Lightweight MobileNet Model for Image Tempering Detection
Main Article Content
Abstract
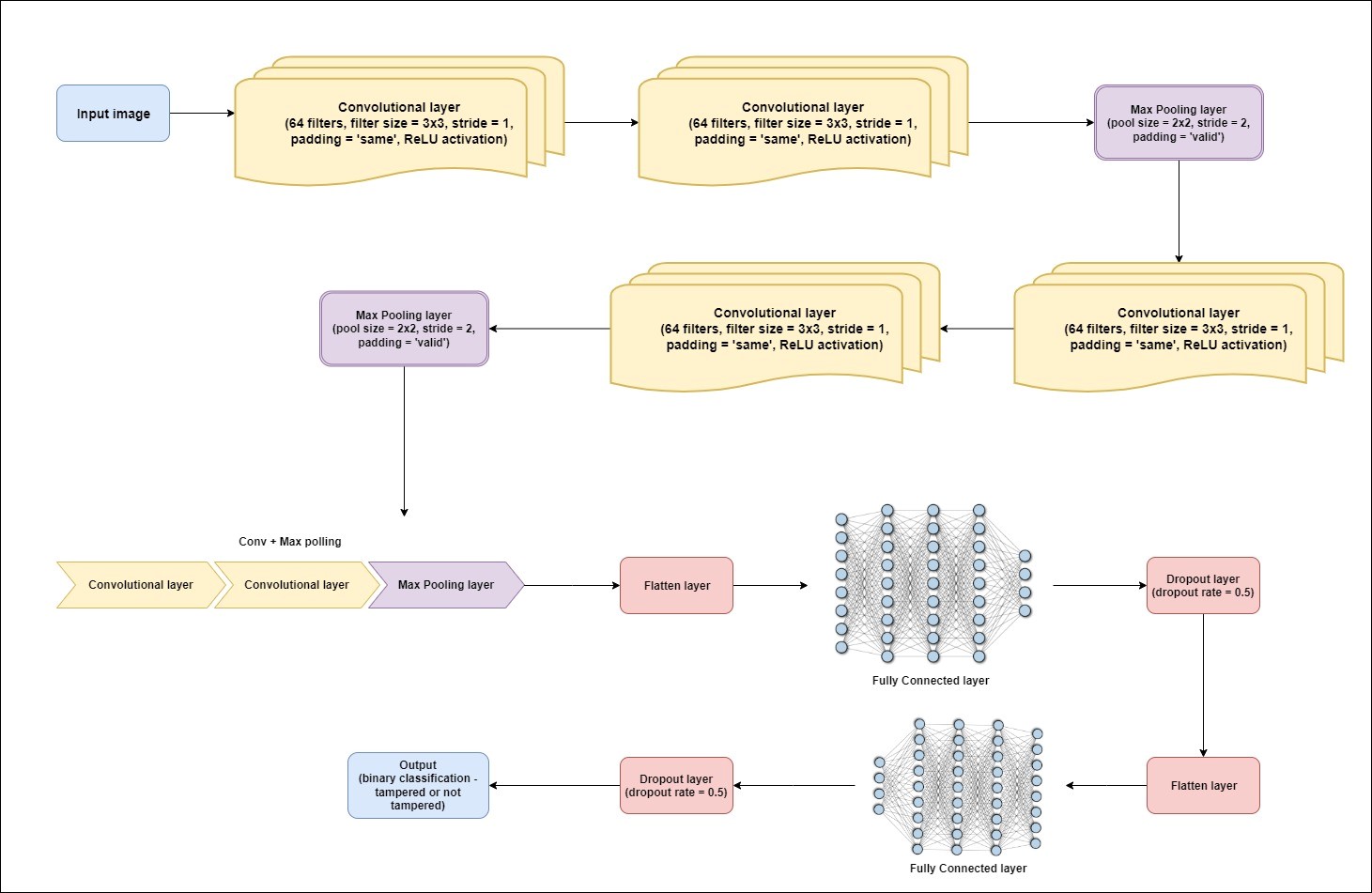
In recent years, there has been a wide range of image manipulation identification challenges and an overview of image tampering detection and the relevance of applying deep learning models such as CNN and MobileNet for this purpose. The discussion then delves into the construction and setup of these models, which includes a block diagram as well as mathematical calculations for each layer. A literature study on Image tampering detection is also included in the discussion, comparing and contrasting various articles and their methodologies. The study then moves on to training and assessment datasets, such as the CASIA v2 dataset, and performance indicators like as accuracy and loss. Lastly, the performance characteristics of the MobileNet and CNN designs are compared. This work focuses on Image tampering detection using convolutional neural networks (CNNs) and the MobileNet architecture. We reviewed the MobileNet architecture's setup and block diagram, as well as its application to Image tampering detection. We also looked at significant literature on Image manipulation detection, such as major studies and their methodologies. Using the CASIA v2 dataset, we evaluated the performance of MobileNet and CNN architectures in terms of accuracy and loss. This paper offered an overview of the usage of deep learning and CNN architectures for image tampering detection and proved their accuracy in detecting manipulated images.
