Intelligent Trust based Security Framework for Internet of Things
Main Article Content
Abstract
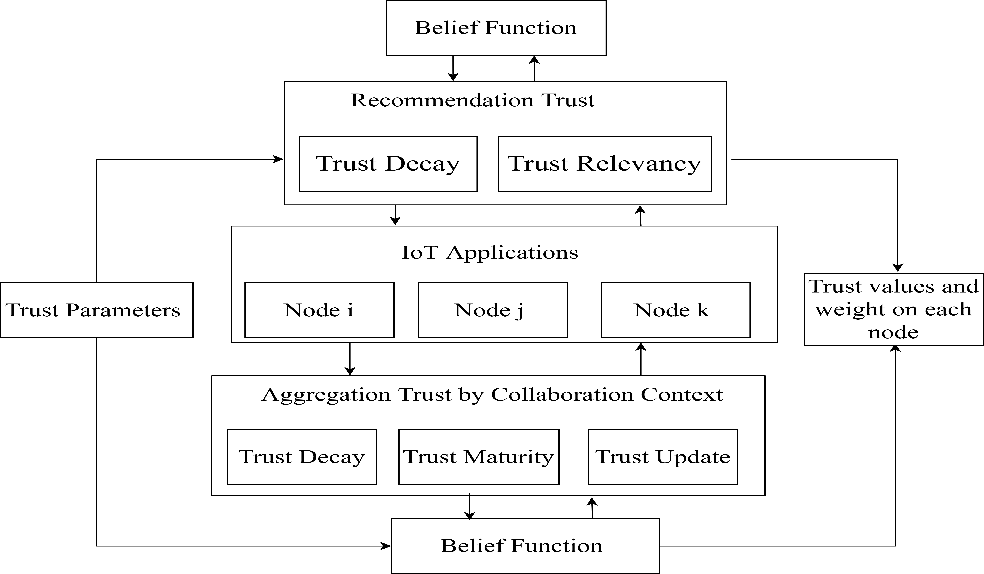
Trust models have recently been proposed for Internet of Things (IoT) applications as a significant system of protection against external threats. This approach to IoT risk management is viable, trustworthy, and secure. At present, the trust security mechanism for immersion applications has not been specified for IoT systems. Several unfamiliar participants or machines share their resources through distributed systems to carry out a job or provide a service. One can have access to tools, network routes, connections, power processing, and storage space. This puts users of the IoT at much greater risk of, for example, anonymity, data leakage, and other safety violations. Trust measurement for new nodes has become crucial for unknown peer threats to be mitigated. Trust must be evaluated in the application sense using acceptable metrics based on the functional properties of nodes. The multifaceted confidence parameterization cannot be clarified explicitly by current stable models. In most current models, loss of confidence is inadequately modeled. Esteem ratings are frequently mis-weighted when previous confidence is taken into account, increasing the impact of harmful recommendations.
In this manuscript, a systematic method called Relationship History along with cumulative trust value (Distributed confidence management scheme model) has been proposed to evaluate interactive peers trust worthiness in a specific context. It includes estimating confidence decline, gathering & weighing trust parameters and calculating the cumulative trust value between nodes. Trust standards can rely on practical contextual resources, determining if a service provider is trustworthy or not and does it deliver effective service? The simulation results suggest that the proposed model outperforms other similar models in terms of security, routing and efficiency and further assesses its performance based on derived utility and trust precision, convergence, and longevity.
Article Details
References
Adewuyi, A. A., Cheng, H., Shi, Q., Cao, J., MacDermott, Á., & Wang, X. (2019). CTRUST: A dynamic trust model for collaborative applications in the Internet of Things. IEEE Internet of Things Journal, 6(3), 5432-5445.
Adewuyi, A. A., Cheng, H., Shi, Q., Cao, J., Wang, X., & Zhou, B. (2021). Sc-trust: a dynamic model for trustworthy service composition in the internet of things. IEEE Internet of Things Journal, 9(5), 3298-3312.
