An Enhanced Scammer Detection Model for Online Social Network Frauds Using Machine Learning
Main Article Content
Abstract
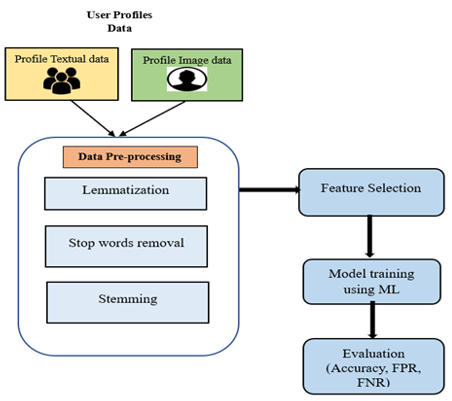
The prevalence of online social networking increase in the risk of social network scams or fraud. Scammers often create fake profiles to trick unsuspecting users into fraudulent activities. Therefore, it is important to be able to identify these scammer profiles and prevent fraud such as dating scams, compromised accounts, and fake profiles. This study proposes an enhanced scammer detection model that utilizes user profile attributes and images to identify scammer profiles in online social networks. The approach involves preprocessing user profile data, extracting features, and machine learning algorithms for classification. The system was tested on a dataset created specifically for this study and was found to have an accuracy rate of 94.50% with low false-positive rates. The proposed approach aims to detect scammer profiles early on to prevent online social network fraud and ensure a safer environment for society and women’s safety.
Article Details
References
Kayes, Imrul, and Adriana Iamnitchi. "Privacy and security in online social networks: A survey." Online Social Networks and Media 3 (2017): 1-21
Guo, Zhen, Jin-Hee Cho, Ray Chen, Srijan Sengupta, Michin Hong, and Tanushree Mitra. "Online social deception and its countermeasures: A survey." IEEE Access 9 (2020): 1770-1806.
Jain, Ankit Kumar, Somya Ranjan Sahoo, and Jyoti Kaubiyal. "Online social networks security and privacy:
comprehensive review and analysis." Complex & Intelligent Systems 7, no. 5 (2021): 2157-2177.
T. J. Holt and A. M. Bossler, The palgrave handbook of International cybercrime and cyberdeviance. 2020. doi: 10.1007/978-3-319-78440-3.
Rathore, Shailendra, Pradip Kumar Sharma, Vincenzo Loia, Young-Sik Jeong, and Jong Hyuk Park. "Social network security: Issues, challenges, threats, and solutions." Information sciences 421 (2017): 43-69.
Apte, Manoj, Girish Keshav Palshikar, and Sriram Baskaran. "Frauds in online social net-works: A review." Social networks and surveillance for society (2019): 1-18.
Cross C. (2020) Romance Fraud. In: Holt T., Bossler A. (eds) The Palgrave Handbook of International Cybercrime and Cyberdeviance. Palgrave Macmillan, Cham. https://doi.org/10.1007/978-3-319-90307-1_41-1
F. Ahmed and M. Abulaish, “An MCL-based approach for spam profile detection in online social networks,” in Proc. IEEE 11th Int. Conf. Trust, Security. Privacy Comput. Commun., 2012, pp. 602–608
M. Conti, R. Poovendran, and M. Secchiero, “Fakebook: Detecting fake profiles in on-line social networks,” in Proc. IEEE/ACM Int. Conf. Adv. Social Network. Anal. Mining., 2012, pp. 1071–1078.
