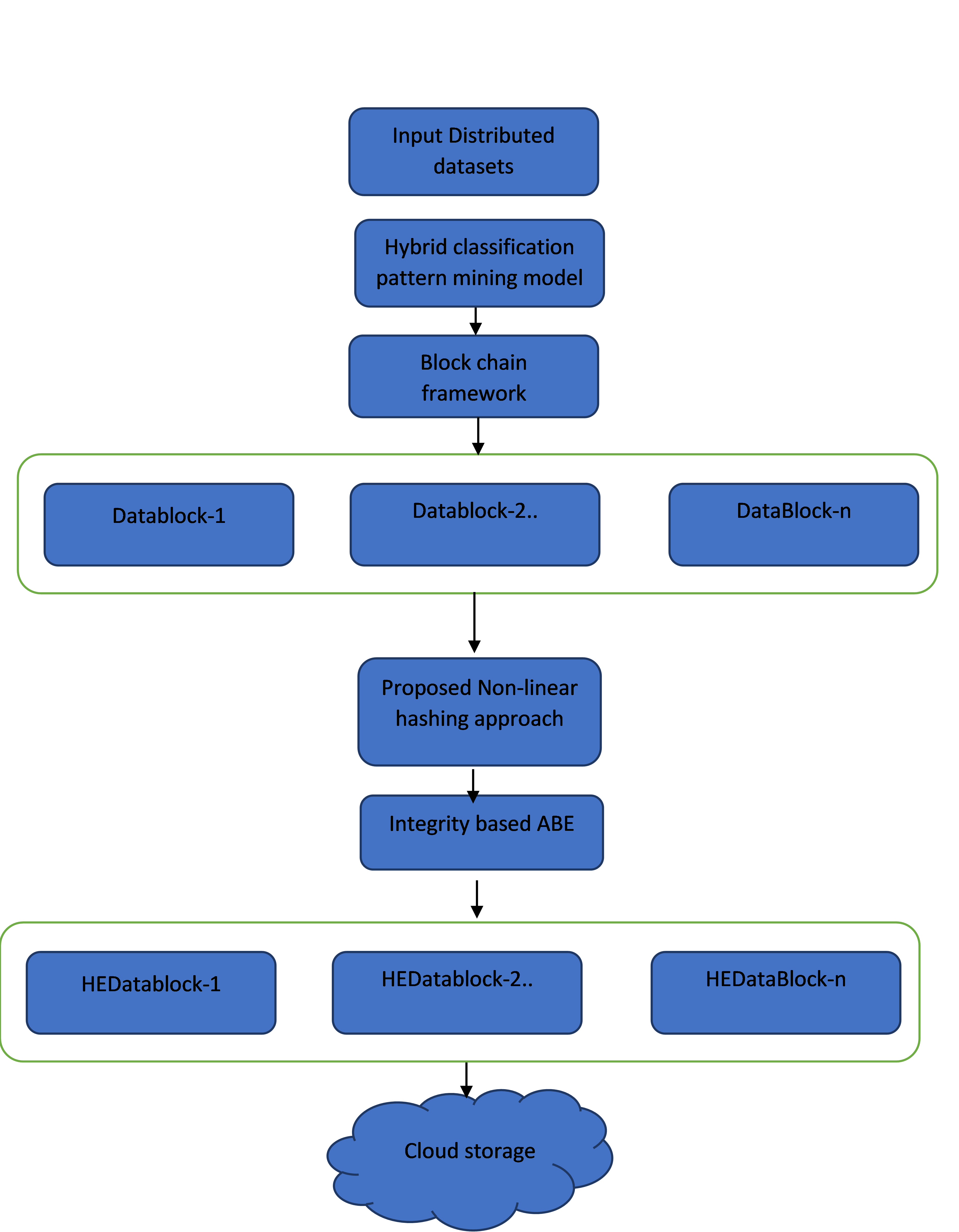
Most of the traditional medical applications are insecure and difficult to compute the data integrity with variable hash size. Traditional medical data security systems are insecure and it depend on static parameters for data security. Also, distributed based cloud storage systems are independent of integrity computational and data security due to unstructured data and computational memory. As the size of the data and its dimensions are increasing in the public and private cloud servers, it is difficult to provide the machine learning based privacy preserving in cloud computing environment. Block-chain technology plays a vital role for large cloud databases. Most of the conventional block-chain frameworks are based on the existing integrity and confidentiality models. Also, these models are based on the data size and file format. In this model, a novel integrity verification and encryption framework is designed and implemented in cloud environment. In order to overcome these problems in the cloud computing environment, a hybrid integrity and security-based block-chain framework is designed and implemented on the large distributed databases. In this framework,a novel decision tree classifier is used along with non-linear mathematical hash algorithm and advanced attribute-based encryption models are used to improve the privacy of multiple users on the large cloud datasets. Experimental results proved that the proposed advanced privacy preserving based block-chain technology has better efficiency than the traditional block-chain based privacy preserving systems on large distributed databases.