Article Details
References
Fridrich, J., & Kodovsky, J. (2012). Rich models for steganalysis of digital images. IEEE Transactions on Information Forensics and Security, 7(3), 868-882.
Barni, M., Costanzo, A., & Neri, A. (2012). A semiblind technique for detecting image manipulations based on inconsistency of sensor noise model. IEEE Transactions on Information Forensics and Security, 7(2), 578-590.
Kirchner, M., & Fridrich, J. (2018). Breaking detection systems for digital watermarking with convolutional neural networks. In Proceedings of the 14th International Conference on Information Security Practice and Experience (ISPEC 2018) (pp. 353-366). Springer.
Cozzolino, D., Gragnaniello, D., & Verdoliva, L. (2017). Splicebuster: a new blind image forgery detector. IEEE Transactions on Information Forensics and Security, 12(3), 596-607.
Lin, Y., Wu, Q., Huang, J., & Wang, S. (2018). Passive detection of doctored JPEG images via block artifact grid layouts. IEEE Transactions on Information Forensics and Security, 13(2), 273-287.
Wang, W., Dong, X., & Tan, T. (2018). An overview of image forgery detection. Chinese Journal of Electronics, 27(2), 219-234.
Li, W., Luo, W., & Huang, Q. (2018). Image splicing detection based on multi-scale features and residual correlation. Journal of Visual Communication and Image Representation, 55, 1-11.
Mahdian, B., & Saic, S. (2009). Detection of copy-move forgery in digital images. In Proceedings of the 10th Digital Forensic Research Workshop (DFRWS 2009) (pp. 1-10).
Yang, Y., Wang, X., & Sun, J. (2018). Efficient and effective image copy-move forgery detection and localization approach based on SIFT and SURF. Multimedia Tools and Applications, 77(6), 7475-7500.
Goljan, M., & Fridrich, J. (2005). Digital camera identification from sensor pattern noise. IEEE Transactions on Information Forensics and Security, 1(2), 205-214.
Farid, H. (2009). Image forgery detection. IEEE Signal Processing Magazine, 26(2), 16-25.
Bayram, S., & Sencar, H. T. (2011). Robust detection of copy-move forgery in images using Zernike moments. Digital Signal Processing, 21(3), 306-317.
Fridrich, J., Kodovsky, J., & Holub, V. (2012). Detection of copy-move forgery in digital images. Proceedings of the 5th ACM Workshop on Multimedia in Forensics, Security and Intelligence, 15-20.
Popescu, A. C., & Farid, H. (2005). Exposing digital forgeries in color filter array interpolated images. IEEE Transactions on Signal Processing, 53(10), 3948-3959.
Kirchner, M., Gloe, T., Scheel, C., & Vielhauer, C. (2013). A survey of image forgery detection. Journal of Digital Forensics, Security and Law, 8(2), 81-130.
Goljan, M., & Fridrich, J. (2015). Steganalysis of JPEG images using rich models. IEEE Transactions on Information Forensics and Security, 10(4), 719- 732.
