Optimal and Efficient Searchable Encryption with Single Trapdoor for Multi-Owner Data Sharing in Federated Cloud Computing
Main Article Content
Abstract
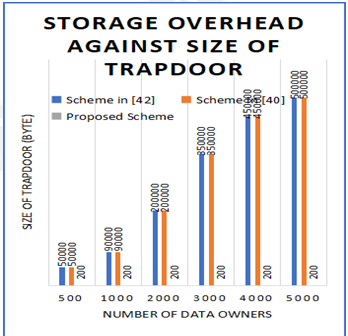
Cloud computing, an Internet based computing model, has changed the way of data owners store and manage data. In such environment, data sharing is very important with more efficient data access control. Issuing an aggregate key to users on data enables and authorizes them to search for data of select encrypted files using trapdoor or encrypted keyword. The existing schemes defined for this purpose do have certain limitations. For instance, Cui et al. scheme is elegant but lacks in flexibility in access control in presence of multiple data owners sharing data to users. Its single trapdoor approach needs transformation into individual trapdoors to access data of specific data owner. Moreover, the existing schemes including that of Cui et al. does not support federated cloud. In this paper we proposed an efficient key aggregate searchable encryption scheme which enables multiple featuressuch as support for truly single aggregate key to access data of many data owners, federated cloud support,query privacy, controlled search process and security against cross-pairing attack. It has algorithms for setup, keygen, encrypt, extract, aggregate, trapdoor, test and federator. In multi-user setting it is designed to serve data owners and users with secure data sharing through key aggregate searchable encryption The proposed scheme supports federated cloud. Experimental results revealed that the proposed scheme is provably secure withrelatively less computational overhead and time complexity when compared with the state of the art.
Article Details
References
Changyu Dong a, Giovanni Russello and Naranker Dulay. (2011). Shared and Searchable Encrypted Data for Untrusted Servers. Journal of Computer Security. 19(3), pp.367-397.
J. Li, X. Chen, M. Li, J. Li, P. P. C. Lee, and W. Lou. (2014). Secure Deduplication with Efficient and Reliable Convergent Key Management. IEEE Trans. Parallel Distrib. Syst.. 25(6), pp.1615-1625.
C. Gentry, C. Peikert, and V. Vaikuntanathan. (2008). Trapdoors for Hard Lattices and New Cryptographic Constructions. STOC, pp.1-41.
X. Lu, W. Yin, Q. Wen, Z. Jin, and W. Li. (2018). A Lattice-Based Unordered Aggregate Signature Scheme Based on the Intersection Method. IEEE Access,. 6, p.33986–33994.
P. V. Reddy and P. Gopal. (2015). Identity-based key-insulated aggregate signature scheme. J. King Saud Univ.-Comput. Inf. Sci.. 29, pp.1-8. Online].
Baojiang Cui, Zheli Liu and Lingyu Wang. (2014). Key-Aggregate Searchable Encryption (KASE) for Group Data Sharing via Cloud Storage. IEEE TRANSACTIONS ON COMPUTERS. 6(1), pp.1-13. Online].
Xiaofeng Chen, Jin Li, Xinyi Huang, Jingwei Li, Yang Xiang, and Duncan S. Wong. (2013). Secure Outsourced Attribute-based Signatures. IEEE Transactions on Parallel and Distributed Systems. 65(8), pp.1-11.
. Li, J. Li, X. Chen, C. Jia, and Z. Liu,. (2012). Efficient Keyword Search over Encrypted Data with Fine-Grained Access Control in Hybrid Cloud. 6th Int. Conf. Netw, pp.490-502.
Mr. Dharmesh Dhabliya. (2012). Intelligent Banal type INS based Wassily chair (INSW). International Journal of New Practices in Management and Engineering, 1(01), 01 - 08. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/2
R. Curtmola, J. Garay, S. Kamara, and R. Ostrovsky,. (2011). Searchable symmetric encryption: Improved definitions and efficient constructions. Department of Computer Science, New Jersey Institute of Technology, pp.895-934.