Ahmed, E., Yaqoob, I., Gani, A., Imran, M., & Guizani, M. (2016). Internet-of-things-based smart environments: state of the art, taxonomy, and open research challenges. IEEE Wireless Communications, 23(5), 10-16.
Alenezi, A., Atlam, H., Alsagri, R., Alassafi, M., & Wills, G. (2019). IoT forensics: A state-of-the-art review, callenges and future directions.
Arulanantham, D., & Palanisamy, C. (2021). Trusted cognitive sensor based dual routing network on Internet of things. International Journal of Communication Systems, 34(10), e4836.
Asiri, S., & Miri, A. (2016, December). An IoT trust and reputation model based on recommender systems. In 2016 14th Annual Conference on Privacy, Security and Trust (PST) (pp. 561-568). IEEE.
Awad, S., Malki, A., & Malki, M. (2021). Composing WoT services with uncertain and correlated data. Computing, 103(7), 1501-1517.
Bao, F., & Chen, I. R. (2012, September). Dynamic trust management for internet of things applications. In Proceedings of the 2012 international workshop on Self-aware internet of things (pp. 1-6).
Beg, S., Anjum, A., Ahmad, M., Hussain, S., Ahmad, G., Khan, S., & Choo, K. K. R. (2021). A privacy-preserving protocol for continuous and dynamic data collection in IoT enabled mobile app recommendation system (MARS). Journal of Network and Computer Applications, 174, 102874.
Chen, D., Chang, G., Sun, D., Li, J., Jia, J., & Wang, X. (2011). TRM-IoT: A trust management model based on fuzzy reputation for internet of things. Computer Science and Information Systems, 8(4), 1207-1228.
Chen, G., Zeng, F., Zhang, J., Lu, T., Shen, J., & Shu, W. (2021). An adaptive trust model based on recommendation filtering algorithm for the Internet of Things systems. Computer Networks, 190, 107952.
Chinnaswamy, S., & Annapurani, K. (2021). Trust aggregation authentication protocol using machine learning for IoT wireless sensor networks. Computers & Electrical Engineering, 91, 107130.
Choudhury, S. S., Mohanty, S. N., & Jagadev, A. K. (2021). Multimodal trust based recommender system with machine learning approaches for movie recommendation. International Journal of Information Technology, 13(2), 475-482.
Díaz, M., Martín, C., & Rubio, B. (2016). State-of-the-art, challenges, and open issues in the integration of Internet of things and cloud computing. Journal of Network and Computer applications, 67, 99-117.
Duan, R., Chen, X., Xing, T.: Aqos architecture for iot. In: 2011International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, pp.717–720. IEEE (2011).
Ganeriwal, S., & Srivastava, M. B. (2004). Reputation-based model for High Integrity Sensor Networks. proceedings of SASN04.
Gessner, D., Olivereau, A., Segura, A. S., & Serbanati, A. (2012, June). Trustworthy infrastructure services for a secure and privacy-respecting internet of things. In 2012 IEEE 11th international conference on trust, security and privacy in computing and communications (pp. 998-1003). IEEE.
Govindan, K., & Mohapatra, P. (2011). Trust computations and trust dynamics in mobile adhoc networks: A survey. IEEE Communications Surveys & Tutorials, 14(2), 279-298.
Guo, J., Liu, A., Ota, K., Dong, M., Deng, X., & Xiong, N. N. (2021). ITCN: an intelligent trust collaboration network system in IoT. IEEE transactions on network science and engineering, 9(1), 203-218.
Han, G., Jiang, J., Shu, L., Niu, J., & Chao, H. C. (2014). Management and applications of trust in Wireless Sensor Networks: A survey. Journal of Computer and System Sciences, 80(3), 602-617.
Khan, S., Zafar, S., Iftekhar, N., Biswas, S., & Tripathi, G. (2021, March). Inculcating Dynamic Trust Management across Internet through avant-garde Approach. In Proceedings of the 2nd International Conference on ICT for Digital, Smart, and Sustainable Development, ICIDSSD 2020, 27-28 February 2020, Jamia Hamdard, New Delhi, India.
