Common Mechanism for Detecting Multiple DDoS Attacks
Main Article Content
Abstract
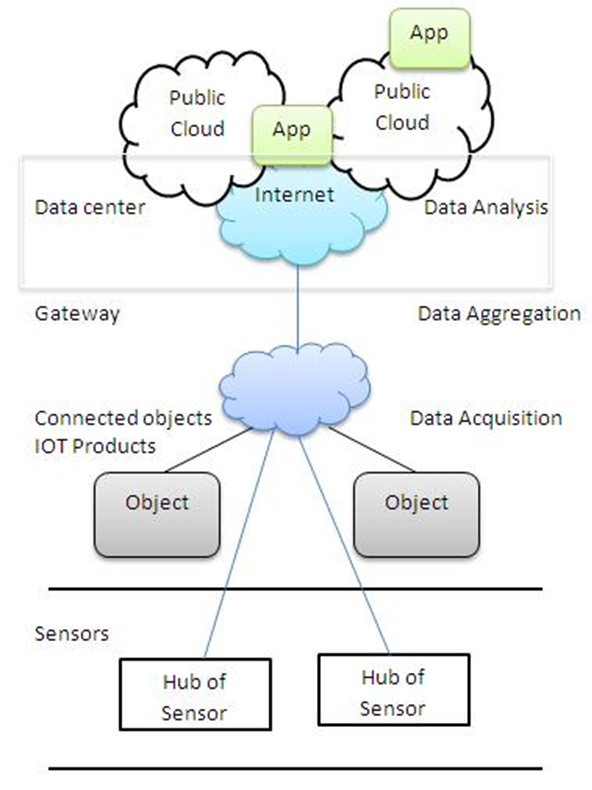
An important principle of an internet-based system is information security. Information security is a very important aspect of distributed systems and IoT (Internet of Things) based wireless systems. The attack which is more harmful to the distributed system and IoT-based wireless system is a DDoS (Distributed Denial of Service) attack since in this attack, an attacker can stop the work of all other connected devices or users to the network. For securing distributed applications, various intrusion detection mechanisms are used. But most existing mechanisms are only concentrated on one kind of DDoS attack. This paper focuses on the basic architecture of IoT systems and an overview of single intrusion detection systems. This paper presents a single detection method for different DDoS attacks on distributed systems with an IoT interface. In the future, the system will provide support for detecting and preventing different DDoS attacks in IoT-based systems.
Article Details
References
M. Abomhara and G. M. Koien, “Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks,” Journal of Cyber Security, Vol. 4, pp. 65-88, May 2015
Q. Jing et al., “Security of the Internet of Things: perspectives and challenges,” Springer Wireless Netw DOI 10.1007/s11276-014-0761-7, 2014.
Q. Xu et al., “Security enhancement for IoT communications Exposed to Eavesdroppers with Uncertain Locations,” IEEE Access, Special section on Internet of Things (IoT) in 5G Wireless Communications, Vol. 4, 2016 .
“DDoS Quick Guide,” National Cyber security and Communications Integration Center, Jan 2014.
TrapX Labs - A Division of TrapX Security, Inc, “Anatomy of an Attacks,” The Internet of Things (IoT) - The Hidden Danger Exposed, Mar 2017.
“IoT Threat Environment,” CISCO, White Paper, 2015.
Capgemini Consulting and Sogeti High Tech, “Securing the Internet of Things Opportunity: Putting Cyber security at the Heart of the IoT,” Nov 2014.
C. Kolias, G. Kambourakis, A. Stavrou, and J. Voas, “DDoS in the IoT: Mirai and other botnets,” IEEE Computer, vol. 50, no. 7, pp. 80–84, 2017.
Idris et. al., “HTTP Flood Mitigation Using Gateway Inspection and Second Chance Approach Analysis”, International Journal of Cyber-Security and Digital Forensics (IJCSDF), The Society of Digital Information and Wireless Communications (SDIWC), Vol. 6, No. 1, Jan. 2017, pp. 14-22.