Article Details
References
A. Smahi et al., “A blockchainized privacy-preserving support vector machine classification on mobile crowd sensed data,” Pervasive and Mobile Computing, vol. 66, p. 101195, Jul. 2020, doi: 10.1016/j.pmcj.2020.101195.
Z. Xu, Y. Lin, V. K. Arthur Sandor, Z. Huang, and X. Liu, “A lightweight privacy and integrity preserving range query scheme for mobile cloud computing,” Computers & Security, vol. 84, pp. 318–333, Jul. 2019, doi: 10.1016/j.cose.2019.04.003.
D. Ahamad, S. Alam Hameed, and M. Akhtar, “A multi-objective privacy preservation model for cloud security using hybrid Jaya-based shark smell optimization,” Journal of King Saud University - Computer and Information Sciences, Oct. 2020, doi: 10.1016/j.jksuci.2020.10.015.
Y. Tian, M. M. Kaleemullah, M. A. Rodhaan, B. Song, A. Al-Dhelaan, and T. Ma, “A privacy preserving location service for cloud-of-things system,” Journal of Parallel and Distributed Computing, vol. 123, pp. 215–222, Jan. 2019, doi: 10.1016/j.jpdc.2018.09.005.
A. Cuzzocrea, C. K. Leung, B. H. Wodi, S. Sourav, and E. Fadda, “An Effective and Efficient Technique for Supporting Privacy-Preserving Keyword-Based Search over Encrypted Data in Clouds,” Procedia Computer Science, vol. 177, pp. 509–515, Jan. 2020, doi: 10.1016/j.procs.2020.10.070.
J. Hua, G. Shi, H. Zhu, F. Wang, X. Liu, and H. Li, “CAMPS: Efficient and privacy-preserving medical primary diagnosis over outsourced cloud,” Information Sciences, vol. 527, pp. 560–575, Jul. 2020, doi: 10.1016/j.ins.2018.12.054.
Chinmay Rawat. (2023). AI for Effective use of Water in India for Crop Cultivation. International Journal of Intelligent Systems and Applications in Engineering, 11(3s), 266–270. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2683
Z. L. Jiang et al., “Efficient two-party privacy-preserving collaborative k-means clustering protocol supporting both storage and computation outsourcing,” Information Sciences, vol. 518, pp. 168–180, May 2020, doi: 10.1016/j.ins.2019.12.051.
Q. Zhang, G. Wang, and Q. Liu, “Enabling Cooperative Privacy-preserving Personalized search in cloud environments,” Information Sciences, vol. 480, pp. 1–13, Apr. 2019, doi: 10.1016/j.ins.2018.12.016.
B. Denham, R. Pears, and M. A. Naeem, “Enhancing random projection with independent and cumulative additive noise for privacy-preserving data stream mining,” Expert Systems with Applications, vol. 152, p. 113380, Aug. 2020, doi: 10.1016/j.eswa.2020.113380.
X. Liu, R. H. Deng, Y. Yang, H. N. Tran, and S. Zhong, “Hybrid privacy-preserving clinical decision support system in fog–cloud computing,” Future Generation Computer Systems, vol. 78, pp. 825–837, Jan. 2018, doi: 10.1016/j.future.2017.03.018.
