Study And Modeling of Question Answer System Using Deep Learning Technique of AI
Main Article Content
Abstract
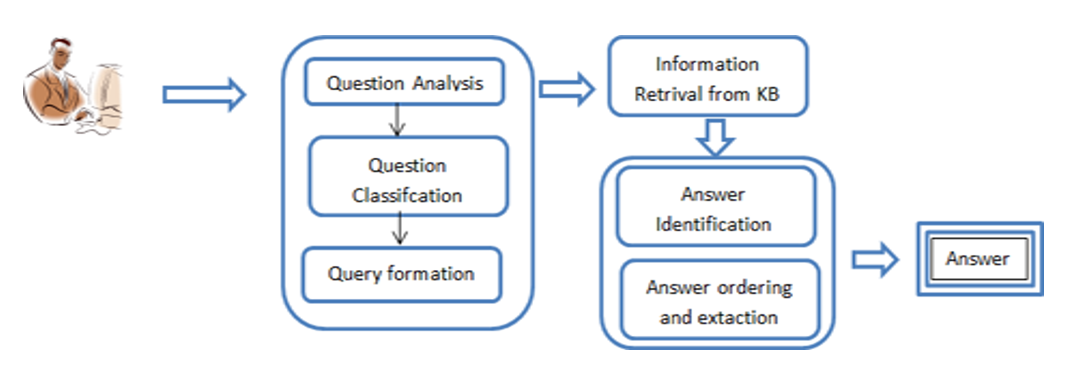
In this paper, the different QA system types, the theoretical foundation for deep learning models, the metaheuristic optimization techniques, and the performance assessment metrics are discussed. A suggested architecture for a question-and-answer system that takes a deep learning approach is shown here. The study also covers the constraints and factors to take into account regarding the aforementioned system.
Article Details
References
Otmane El Mouaatamid, Mohammed L, Mostafa B, 2016, “Internet of Things Security: Layered Classification of Attacks and Possible Countermeasures,” Electronic Journal of Information Technology, Vol. 9.
M.U. Farooq, Muhammad W, SadiaM, 2015, “A Review on Internet of Things (IoT),” International Journal of Computer Applications, Vol. 113, No. 1, pp. 1-7.
Riccardo B, Nicola B, Vishwas L, Alexis O, Alexandru, and Michele Rossi, 2012, “Secure communication for smart IoT objects: Protocol stacks, use cases and practical examples,” IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Digital Proceedings, pp. 1-7.
T. Dierks and E. Rescorla., 2008, “The Transport Layer Security (TLS) Protocol Version 1.2. RFC 5246 (Proposed Standard),” Updated by RFCs 5746, 5878, 6176.
Gunter S, 2003, “Security in Fixed and Wireless Networks - An Introduction to Securing Data Communications,” Wiley.
Joerg D, Alexander W, and Panayotis K, 2015, “A View on Privacy & Trust in IoT,” IEEE International Conference on Communications, London.
Jennifer G. Steiner, B. Clifford Neuman, and Jeffrey I. Schiller, 1988, “Kerberos: An authentication service for open network systems,” In Proceedings of the USENIX Winter Conference. Dallas, Texas, USA, USENIX Association, pp.191-202.
E. Vasilomanolakis, J. Daubert, M. Luthra, V. Gazis, A. Wiesmaier and P. Kikiras, 2015, “On the Security and Privacy of Internet of Things Architectures and Systems,” International Workshop on Secure Internet of Things (SIoT), pp. 49-57.
Ahmad W Atamli and Andrew M, 2014, “Threat- Based Security Analysis for the Internet Things,” In Secure Internet of Things, pp. 35–43.
Rolf H. Weber, 2010, “Internet of Things – New Security and Privacy Challenges,” Computer Law & Security Review, Vol. 26, No. 1, pp. 23–30. 136
Cisco: The Internet of Things Reference Model. 2014. http://cdn.iotwf .com/resources /71/IoT Reference Model White Paper June4 2014.pdf.
Conoscenti M, Vetro A, De Martin JC., 2016,“Blockchain for the Internet of Things: a systematic literature review,” IEEE/ACS13th international conference of computer systems and applications(AICCSA), pp. 1–6.
Chahid Y, Benabdellah M, Azizi A, 2017,“Internet of things security,” International conference on wireless technologies, embedded and intelligent systems (WITS), pp. 1–6.
K. Chen.,2018, “Internet-of-Things Security and Vulnerabilities: Taxonomy, Challenges, and Practice,” Journal of Hardware and Systems Security, Vol 2, pp. 97–110.
H. Z. Yuchen Yang, Longfei Wu, Guisheng Yin, and Lijie Li, 2017 “A Survey on Security and Privacy Issues in Internet-of-Things,” IEEE Internet of Things Journal, Vol. 4, No. 5, pp. 1250-1258.
Shinzaki.T, Morikawa.I, Yamaoka.Y, and Sakemi.Y, 2016,“IoT security for utilization of big data: Mutual authentication technology and anonymization technology for positional data,” Fujitsu Sci. Tech. J., Vol. 52, No. 4, pp. 52–60.
Ferrag.M.A, Maglaras.L.A, Janicke.H, and Jiang.J, 2017, “Authentication Protocols for Internet of Things: A Comprehensive Survey,” Security and Communication Networks, Vol. 17, pp.1- 41.
X. Li, J. Peng, J. Niu, F. Wu, J. Liao and K. R. Choo, 2018,"A Robust and Energy Efficient Authentication Protocol for Industrial Internet of Things," IEEE Internet of Things Journal, Vol. 5, No. 3, pp. 1606-1615.
Srinivas.J, Mukhopadhyay.S, and Mishra.D, 2017, “Ad Hoc Networks Secure and efficient user authentication scheme for multi -gateway wireless sensor networks,” Ad Hoc Networks, Vol. 54, pp. 147–169.