C.-K. Chu, S. S. M. Chow, W.-G. Tzeng, J. Zhou, and R. H. Deng. (2014). Key-Aggregate Cryptosystem for Scalable Data Sharing in Cloud Storage. IEEE Trans. Parallel Distrib.. 25(2), pp.468-477.
C. Gu, Y. Guang, Y. Zhu, and Y. Zheng. (2013). Public Key Encryption with Keyword Search from Lattices. Int. J. Inf. Technol. 19(1), pp.1-10.
Sharma, M. K. (2021). An Automated Ensemble-Based Classification Model for The Early Diagnosis of The Cancer Using a Machine Learning Approach. Machine Learning Applications in Engineering Education and Management, 1(1), 01–06. Retrieved from http://yashikajournals.com/index.php/mlaeem/article/view/1
D. Boneh, C. Gentry, and B. Waters,. (2005). Collusion Resistant Broadcast Encryption With Short Ciphertexts and Private Keys. CRYPTO. 3621, pp.258-275.
O. Regev. (2005). On Lattices, Learning with Errors, Random Linear Codes, and Cryptography. J. ACM,. 56(6), pp.84-93.
J. Li and K. Kim. (2010). Hidden attribute-based signatures without anonymity revocation. Department of Computer Science, Korea Advanced Institute of Science and Technology. 180(9), pp.1681-1689.
C. Gentry, A. O’Neill, and L. Reyzin. (2018). A Unified Framework for Trapdoor-Permutation-Based Sequential Aggregate Signatures. PKC PTII, pp.1-17.
D. Boneh, C. Gentry, and M. Hamburg. (2007). Space-Efficient Identity Based Encryption Without Pairings. FOCS. , p.647–657.
J. Alwen and C. Peikert. (2010). Generating Shorter Bases for Hard Random Lattices. Theory Comput. Syst. 48(.), pp.535-553.
H. Du, Q. Wen, and S. Zhang. (2018). An Efficient Certificateless Aggregate Signature Scheme without Pairings for Healthcare Wireless Sensor Network. IEEE Access. 7, pp.1-14.
Peter W. Shor. (1999). Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer?. AMS subject classifications. 41(2), pp.303-332.
Z. Liu, Z. Wang, X. Cheng, C. Jia, and K. Yuan,. (2013). ‘‘Multi-user searchable encryption with coarser-grained access control in hybrid cloud,’’. 4th Int. Conf. Emerg. Intell. Data Web Technol, pp.249-255.
M. Noroozi and Z. Eslami,. (2019). Public key encryption with keyword search: a generic construction secure against online and offline keyword guessing a. J. Ambient Intell. Humanized Comput, pp.1-12.
X. Zhang, Y. Tang, H. Wang, C. Xu, Y. Miao, and H. Cheng. (2019). Lattice-based proxy-oriented identity-based encryption with keyword search for cloud storage. Inf. Sci. 494, pp.193-207.
Dhabliya, P. D. . (2020). Multispectral Image Analysis Using Feature Extraction with Classification for Agricultural Crop Cultivation Based On 4G Wireless IOT Networks. Research Journal of Computer Systems and Engineering, 1(1), 01–05. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/10
D. Wu, X. Wang, and Q. Gan. (2016). Public Key Encryption with Keyword Search from Lattices in Multiuser Environments. Math. Problems Eng, pp.1-8.
R. A. Popa and N. Zeldovich. (2019). Multi-Key Searchable Encryption. Cryptol. ePrint Arch., Tech, pp.1-18.
Xiaojun Zhanga,b,c, Huaxiong Wangb and Chunxiang Xu. (2018). Identity-based key-exposure resilient cloud storage public auditing scheme from lattices. Information Sciences, pp.1-29.
Smith, J., Jones, D., Martinez, J., Perez, A., & Silva, D. Enhancing Engineering Education through Machine Learning: A Case Study. Kuwait Journal of Machine Learning, 1(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/86
X. Zhang, C. Xu, H. Wang, Y. Zhang, and S. Wang. (2021). ‘‘FS-PEKS: Lattice based forward secure public-key encryption with keyword search for cloud-assisted industrial Inte. IEEE Trans. Dependable Secure Comput., to be published, pp.1-16.
