Empirical Analysis of Privacy Preservation Models for Cyber Physical Deployments from a Pragmatic Perspective
Main Article Content
Abstract
The difficulty of privacy protection in cyber-physical installations encompasses several sectors and calls for methods like encryption, hashing, secure routing, obfuscation, and data exchange, among others. To create a privacy preservation model for cyber physical deployments, it is advised that data privacy, location privacy, temporal privacy, node privacy, route privacy, and other types of privacy be taken into account. Consideration must also be given to other types of privacy, such as temporal privacy. The computationally challenging process of incorporating these models into any wireless network also affects quality of service (QoS) variables including end-to-end latency, throughput, energy use, and packet delivery ratio. The best privacy models must be used by network designers and should have the least negative influence on these quality-of-service characteristics. The designers used common privacy models for the goal of protecting cyber-physical infrastructure in order to achieve this. The limitations of these installations' interconnection and interface-ability are not taken into account in this. As a result, even while network security has increased, the network's overall quality of service has dropped. The many state-of-the-art methods for preserving privacy in cyber-physical deployments without compromising their performance in terms of quality of service are examined and analyzed in this research. Lowering the likelihood that such circumstances might arise is the aim of this investigation and review. These models are rated according to how much privacy they provide, how long it takes from start to finish to transfer data, how much energy they use, and how fast their networks are. In order to maximize privacy while maintaining a high degree of service performance, the comparison will assist network designers and researchers in selecting the optimal models for their particular deployments. Additionally, the author of this book offers a variety of tactics that, when used together, might improve each reader's performance. This study also provides a range of tried-and-true machine learning approaches that networks may take into account and examine in order to enhance their privacy performance.
Article Details
References
Dou, Hui ?.?. ‘A Secure and Efficient Privacy-Preserving Data Aggregation Algorithm’. Journal of ambient intelligence and humanized computing 13.3 (2022): 1495–1503. Web.
Liu, Xiaowu ?.?. ‘Energy-Efficient Privacy-Preserving Data Aggregation Protocols Based on Slicing’. EURASIP journal on wireless communications and networking 2020.1 (2020): n. pag. Web.
Xie, Qi ?.?. ‘A Secure and Privacy-Preserving Authentication Protocol for Wireless Sensor Networks in Smart City’. EURASIP journal on wireless communications and networking 2021.1 (2021): n. pag. Web.
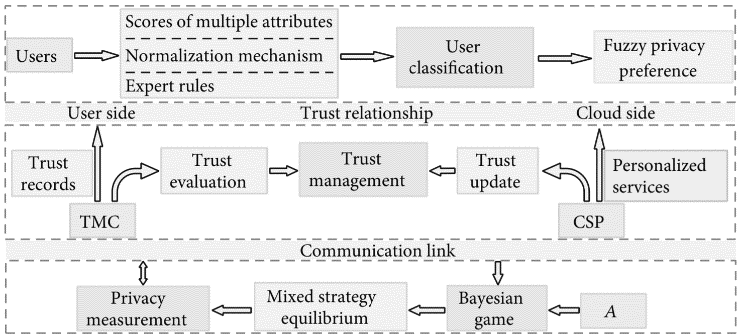
Bi, Renwan ?.?. ‘A Privacy-Preserving Personalized Service Framework through Bayesian Game in Social IoT’. Wireless communications and mobile computing 2020 (2020): 1–13. Web.
Kaissis, Georgios A. ?.?. ‘Secure, Privacy-Preserving and Federated Machine Learning in Medical Imaging’. Nature Machine Intelligence 2.6 (2020): 305–311. Web.
Wang, Qian ?.?. ‘Real-time and spatio-temporal crowd-sourced social network data publishing with differential privacy’. IEEE transactions on dependable and secure computing (2016): 1–1. Web.
Niu, Chaoyue ?.?. ‘Achieving data truthfulness and privacy preservation in data markets’. IEEE transactions on knowledge and data engineering 31.1 (2019): 105–119. Web.