C. Zhang, L. Zhu, C. Xu, and R. Lu, “PPDP: An efficient and privacy-preserving disease prediction scheme in cloud-based e-Healthcare system,” Future Generation Computer Systems, vol. 79, pp. 16–25, Feb. 2018, doi: 10.1016/j.future.2017.09.002.
Diksha Siddhamshittiwar. (2017). An Efficient Power Optimized 32 bit BCD Adder Using Multi-Channel Technique. International Journal of New Practices in Management and Engineering, 6(02), 07 - 12. https://doi.org/10.17762/ijnpme.v6i02.57
S. Sheela and K. Sathesh Kumar, “Privacy –Preserved in cloud based data sharing for energy management system using big data analytics,” Materials Today: Proceedings, Nov. 2020, doi: 10.1016/j.matpr.2020.09.621.
E. Ezhilarasan and M. Dinakaran, “Privacy preserving and data transpiration in multiple cloud using secure and robust data access management algorithm,” Microprocessors and Microsystems, vol. 82, p. 103956, Apr. 2021, doi: 10.1016/j.micpro.2021.103956.
W. Fan, J. He, M. Guo, P. Li, Z. Han, and R. Wang, “Privacy preserving classification on local differential privacy in data centers,” Journal of Parallel and Distributed Computing, vol. 135, pp. 70–82, Jan. 2020, doi: 10.1016/j.jpdc.2019.09.009.
N. Domadiya and U. P. Rao, “Privacy Preserving Distributed Association Rule Mining Approach on Vertically Partitioned Healthcare Data,” Procedia Computer Science, vol. 148, pp. 303–312, Jan. 2019, doi: 10.1016/j.procs.2019.01.023.
S. Li, N. Mu, J. Le, and X. Liao, “Privacy preserving frequent itemset mining: Maximizing data utility based on database reconstruction,” Computers & Security, vol. 84, pp. 17–34, Jul. 2019, doi: 10.1016/j.cose.2019.03.008.
X. Ma, F. Zhang, X. Chen, and J. Shen, “Privacy preserving multi-party computation delegation for deep learning in cloud computing,” Information Sciences, vol. 459, pp. 103–116, Aug. 2018, doi: 10.1016/j.ins.2018.05.005.
A. Alabdulatif, I. Khalil, H. Kumarage, A. Y. Zomaya, and X. Yi, “Privacy-preserving anomaly detection in the cloud for quality assured decision-making in smart cities,” Journal of Parallel and Distributed Computing, vol. 127, pp. 209–223, May 2019, doi: 10.1016/j.jpdc.2017.12.011.
J. Domingo-Ferrer, O. Farràs, J. Ribes-González, and D. Sánchez, “Privacy-preserving cloud computing on sensitive data: A survey of methods, products and challenges,” Computer Communications, vol. 140–141, pp. 38–60, May 2019, doi: 10.1016/j.comcom.2019.04.011.
Y. Zhao, S. K. Tarus, L. T. Yang, J. Sun, Y. Ge, and J. Wang, “Privacy-preserving clustering for big data in cyber-physical-social systems: Survey and perspectives,” Information Sciences, vol. 515, pp. 132–155, Apr. 2020, doi: 10.1016/j.ins.2019.10.019.
Jackson, B., Lewis, M., Herrera, J., Fernández, M., & González, A. Machine Learning Applications for Performance Evaluation in Engineering Management. Kuwait Journal of Machine Learning, 1(2). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/126
J.-S. Lee and S.-P. Jun, “Privacy-preserving data mining for open government data from heterogeneous sources,” Government Information Quarterly, vol. 38, no. 1, p. 101544, Jan. 2021, doi: 10.1016/j.giq.2020.101544.
H. Rong, J. Liu, W. Wu, J. Hao, H. Wang, and M. Xian, “Toward fault-tolerant and secure frequent itemset mining outsourcing in hybrid cloud environment,” Computers & Security, vol. 98, p. 101969, Nov. 2020, doi: 10.1016/j.cose.2020.101969.
P. Kumar, G. P. Gupta, and R. Tripathi, “TP2SF: A Trustworthy Privacy-Preserving Secured Framework for sustainable smart cities by leveraging blockchain and machine learning,” Journal of Systems Architecture, vol. 115, p. 101954, May 2021, doi: 10.1016/j.sysarc.2020.101954.