S. Gurajala, J. S. White, B. Hudson, and J. N. Matthews, “Fake twitter accounts: Profile characteristics obtained using an activity-based pattern detection approach,” in Proc. Int. Conf. SocialMedia Soc., 2015, pp. 1–7
S. Gurajala, J. S. White, B. Hudson, B. R. Voter, and J. N. Matthews, “Profile characteristics of fake twitter accounts,” Journal of Big Data, vol. 3, no. 2, 2016, 2053951716674236
M. BalaAnand, S. Sankari, R. Sowmipriya, and S. Sivaranjani, “Identifying fake user’s in social networks using non verbal behavior,” International Journal Technol. Eng. Syst., vol. 7, no. 2, pp. 157–161, 2015.Technol. Eng. Syst., vol. 7, no. 2, pp. 157–161, 2015
Y. Boshmaf et al., “Integro: Leveraging victim prediction for robust fake account detection in OSNs,” in Proc.Netw.Distributed Syst. Secur. Symp., 2015, pp. 8–11
M. Meligy, H. M. Ibrahim, and M. F. Torky, “Identity verification mechanism for detecting fake profiles in online social networks,” Int. J. Comput. Netw. Inf. Secur., vol. 9, no. 1, pp. 31–39, 2017.
J. Jia, B. Wang, and N. Z. Gong, “Random walk based fake account detection in online social networks,” in Proc. 47th Annu. IEEE/IFIP Int. Conf. Dependable Syst. Netw., 2017, pp. 273–284.
S. Khaled, N. El-Tazi, and H. M. Mokhtar, “Detecting fake accounts on social media,” in Proc. IEEE Int. Conf. Big Data., 2018, pp. 3672–3681
N. Singh, T. Sharma, A. Thakral, and T. Choudhury, “Detection of fake profile in online social networks using machine learning,” in Proc. IEEE Int. Conf. Adv. Comput. Commun. Eng., 2018, pp. 231–234.
S. Revathi and M. Suriakala, “Profile similarity communication matching approaches for detection of duplicate profiles in online social network,” in Proc. IEEE 3rd Int. Conf. Comput. Syst. Inf. Technol. Sustain. Solutions, 2018, pp. 174–182.
M. Suriakala and S. Revathi, “Privacy protected system for vulnerable users and cloning profile detection using data mining approaches,” in Proc. IEEE 10th Int. Conf. Adv. Comput., 2018, pp. 124–132.
M. A. Wani, N. Agarwal, S. Jabin, and S. Z. Hussain, “Analyzing real and fake users in Facebook network based on emotions,” in Proc. IEEE 11th Int. Conf. Commun. Syst. Netw., 2019, pp. 110–117
P.Wanda and H. J. Jie, “Deepprofile: Finding fake profile in online social network using dynamic CNN,” Journal of Information Security, Appl., vol. 52, pp. 1–13, 2020
P. Pourghomi, M. Dordevic, and F. Safieddine, “Facebook fake profile identification: Technical and ethical considerations,” Int. Journal . Pervasive Comput. Commun., vol. 16, pp. 101–112, 2020.
M. M. Swe and N. N. Myo, “Fake accounts detection on twitter using blacklist,” in Proc. IEEE/ACIS 17th Int. Conf. Comput. Inf. Sci., 2018, pp. 562–566. E. M. Clark, J. R.Williams, C. A. Jones, R. A. Galbraith, C.M. Danforth, and P. S. Dodds, “Sifting robotic from organic text: A natural language approach for detecting automation on twitter,” J. Comput. Sci., vol. 16, pp. 1–7, 2016.
M. U. S. Khan, M. Ali, A. Abbas, S. U. Khan, and A. Y. Zomaya “Segregating spammers and unsolicited bloggers from genuine experts on twitter,” IEEE Trans. Dependable Secure Comput., vol. 15, no. 4, pp. 551–560, Jul./Aug. 2018
M. U. S. Khan, M. Ali, A. Abbas, S. U. Khan, and A. Y. Zomaya, “Segregating spammers and unsolicited bloggers from genuine experts on twitter,” IEEE Trans. Dependable Secure Comput., vol. 15, no. 4, pp. 551–560, Jul./Aug. 2018.
