A Secured Software Defined Network Architecture for Mini Net using POX Controller
Main Article Content
Abstract
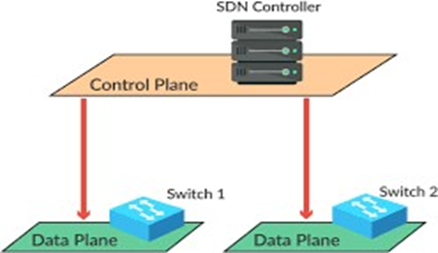
SDN (software-defined networks) is a new technology that stems from numerous network security enhancements. It handles network data in a flexible manner using highly secure frameworks. The secure SDN model's purpose is to ensure data security. The proposed idea to be executed is a robust firewall protection in a mini net employing a POX controller. In order to deal with network-induced dangers, the huge network connectivity influenced environment requires additional protection. The proposed effort focuses on creating a secure SDN simulation architecture that is managed by Open Source POX Controller. Through a POX-controlled traffic management system and a Fingerprint-enabled authentication technique, the system provides multilayer security. The enhanced security is achieved by assessing network traffic as either elephant or mouse flow and selecting the appropriate security level based on data complexity. Mininet is run in a virtual cloud, where protocols and tools are tested and supported by a virtual machine (VM). The novelty is to produce a secure SDN topology was created using a python-based POX controller in the suggested technique. It also provides a low-cost solution as well as rapid development in conjunction with industrial networks.
Article Details
References
Kaur, S., Singh, J. and Ghumman, N.S., August. Network programmability using POX controller. In ICCCS International conference on communication, computing & systems, IEEE (2014), (Vol. 138, p. 70). sn.
Srinivasa, K.G. and GM, S., Introduction to Data Analytics. In Network Data Analytics 2018, (pp. 3-28). Springer, Cham.
Miner, G., Elder, J., IV, & Hill, T,. Practical text mining and statistical analysis for non-structured text data applications. (2012), Cambridge: Academic Press.
Boutaba, R., Salahuddin, M.A., Limam, N., Ayoubi, S., Shahriar, N., Estrada-Solano, F. and Caicedo, O.M., A comprehensive survey on machine learning for networking: evolution, applications and research opportunities. Journal of Internet Services and Applications, 9(1), (2012), pp.1-99.
B. Ahmed, N. Ahmed, A. W. Malik, M. Jafri and T. Hafeez, "Fingerprinting SDN Policy Parameters: An Empirical Study," in IEEE Access, vol. 8, pp. 142379-142392, 2020, doi: 10.1109/ACCESS.2020.3012176.
M. W. Hussain, K. H. K. Reddy, J. J. P. C. Rodrigues and D. S. Roy, "An Indirect Controller- Legacy Switch Forwarding Scheme for Link Discovery in Hybrid SDN," in IEEE Systems Journal, vol. 15, no. 2, pp. 3142-3149, June 2021, doi: 10.1109/JSYST.2020.3011902.
S. Ejaz, Z. Iqbal, P. Azmat Shah, B. H. Bukhari, A. Ali and F. Aadil, "Traffic Load Balancing Using Software Defined Networking (SDN) Controller as Virtualized Network Function," in IEEE Access, vol. 7, pp. 46646-46658, 2019, doi: 10.1109/ACCESS.2019.2909356.
Y. Meng, Z. Huang, G. Shen and C. Ke, "SDN-Based Security Enforcement Framework for Data Sharing Systems of Smart Healthcare," in IEEE Transactions on Network and Service Management, vol. 17, no. 1, pp. 308- 318, March 2020, doi: 10.1109/TNSM.2019.2941214.
Q. Li, X. Zou, Q. Huang, J. Zheng and P. P. C. Lee, "Dynamic Packet Forwarding Verification in SDN," in IEEE Transactions on Dependable and Secure Computing, vol. 16, no. 6, pp. 915-929, 1 Nov.-Dec. 2019, doi: 10.1109/TDSC.2018.2810880.
X. He, J. Zheng, H. Dai, Y. Sun, W. Dou and G. Chen, "Buffer-Assisted Network Updates in Timed SDN," in IEEE Transactions on Communications, vol. 69, no. 10, pp. 6822-6837, Oct. 2021, doi: 10.1109/TCOMM.2021.3093929.
M. Rezaee and M. H. Yaghmaee Moghaddam, "SDN-Based Quality of Service Networking for Wide Area Measurement System," in IEEE Transactions on Industrial Informatics, vol. 16, no. 5, pp. 3018-3028, May 2020, doi: 10.1109/TII.2019.2893865.
A. Erfanian, F. Tashtarian, A. Zabrovskiy, C. Timmerer and H. Hellwagner, "OSCAR: On Optimizing Resource Utilization in Live Video Streaming," in IEEE Transactions on Network and Service Management, vol. 18, no. 1, pp. 552-569, March 2021, doi: 10.1109/TNSM.2021.3051950.
Nunes, B.A.A., Mendonca, M., Nguyen, X.N., Obraczka, K. and Turletti, T., 2014. “A survey of software-defined networking: Past, present, and future of programmable networks”. IEEE Communications surveys & tutorials, 16(3), pp.1617-1634.
M. Ayaz, I. Baig, A. Abdullah, and I. Faye, “Review: A survey on routing techniques in underwater wireless sensor networks,” J. Netw. Comput. Appl., vol. 34, no. 6, pp. 1908–1927, Nov. 2011.
N. Li, J.-F. Martínez, J. M. Chaus, and M. Eckert, “A survey on underwater acoustic sensor network routing protocols,” Sensors, vol. 16, no. 3, p. 414, Mar. 2016.
P. Xie, J.-H. Cui, and L. Lao, “VBF: Vector-based forwarding protocol for underwater sensor networks,” in Proc. IFIP-TC6 Netw. Berlin, Germany: Springer-Verlag, 2006, pp. 1216–1221.
Klaine PV, Imran MA, Onireti O, Souza RD. “A survey of machine learning techniques applied to self organizing cellular networks”. IEEE CommunSurv Tutor. 2017; PP(99):1.
Nunes, B.; Mendonca, M.; Nguyen, X.; Obraczka, K.; Turletti, T., "A Survey of Software- Defined Networking: Past, Present, and Future of Programmable Networks," Communications Surveys & Tutorials, IEEE ,vol.PP, no.99, pp.1,18
Benson T. Data Set for IMC 2010 Data Center Measurement. 2010. http://pages.cs.wisc.edu/tbenson/IMC10_Data.html. Accessed 28 Dec 2017.
Abdulrahman Saad Alqahtani, “Security threats and countermeasures in software defined network using efficient and secure trusted routing mechanism”, Computer Communications, Volume 153, 2020, Pages 336-341, ISSN 0140-3664,.
Mosab Hamdan, Suleman Khan, Ahmed Abdelaziz, Shahidatul Sadiah, Nasir Shaikh-Husin, Sattam Al Otaibi, Carsten Maple, M.N. Marsono, DPLBAnt: Improved load balancing technique based on detection and rerouting of elephant flows in software-defined networks, Computer Communications, Volume 180, 2021, Pages 315-327, ISSN 0140-3664