Auto Deep Learning-based Automated Surveillance Technique to Recognize the Activities in the Cyber-Physical System
Main Article Content
Abstract
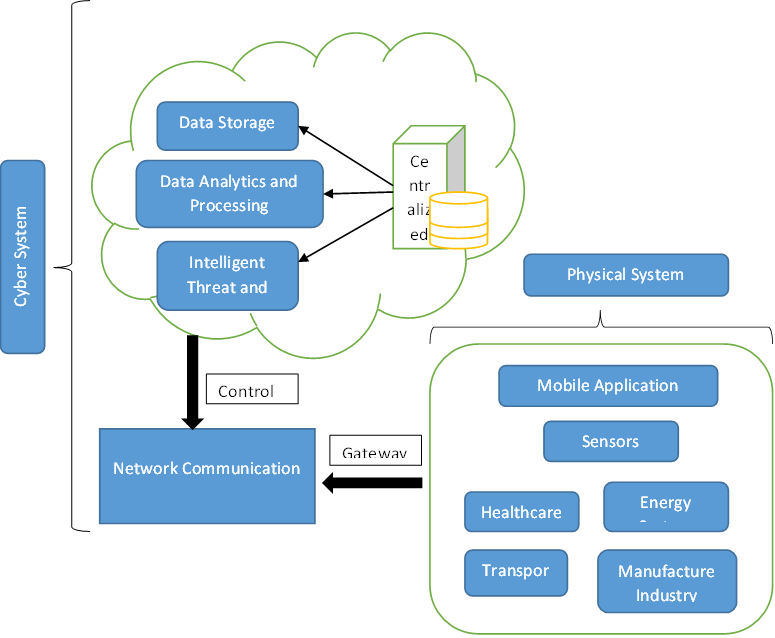
In recent days, the Internet of Things (IoT) plays a significant role and increasing in rapid usage in various applications. As IoT is being developed for cyber-physical systems in the specific domain of e-health care, military, etc. Based on real-time applications, security plays a vital role in certain activities in educational institutions. In the institutions, there are multiple videos are collected and stored in the data repositories. Those datasets are developed specifically for certain activities and no other datasets are developed for academic activities. As there is a large number of videos and images are collected and considered, advanced technologies like, deep learning and IoT are used to perform certain tasks. In this paper, a Auto Deep learning-based Automated Identification Framework (DLAIF) is proposed to consider and reconsider the activities based on image pre-processing, model can be trained through the proposed GMM model and then predication to make an effective surveillance process based on HMM. This proposed process makes to recognize the activities through EM and log Likelihood for cyber-physical systems. In the performance analysis, the proposed model efficiency can be determined through Accuracy detection, False Positive rate and F1 Score requirement. Then calculating the accuracy is more effective for the proposed model compared to other existing models such as BWMP and LATTE.
Article Details
References
H. M. Song, H. R. Kim and H. K. Kim, "Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network," in International Conference on Information Networking (ICOIN), 2016.
M. Marchetti and D. Stabili, "Anomaly detection of CAN bus messages through analysis of ID sequences," in IEEE Intelligent Vehicles Symposium (IV), 2017.
T. Hoppe, S. Kiltz, and J. Dittmann, "Security threats to automotive CAN networks—
Practical examples and selected short-term countermeasures," Reliability Engineering & System Safety, vol. 96, no. 11, pp. 11-25, 2011.
M. Gmiden, M. H. Gmiden and H. Trabelsi, "An intrusion detection method for securing in vehicle CAN bus," in International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), 2016.
H. Lee, S. H. Jeong and H. K. Kim, "OTIDS: A Novel Intrusion Detection System for Invehicle Network by Using Remote Frame," in Annual Conference on Privacy, Security and Trust (PST), 2017.
U. E. Larson, D. K. Nilsson and E. Jonsson, "An approach to specification-based attack detection for in-vehicle networks," in IEEE Intelligent Vehicles Symposium, 2008.
M. Aldwairi , A. M.Abu-Dalo and M. Jarrah, "Pattern matching of signature-based IDS using Myers algorithm under MapReduce framework," EURASIP Journal on Information Security, 2017.
E. W. Myers, "An O(ND) difference algorithm and its variations," Algorithmica, vol. 1, pp. 251-266, 1986.
T. Hoppe, S. Kiltz, and J. Dittmann, "Applying intrusion detection to automotive IT-early
insights and remaining challenges," Journal of Information Assurance and Security (JIAS), pp. 226-235, 2009.
D. Stabili, M. Marchetti and M. Colajanni, "Detecting attacks to internal vehicle networks through Hamming distance," in AEIT International Annual Conference, 2017.