F. Zhao, T. Nishide, and K. Sakurai. (2012). Multi-User Keyword Search Scheme for Secure Data Sharing with Fine-Grained Access Control. Int. Conf. Inf. Secur. Cryptol, pp.406-418. Online].
Muhammad Khan, Machine Learning for Predictive Maintenance in Manufacturing: A Case Study , Machine Learning Applications Conference Proceedings, Vol 1 2021.
S. Agrawal, D. Boneh, and X. Boyen,. (2010). Lattice Basis Delegation in Fixed Dimension and Shorter-Ciphertext Hierarchical IBE. CRYPTO, pp.98-115.
YANQING YAO, ZHENGDE ZHAI , JIANWEI LIU , AND ZHOUJUN L. (2019). Lattice-Based Key-Aggregate (Searchable) Encryption in Cloud Storage. J. Softw. 7, pp.164544-164555.
YANQING YAO, Zhengde Zhai , Jianwei Liu , Zhoujun Li. (2016). Lattice-based Key-Aggregate (Searchable) Encryption in Cloud Storage. IEEE Access. 4, pp.1-13.
S.Vinothkumar, J.Amutharaj and Jeyabalan. (2021). A COMPREHENSIVE STUDY OF CRYPTOGRAPHY AND KEY MANAGEMENT BASED SECURITY IN CLOUD COMPUTING. 1Department of CSE, ACS College of Engineering, Bengaluru,. 27(3), pp.1909-1923.
Mahnaz Noroozi , Ziba Eslami. (2019). Public key encryption with keyword search. Ambient Intelligence and Humanized Computing , pp.1-12. Online].
Rui Araújo and António Pinto. (2021). Secure Remote Storage of Logs with Search Capabilities. J. Cybersecur. Priv, pp.340-364. Online].
YANQING YAO, Zhengde Zhai, Jianwei Liu and , Zhoujun Li 3. (2016). Lattice-Based Key-Aggregate (Searchable) Encryption in Cloud Storage. IEEE Access. 4, pp.1-13.
Rajat Chaudhary, Anish Jindal, Gagangeet Singh Aujla, Neeraj Kumar, Ashok Kumar. (2018). LSCSH: Lattice-Based Secure Cryptosystem for Smart Healthcare in Smart Cities Environment. IEEE Communications Magazine , pp.24-32.
Shanthi D.L, Sahana .P, Abishek .P, Shilpa A.S, Juhi Kumari . (2016). A Study on the Security Issues , Algorithms and Schemes towards a more secure Cloud Storage. International Journal of Scientific & Engineering Research. 7(3), pp.729-735. Online].
Chiara Marcolla, Victor Sucasas and Marc Manzano, Riccardo Bassoli. (2022). Survey on Fully Homomorphic Encryption, Theory and Applications. IEEE, pp.1-40.
Jelizaveta Vakarjuk, Nikita Snetkov and Jan Willemson. (2021). DiLizium: A Two-Party Lattice-Based Signature Scheme. Entropy, pp.1-30. Online].
A. Boorghanya S. Bayat-Sarmadib , and R. Jalili. (2018). Practical provably-secure authenticated encryption schemes using lattice-based pseudorandom function SPRING. Scientia Iranica. 25(6), pp.3442-3460.
Tong Li, Zheli Liu, Ping Li, Chunfu Jia, Zoe L Jiang, and Jin Li. Verifiable searchable encryption with aggregate keys for data sharing in outsourcing storage. In Australasian Conference on Information Security and Privacy, pages 153–169. Springer, 2016.
Haijiang Wang, Xiaolei Dong, Zhenfu Cao, Dongmei Li, and Nanyuan Cao. Secure key-aggregation authorized searchable encryption. Science China Information Sciences, 62(3):39111, 2019.
Cui BJ, Liu ZL, Wang LY, 2016. Key-aggregate searchable encryption (KASE) for group data sharing via cloud storage. IEEE Trans Comput, 65(8):2374-2385. https://doi.org/10.1109/TC.2015.2389959