J. Francois, I. Aib, and R. Boutaba, “FireCol: A Collaborative Protection Network for the Detection of Flooding DDoS Attacks”, IEEE/ACM Transactions on Networking, IEEE/ACM, Sept. 2012, 20 (6), pp.1828-1841.
S.H.C. Haris., et. al., "TCP SYN flood detection based on payload analysis", Proc. of 2010 IEEE Student Conference on Research and Development (SCOReD 2010), Putrajaya, Malaysia, Dec 2010, pp. 149-153
Myers, Robbie. “Attacks on TCP/IP Protocols.” Last accessed Jan 4, 2016.http://www.utc.edu/center-information-security-assurance/pdfs/course-paper-5620-attacktcpip.pdf.
Daehee Jang et.al., “ATRA: Address Translation Redirection Attack against Hardware-based External Monitors”, ACM, Scottsdale, Arizona, USA, CCS’14, November 3–7, 2014.
V. K. Yadav et. al., “DDA: An Approach to Handle DDoS (Ping Flood) Attack”,inProc. of International Conference on ICT for Sustainable Development, Advances in Intelligent Systems and Computing, Springer, Singapore, Vol.10, Issue No. 2, Sept. 2016.
D. C. MacFarland et. al., “Characterizing Optimal DNS Amplification Attacks and Effective Mitigation”, Springer, Vol. 8, No. 2, Mar. 2015.
M. Geva, A. Herzberg, and Y. Gev, “Bandwidth Distributed Denial of Service: Attacks and Defenses”, Article in IEEE Security and Privacy Magazine, Jan. 2013.
S. Sen, R. Choudhary and S. Nelakuditi, “CSMA/CN: Carrier Sense Multiple Access with Collision Notification”, proc. In MobiCom’10, ACM, Sept. 2010.
Nicolas Bruneau et. Al., “Stochastic Collision Attack”, International IEEE Transactions On Information Forensics And Security, Vol. 12, No. 9, Sept. 2017.
Lu, Zhuo, W. Wang, and C. Wang. "Camouflage Traffic: Minimizing Message Delay for Smart Grid Applications under Jamming." IEEE Transactions on Dependable & Secure Computing, Vol. 12, No.1, Feb. 2015, pp. 31-44.
Sachin D. Babar, Neeli R. Prasad, and Ramjee Prasad, “Activity Modelling and Countermeasures on Jamming Attack”, Journal of Cyber Security and Mobility, River Publisher, Vol. 2, No. 1, Apr. 2013.
Nazari Skrupsky et. al., “TamperProof: A Server-Agnostic Defense for parameter Tampering Attacks on Web Applications”, Proc. of the Third ACM Conference on Data and Application Security and Privacy (CODASPY’13), San Antonio, Texas, USA, Vol. 7, No. 2, Feb. 18–20, 2013.
M. N. Aman et. al., “Detecting data tampering attacks in synchrophasor network using time hopping”, 2016 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Ljubljana, 2016, pp. 1-6.
R. Latif et al., “EVFDT: An Enhanced Very Fast Decision Tree Algorithm for Detecting Distributed Denial of Service Attack in Cloud-Assisted Wireless Body Area Network”, Pub. Hindawi Corporation, Mobile Information Systems (HCMIS), Vol. 2015, Issue 5, Aug. 2015.
J. Wang., “Advanced Attack Tree-Based Intrusion Detection”, Pub. In Lough borough University Institutional Repository (LUIR), Leicestershire, UK, Feb 2012.
J. Wang et. al., “Augmented Attack Tree Modeling of Distributed Denial of Services and Tree-Based Attack Detection Method”, Proc. in 10th IEEE International Conference on Computer and Information Technology (CIT 2010), Oct. 2010.
P. Jayashree and Dr. K. S. Easwarakumar, “An Effective Defense Cum Prevention Of DDoS Attacks In Active Networks Using Attribute Trees”, Ubiquitous Computing and Communication Journal (UCCJ), Jun. 2008.
Yu. Chen et. al., “Distributed Change-Point Detection of DDoS Attacks: Experimen-tal Results on DETER Testbed”, Pres. in DETER Community Workshop on Cyber Security Experimentation and Test (DCWCSET), Jul. 2007..