Babu, S. Sathees, ??? K. Balasubadra. ‘Revamping Data Access Privacy Preservation Method against inside Attacks in Wireless Sensor Networks’. Cluster computing 22.S1 (2019): 65–75. Web.
Song, Haina ?.?. ‘Multiple sensitive values-oriented personalized privacy preservation based on randomized response’. IEEE transactions on information forensics and security 15 (2020): 2209–2224. Web.
Qiu, Guoying ?.?. ‘Mobile semantic-aware trajectory for personalized location privacy preservation’. IEEE internet of things journal 8.21 (2021): 16165–16180. Web.
Liu, Hong ?.?. ‘Cooperative privacy preservation for wearable devices in hybrid computing-based smart health’. IEEE internet of things journal 6.2 (2019): 1352–1362. Web.
Ni, Jianbing ?.?. ‘Enabling strong privacy preservation and accurate task allocation for mobile crowdsensing’. IEEE transactions on mobile computing 19.6 (2020): 1317–1331. Web.
Xu, Zhe, ??? A. Agung Julius. ‘Robust temporal logic inference for provably correct fault detection and privacy preservation of switched systems’. IEEE systems journal 13.3 (2019): 3010–3021. Web.
Shuai, Mengxia ?.?. ‘Lightweight and Privacy?preserving Authentication Scheme with the Resilience of Desynchronisation Attacks for WBANs’. IET information security 14.4 (2020): 380–390. Web.
Kamil, Ismaila A., ??? Sunday O. Ogundoyin. ‘On the Security of Privacy?preserving Authentication Scheme with Full Aggregation in Vehicular Ad Hoc Network’. Security and privacy 3.3 (2020): n. pag. Web.
Deebak, B. D., Fadi Al-Turjman, ??? Anand Nayyar. ‘Chaotic-Map Based Authenticated Security Framework with Privacy Preservation for Remote Point-of-Care’. Multimedia tools and applications 80.11 (2020): 1–26. Web.
Roy, Amit Kumar, ??? Ajoy Kumar Khan. ‘Privacy Preservation with RTT?based Detection for Wireless Mesh Networks’. IET information security 14.4 (2020): 391–400. Web.
Chavhan, Suresh ?.?. ‘Agent pseudonymous authentication-based conditional privacy preservation: An emergent intelligence technique’. IEEE systems journal 14.4 (2020): 5233–5244. Web.
Zhang, Lei, Meina Chen, ?.?. ‘A ?-Sensitive Indistinguishable Scheme for Privacy Preserving’. Cyber physical deployments 26.7 (2020): 5013–5033. Web.
Safia, Bourahla, ??? Challal Yacine. ‘Privacy preservation in social networks sequential publishing’. 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA). IEEE, 2018. Web.
Zhang, Zhikun, Heng Zhang, ?.?. ‘Bilateral privacy-preserving utility maximization protocol in database-driven cognitive radio networks’. IEEE transactions on dependable and secure computing 17.2 (2020): 236–247. Web.
Errapotu, Sai Mounika ?.?. ‘Bid privacy preservation in matching-based multiradio multichannel spectrum trading’. IEEE transactions on vehicular technology 67.9 (2018): 8336–8347. Web.
Xu, Qichao ?.?. ‘APIS: Privacy-preserving incentive for sensing task allocation in cloud and edge-cooperation mobile internet of things with SDN’. IEEE internet of things journal 7.7 (2020): 5892–5905. Web.
Du, Jun ?.?. ‘Distributed data privacy preservation in IoT applications’. IEEE wireless communications 25.6 (2018): 68–76. Web.
Wang, Xin ?.?. ‘Privacy preserving collaborative computing: Heterogeneous privacy guarantee and efficient incentive mechanism’. IEEE transactions on signal processing: a publication of the IEEE Signal Processing Society 67.1 (2019): 221–233. Web.