Kalnoor, G., & Gowrishankar, S. (2022). A model for intrusion detection system using hidden Markov and variational Bayesian model for IoT based wireless sensor network. International Journal of Information Technology, 14(4), 2021-2033.
Kenchannavar, H. H., Pujar, P. M., Kulkarni, R. M., & Kulkarni, U. P. (2021). Evaluation and Analysis of Goodness of Fit for Water Quality Parameters using Linear Regression through the Internet of Things (IoT) based Water Quality Monitoring System. IEEE Internet of Things Journal.
Kil, H., & Nam, W. (2021). Automatic incremental recomposition algorithm for QoS-aware internet of things service composition. International Journal of Web and Grid Services, 17(2), 118-137.
Kotis, K., Athanasakis, I., & Vouros, G. A. (2018). Semantically enabling IoT trust to ensure and secure deployment of IoT entities. International Journal of Internet of Things and Cyber-Assurance, 1(1), 3-21.
Lin, Z., & Dong, L. (2017). Clarifying trust in social internet of things. IEEE Transactions on Knowledge and Data Engineering, 30(2), 234-248.
Malchi, S. K., Kallam, S., Al-Turjman, F., & Patan, R. (2021). A trust-based fuzzy neural network for smart data fusion in internet of things. Computers & Electrical Engineering, 89, 106901.
Mon, S., Winster, S. G., & Ramesh, R. (2021). Trust Model for IoT Using Cluster Analysis: A Centralized Approach. Wireless Personal Communications, 1-22.
Musen, M. A. (2015). The protégé project: a look back and a look forward. AI matters, 1(4), 4-12.
Patel, M., Bhattacharyya, S., & Alfageeh, A. (2019, October). Formal Trust Architecture For Assuring Trusted Interactions In the Internet of Things. In 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON) (pp. 0033-0039). IEEE.
Riahi, A., Challal, Y., Natalizio, E., Chtourou, Z., & Bouabdallah, A. (2013, May). A systemic approach for IoT security. In 2013 IEEE international conference on distributed computing in sensor systems (pp. 351-355). IEEE.
Ruan, Y., Durresi, A., Alfantoukh, L.: Trust management framework for internet of thing. In: 2016 IEEE 30th International Conference on Advanced Information Net-working and Applications (AINA), pp.1013–1019. IEEE(2016)
Sharma, D. K., Bhardwaj, K. K., Banyal, S., Gupta, R., Gupta, N., & Nkenyereye, L. (2021). An Opportunistic Approach for Cloud Service-Based IoT Routing Framework Administering Data, Transaction, and Identity Security. IEEE Internet of Things Journal, 9(4), 2505-2512.
Soleymani, M., Abapour, N., Taghizadeh, E., Siadat, S., & Karkehabadi, R. (2021). Fuzzy Rule-Based Trust Management Model for the Security of Cloud Computing. Mathematical Problems in Engineering, 2021.
Swathi, S. (2021). Trust Aware Data Aggregation mechanism for malicious node identification in WSN based IoT Environment. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(13), 2217-2224.
Tahta, U. E., Sen, S., & Can, A. B. (2015). GenTrust: A genetic trust management model for peer-to-peer systems. Applied Soft Computing, 34, 693-704.
Theodorakopoulos, G., & Baras, J. S. (2006). On trust models and trust evaluation metrics for ad hoc networks. IEEE Journal on selected areas in Communications, 24(2), 318-328.
Wang, Y., Yang, G., Li, T., Li, F., Tian, Y., & Yu, X. (2020). Belief and fairness: a secure two-party protocol toward the view of entropy for IoT devices. Journal of Network and Computer Applications, 161, 102641.
Weinstein, R. (2005). RFID: a technical overview and its application to the enterprise. IT professional, 7(3), 27-33.
Yi, S. K. M., Steyvers, M., Lee, M. D., & Dry, M. J. (2012). The wisdom of the crowd in combinatorial problems. Cognitive science, 36(3), 452-470.