M. Egele, G. Stringhini, C. Kruegel, and G. Vigna, “COMPA: Detecting compromised accounts on social networks,” in Proc. Netw. Distrib. Syst. Secur. Symp., 2013
P.V. Phad andM.Chavan, “Detecting compromised high-profile accounts on social networks,” in Proc. IEEE 9th Int. Conf. Comput., Commun. Netw. Technol., 2018, pp. 1–4
G. Karegowda, A. Manjunath, and M. Jayaram, “Comparative study of attribute selection using gain ratio and correlation based feature selection,” Int. J. Inf. Technol. Knowl. Manage., vol. 2, no. 2, pp. 271–277, 2010.
Chakraborty, J. Sundi, S. Satapathy, “SPAM: A framework for social profile abuse monitoring,” Stony Brook Univ., Stony Brook, NY, USA, CSE508 Report, 2012.
W. Hua and Y. Zhang, “Threshold and associative based classification for social spam profile detection on twitter,” in Proc. 9th Int. Conf. Semantics, Knowl. Grids, 2013, pp. 113–120.
K. S. Adewole, N. B. Anuar, A. Kamsin, and A. K. Sangaiah, “SMSAD: Aframework for spammessage and spam account detection,” Multimedia Tools Appl., vol. 78, no. 4, pp. 3925–3960, 2019.
E. V. D. Walt and J. Eloff, “Using machine learning to detect fake identities: Bots vs humans,” IEEE Access, vol. 6, pp. 6540–6549, 2018.
M. Mateen, M. A. Iqbal, M. Aleem, and M. A. Islam, “A hybrid approach for spam detection for Twitter,'' in Proc. 14th Int. Bhurban Conf. Appl. Sci. Technol. (IBCAST), Jan. 2017, pp. 466_471
Jong, Koen. "Detecting the online romance scam: Recognising images used in fraudulent dating profiles." Master's thesis, University of Twente, 2019.
Suarez-Tangil, Guillermo, et al. "Automatically dismantling online dating fraud." IEEE Transactions on Information Forensics and Security 15 (2019): 1128-1137.’.
S. Al-Rousan, A. Abuhussein, F. Alsubaei, O. Kahveci, H. Farra, and S. Shiva, “Social-Guard: Detecting Scammers in Online Dating”, IEEE Int. Conf. Electro Inf. Technol., vol. 2020-July, no. August, pp. 416–422, 2020, doi: 10.1109/EIT48999.2020.9208268.
Aytu_g Onan, Serdar Koruko_glu, and Hasan Bulut. Ensemble of keyword extraction methods and classifiers in text classification. Expert Systems with Applications, 57:232{247, 2016
Liangxiao Jiang, Chaoqun Li, Shasha Wang, and Lungan Zhang. Deep feature weighting for Naive Bayes and its application to text classification. Engineering Applications of Artificial Intelligence, 52:26{39, 2016.
Bo Tang, Haibo He, Paul M Baggenstoss, and Steven Kay. “A Bayesian classification approach using class-specific features for text categorization”, IEEE Transactions on Knowledge and Data Engineering, 28(6):1602{1606, 2016.
Lungan Zhang, Liangxiao Jiang, Chaoqun Li, and Ganggang Kong. Two feature weighting approaches for naive bayes text classi_ers. Knowledge-Based Systems, 100:137{144, 2016.
Bochkovskiy, Alexey, Chien-Yao Wang, and Hong-Yuan Mark Liao. "Yolov4: Optimal speed and accuracy of object detection." arXiv preprint arXiv:2004.10934 (2020).
Mahesh, Batta. "Machine learning algorithms-a review." International Journal of Science and Research (IJSR), (381-386)2020.
P. K. Roy and S. Chahar, "Fake Profile Detection on Social Networking Websites: A Comprehensive Review," in IEEE Transactions on Artificial Intelligence, vol. 1, no. 3, pp. 271-285, Dec. 2020, doi: 10.1109/TAI.2021.3064901.
Jiang, Zicong, Liquan Zhao, Shuaiyang Li, and Yanfei Jia. "Real-time object detection method based on improved YOLOv4-tiny." arXiv preprint arXiv:2011.04244 (2020).