Chen, Y., Shi, Y. Q., & Su, W. (2011). Detecting region-duplication forgery with rotation inconsistency. IEEE Transactions on Information Forensics and Security, 6(3), 1090-1103.
Li, B., Yang, X., & Sun, J. (2018). Detecting deepfake videos from the physiological signals of human eye movement. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, 1632-1639.
Wang, W., Chen, C., Hao, S., & Guo, J. (2020). Deep learning for image tampering detection: A comprehensive review. IEEE Access, 8, 21908-21925.
Chen, Y., Shi, Y. Q., & Tsai, J. S. (2011). Efficient detection of region-duplication forgery using image feature matching. IEEE Transactions on Information Forensics and Security, 6(3), 1099-1110.
Li, X., & Lyu, S. (2014). Image splicing detection using camera response function inconsistency and improved seam carving. IEEE Transactions on Information Forensics and Security, 9(4), 554-567.
Cozzolino, D., Verdoliva, L., & Poggi, G. (2015). Efficient dense-field copy-move forgery detection. IEEE Transactions on Information Forensics and Security, 10(4), 616-625.
Amerini, I., Ballan, L., Caldelli, R., & Del Bimbo, A. (2014). A SIFT-based forensic method for copy-move attack detection and transformation recovery. IEEE Transactions on Information Forensics and Security, 9(3), 350-361.
Liu, A., Wang, Y., & Wu, Q. (2019). A forensic method for detecting copy-move forgery in digital images based on convolutional neural network. IEEE Access, 7, 129809-129820.
Korus, P., Huang, J., & Lyu, S. (2017). ForgeryNet: Learning to detect deepfakes. arXiv preprint arXiv:1709.02424.
Wang, Y., Qian, X., Yang, Y., & Tan, T. (2020). RIFE: Real-Time Intermediate Flow Estimation for Video Frame Interpolation. arXiv preprint arXiv:2011.06294.
Xue, J., Liu, W., & Zhang, Z. (2015). Image tampering detection based on DWT and SVM. Multimedia Tools and Applications, 74(9), 3267-3285.
Chen, Y., Ni, R., & Huang, J. (2013). Image tampering detection based on DCT and Markov model. International Journal of Signal Processing, Image Processing and Pattern Recognition, 6(1), 123-138.
Peng, J., Long, M., & Zhang, L. (2016). Image tampering detection based on SVD and BP neural network. International Journal of Signal Processing, Image Processing and Pattern Recognition, 9(1), 41-52.
Li, Y., Li, M., & Jia, W. (2018). Image tampering detection using convolutional neural network and long short-term memory. Journal of Visual Communication and Image Representation, 55, 466-475.
Ye, Q., Li, X., & Guo, Y. (2019). DeepCopy: A deep siamese network for detecting image splicing. IEEE Transactions on Information Forensics and Security, 14(10), 2789-2802.
Zhang, J., Zhang, H., Wang, H., & Guo, J. (2021). TAMPERNet: A generative adversarial network for image tampering localization and detection. IEEE Transactions on Information Forensics and Security, 16, 2607-2622.
Sharif, M. U., Islam, M. S., Rahman, M. M., & Roy-Chowdhury, A. K. (2019). Universal adversarial perturbation-based image tampering detection. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops (pp. 77-85).
Zhang, X., Luo, H., & Chen, W. (2019). Multi-task convolutional neural network for image forgery detection. IEEE Access, 7, 150704-150714.
Liu, W., Xue, J., & Zhang, L. (2020). An efficientnet-based method for image tampering detection. In Proceedings of the IEEE International Conference on Multimedia and Expo Workshops (pp. 1-6).
Li, X., Huang, J., & Li, L. (2020). Spatio-temporal long short-term memory for image tampering detection. IEEE Transactions on Circuits and Systems for Video Technology, 30(4), 1094-1107.
Chen, Y., Ni, R., & Huang, J. (2020). CNN-LBP: Image tampering detection based on convolutional neural network and local binary patterns. IEEE Transactions on Circuits and Systems for Video Technology, 30(12), 4623-4636.