Hussain, Siam U., ??? Farinaz Koushanfar. ‘Privacy preserving localization for smart automotive systems’. Proceedings of the 53rd Annual Design Automation Conference. New York, NY, USA: ACM, 2016. Web.
Xu, Xiaolong ?.?. ‘A blockchain-powered crowdsourcing method with privacy preservation in mobile environment’. IEEE transactions on computational social systems 6.6 (2019): 1407–1419. Web.
Shi, Xiufang ?.?. ‘Resilient privacy-preserving distributed localization against dishonest nodes in internet of things’. IEEE internet of things journal 7.9 (2020): 9214–9223. Web.
Zhang, Zhikun, Shibo He, ?.?. ‘REAP: An efficient incentive mechanism for reconciling aggregation accuracy and individual privacy in crowdsensing’. IEEE transactions on information forensics and security 13.12 (2018): 2995–3007. Web.
Keshk, Marwa ?.?. ‘A privacy-preserving-framework-based blockchain and deep learning for protecting smart power networks’. IEEE transactions on industrial informatics 16.8 (2020): 5110–5118. Web.
Zhu, Saide ?.?. ‘Hybrid blockchain design for privacy preserving crowdsourcing platform’. 2019 IEEE International Conference on Blockchain (Blockchain). IEEE, 2019. Web.
Linoy, Shlomi ?.?. ‘Scalable Privacy-Preserving Query Processing over Ethereum Blockchain’. 2019 IEEE International Conference on Blockchain (Blockchain). IEEE, 2019. Web.
Yao, Lin ?.?. ‘Sensitive Attribute Privacy Preservation of Trajectory Data Publishing Based on L-Diversity’. Distributed and parallel databases 39.3 (2021): 785–811. Web.
Shabbir, Maryam ?.?. ‘Enhancing security of health information using modular encryption standard in mobile cloud computing’. IEEE access: practical innovations, open solutions 9 (2021): 8820–8834. Web.
Lu, Xiuqing, Zhenkuan Pan, ??? Hequn Xian. ‘An Efficient and Secure Data Sharing Scheme for Mobile Devices in Cloud Computing’. Journal of Cloud Computing Advances Systems and Applications 9.1 (2020): n. pag. Web.
Khan, Razaullah ?.?. ‘Privacy Preserving for Multiple Sensitive Attributes against Fingerprint Correlation Attack Satisfying c-Diversity’. Wireless communications and mobile computing 2020 (2020): 1–18. Web.
Song, Yujiao ?.?. ‘Efficient Attribute-Based Encryption with Privacy-Preserving Key Generation and Its Application in Industrial Cloud’. Security and communication networks 2019 (2019): 1–9. Web.
Zhang, Guanglin, Anqi Zhang, ?.?. ‘Lightweight privacy-preserving scheme in WI-fi fingerprint-based indoor localization’. IEEE systems journal 14.3 (2020): 4638–4647. Web.
Sun, Gang ?.?. ‘Toward incentivizing fog-based privacy-preserving mobile crowdsensing in the internet of vehicles’. IEEE internet of things journal 7.5 (2020): 4128–4142. Web.
Zhao, Chengcheng ?.?. ‘Privacy-preserving consensus-based energy management in smart grids’. IEEE transactions on signal processing: a publication of the IEEE Signal Processing Society 66.23 (2018): 6162–6176. Web.
Zhu, Tianqing ?.?. ‘More than privacy: Applying differential privacy in key areas of artificial intelligence’. IEEE transactions on knowledge and data engineering (2021): 1–1. Web.
Majeed, Abdul, Safiullah Khan, ??? Seong Oun Hwang. ‘Toward privacy preservation using clustering based anonymization: Recent advances and future research outlook’. IEEE access: practical innovations, open solutions 10 (2022): 53066–53097. Web.
Hassanpour, Ahmad ?.?. ‘Differential privacy preservation in robust continual learning’. IEEE access: practical innovations, open solutions 10 (2022): 24273–24287. Web.