K. T. Cho and K. G. Shin, "Viden: Attacker identification on in-vehicle networks," in ACM SIGSAC Conference on Computer and Communications Security, 2017.
K. T. Cho and K. G. Shin, "Fingerprinting Electronic Control Units for Vehicle Intrusion Detection," in 25th USENIX Security Symposium, 2016.
X. Ying, S. U. Sagong, A. Clark, L. Bushnell and R. Poovendran, "Shape of the Cloak: Formal Analysis of Clock Skew-Based Intrusion Detection System in Controller Area Networks," IEEE Transactions on Information Forensics and Security, vol. 14, pp. 2300- 2314, 2019.
M. Yoon, S. Mohan, J. Choi and L. Sha, "Memory Heat Map: Anomaly detection in realtime embedded systems using memory behavior," in IEEE Design Automation Conference, (DAC), 2015.
M. Müter and N. Asaj, "Entropy-based anomaly detection for in-vehicle networks," in IEEE Intelligent Vehicles Symposium (IV), 2011.
W. Wu, Y. Huang, R. Kurachi, G. Zeng, G. Xie, R. Li, and K. Li, "Sliding window optimized information entropy analysis method for intrusion detection on in-vehicle networks," IEEE Access, vol. 6, pp. 45233-45245, 2018.
M. Müter, A. Groll and F. C. Freiling, "A structured approach to anomaly detection for invehicle networks," in International Conference on Information Assurance and Security, 2010.
A. Taylor, N. Japkowicz and S. Leblanc, "Frequency-based anomaly detection for the automotive CAN bus," in World Congress on Industrial Control Systems Security (WCICSS), 2015.
F. Martinelli, F. Mercaldo, V. Nardone and A. Santone, "Car hacking identification through fuzzy logic algorithms," in IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), 2017.
T. P. Vuong, G. Loukas and D. Gan, "Performance Evaluation of Cyber-Physical Intrusion Detection on a Robotic Vehicle," in IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, 2015.
M. Levi, Y. Allouche and A. Kontorovich, "Advanced analytics for connected cars cyber security," in IEEE Vehicular Technology Conference (VTC Spring), 2017.
M. Kang and J. Kang, "A novel intrusion detection method using deep neural network for in-vehicle network security," in IEEE 83rd Vehicular Technology Conference (VTC Spring), 2016.
S. F. Lokman, A. T. Othman, S. Musa, and M. H. Abu Bakar, "Deep contractive autoencoder-based anomaly detection for in-vehicle controller area network (CAN)," Progress in Engineering Technology. Advanced Structured Materials, vol. 119, 2019.
M. Hanselmann, T. Strauss, K. Dormann and H. Ulmer, "CANet: An Unsupervised Intrusion Detection System for High Dimensional CAN Bus Data," IEEE Access, vol. 8, pp. 58194-58205, 2020.
G. Loukas, T. Vuong, R. Heartfield, G. Sakellari, Y. Yoon and D. Gan, "Cloud-Based Cyber-Physical Intrusion Detection for Vehicles Using Deep Learning," IEEE Access, vol. 6, pp. 3491-3508, 2018.
A. Taylor, S. Leblanc and N. Japkowicz, "Anomaly detection in automobile control network data with long short-term memory networks," in IEEE International Conference on Data Science and Advanced Analytics (DSAA), 2016.
M. D. Hossain, H. Inoue, H. Ochiai, D. Fall and Y. Kadobayashi, "LSTM-based intrusion detection system for in-vehicle can bus communications," IEEE Access, vol. 8, pp. 185489-185502, 2020.
V. K. Kukkala, S. V. Thiruloga and S. Pasricha, "INDRA: Intrusion Detection using Recurrent Autoencoders in Automotive Embedded Systems," IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems (TCAD), vol. 39, 2020.
M. O. Ezeme, Q. H. Mahmoud and A. Azim, "Hierarchical Attention-Based Anomaly Detection Model for Embedded Operating Systems," in IEEE International Conference on Embedded and Real-Time Computing Systems and Applications (RTCSA), 2018.
M. Weber, G. Wolf, B. Zimmer, and E. Sax., "Online Detection of Anomalies in Vehicle Signals using Replicator Neural Networks," in ESCAR USA, 2018.
M. Weber, S. Klug, B. Zimmer, and E. Sax, "Embedded Hybrid Anomaly Detection for Automotive CAN Communication," in European Congress on Embedded Real Time Software and Systems(ERTS),2018.
Bandi, R., Ananthula, V.R. & Janakiraman, S. Self Adapting Differential Search Strategies Improved Artificial Bee Colony Algorithm-Based Cluster Head Selection Scheme for WSNs. Wireless Pers Commun 121, 2251–2272 (2021). https://doi.org/10.1007/s11277-021-08821-5