Development of Mobile Application that Detects Phishing Messages to Decrease the Percentage of Data Theft during the COVID-19 Pandemic
Main Article Content
Abstract
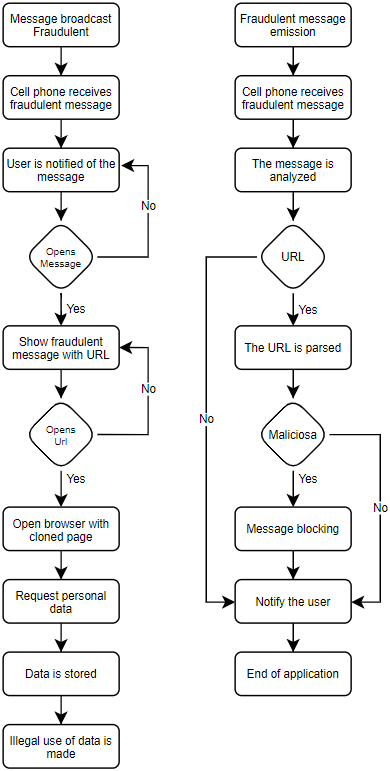
The COVID-19 pandemic has established not only a health emergency, but has generated an emergency in the control of personal data of all those people who make use of technological means, which increased the activity of phishing which consists of the theft of personal data through the circulation of false information through the different social networks, in addition, the circulation with messages related to the cure of this disease only for the theft of data. This research develops a mobile application that detects malicious URLs found within the content of textmessages. The developed application performs an analysis of the URLs according to the database that is updated with each attack detected, performing a blocking of the content and notifies the user of the actions that canbetaken, with this the theft of the personal data of the users is avoided. This application is very useful for all those people who use mobile equipment (mobile) and have no knowledge of these types of attacks, since they are likely to perform the actions that the perpetrators foresee for the obtaining of their personal data, so this application provides a means of security against these types of phishing attacks.
Article Details
References
I. Saha, D. Sarma, R. J. Chakma, M. N. Alam, A. Sultana, and S. Hossain, "Phishing attacks detection using deep learning approach," Proc. 3rd Int. Conf. Smart Syst. Inven. Technol. ICSSIT 2020, no. Icssit, pp. 1180–1185, 2020, doi: 10.1109/ICSSIT48917.2020.9214132.
F. Almeida, J. Duarte Santos, and J. Augusto Monteiro, "The Challenges and Opportunities in the Digitalization of Companies in a Post-COVID-19 World," IEEE Eng. Manag. Rev. , vol. 48, no. 3, pp. 97–103, 2020, doi: 10.1109/EMR.2020.3013206.
A. Gupta, P. Prabhat, R. Gupta, S. Pangotra, and S. Bajaj, "Message authentication system for mobile messaging applications," Proc. - 2017 Int. Conf. Next Gener. Comput. Inf. Syst. ICNGCIS 2017, pp. 126–130, 2018, doi: 10.1109/ICNGCIS.2017.32.
J. Tidy, "Coronavirus: how hackers are using the fear of covid-19 disease to spread computer viruses - BBC News World." .
Oshin Dhiman, & Dr. Anand Sharma. (2022). Incorporation of Booster in Carbon Interconnects for High-Speed Integrated Circuits. Acta Energetica, (03), 22–28. Retrieved from http://actaenergetica.org/index.php/journal/article/view/473
J. W. Joo, S. Y. Moon, S. Singh, and J. H. Park, "S-Detector: an enhanced security model for detecting Smishing attack for mobile computing," Telecommun. Syst. , vol. 66, no. 1, pp. 29–38, 2017, doi: 10.1007/s11235-016-0269-9.
N. E.C. PERU, "Cybercriminal reveals how he steals money from credit cards in Mexico | world | EL COMERCIO PERÚ."
D. El Comercio, "Cybercriminal reveals how he steals money from credit cards in Mexico | world | EL COMERCIO PERÚ." .
B. V. Deemer, By Pete, Gabrielle Benefield, Craig Larman, "The Scrum Primer," Scrum Train. Inst. , vol. 1.1, pp. 1–20, 2009.
P. Chilito, D. Viveros, C. Pardo, and F. J. Pino, "Scrum+: An agile guide for the global software development (GSD) multi-model project management," 2018 IEEE Colomb. Conf. Commun. Comput. COLCOM 2018 - Proc. , pp. 0–5, 2018, doi: 10.1109/ColComCon.2018.8466710.
Tadeusz Chmielniak, & Nadica Stojanovic. (2022). Design of Computer Aided Design in the Field of Mechanical Engineering . Acta Energetica, (01), 08–16. Retrieved from http://actaenergetica.org/index.php/journal/article/view/460
G. Ongo and G. P. Kusuma, "Hybrid Database System of MySQL and MongoDB in Web Application Development," Proc. 2018 Int. Conf. Inf. Manag. Technol. ICIMTech 2018, no. September, pp. 256–260, 2018, doi: 10.1109/ICIMTech.2018.8528120.
A. Mundra, S. Misra, and C. A. Dhawale, "Practical scrum-scrum team: Way to produce successful and quality software," Proc. 2013 13th Int. Conf. Comput. Sci. Its Appl. ICCSA 2013, pp. 119–123, 2013, doi: 10.1109/ICCSA.2013.25.
S. Nakazawa, K. Komatsu, T. Tanaka, and K. Matsumoto, "Development and Evaluation of Large-Screen Digital Kanban with Smartphone Operation," Proc. - 2017 6th IIAI Int. Congr. Adv. Appl. Informatics, IIAI-AAI 2017, pp. 295–300, 2017, doi: 10.1109/IIAI-AAI.2017.151.