Web Social Media Privacy Preferences and Perception
Main Article Content
Abstract
The proliferation of social media websites has led to concerns over privacy breaches, as these sites have access to users' sensitive and personal data. This study sought to investigate users' perceptions and concerns for social media websites, with the aim of developing a system that meets their requirements. To achieve this, a questionnaire was designed for privacy permissions on eight popular social media websites, and 425 completed answers were analyzed. The results revealed that users' concerns were diverse and differed across different social media platforms. Gender, age, education level, and IT proficiency were found to be weakly correlated with privacy concerns. Women expressed greater concerns than men, particularly for Twitter and Snapchat, while older users expressed greater levels of concern for Snapchat and Instagram. As education levels increased, users tended to express greater levels of concern, especially on WhatsApp and Snapchat.
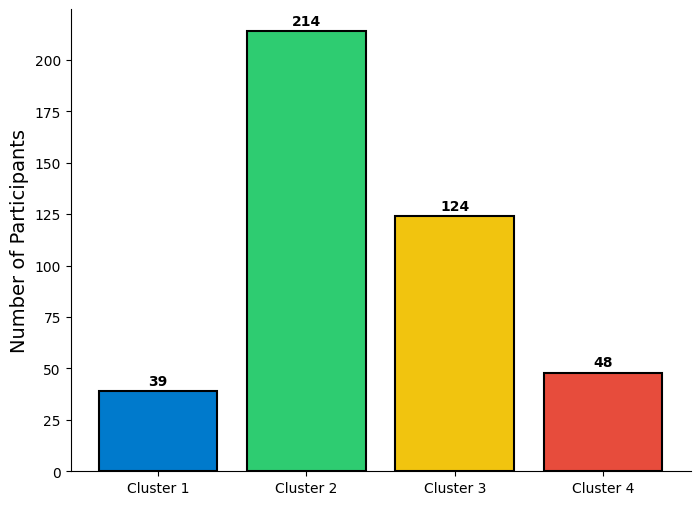
Furthermore, this study identified four hierarchical clusters of users based on their preferences and concerns regarding permission privacy for social media websites. The results revealed that the majority of participants (214 users) were highly concerned about privacy on social media, indicating that they were aware of the potential risks associated with sharing personal information online which represents the third cluster. The first and fourth clusters were the most unconcerned groups regarding permission privacy, consisting of a small number of users. The second cluster, comprising 124 participants, had an average score of 1.6, indicating that they were the second most concerned about privacy. Overall, the findings of this study could be useful for social media platforms in developing privacy policies and settings that align with users' concerns and preferences.
Article Details
References
J. R. Mayer and J. C. Mitchell, “Third-Party Web Tracking: Policy and Technology,” in 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA: IEEE, May 2012, pp. 413–427. doi: 10.1109/SP.2012.47.
“Web Design and Applications - W3C.” https://www.w3.org/standards/webdesign/ (accessed Dec 30, 2022).
Agarwal, S., & Hall, C. M. (2012). A framework for understanding the impact of social media on tourism. Tourism Management, 33(1), 162-170.
Song, Y., & Hengartner, U. (2015, October). PrivacyGuard: A VPN-based platform to detect side channel attacks on smartphones. In Proceedings of the 2015 ACM SIGSAC Conference on Computer and Communications Security (pp. 144-155). ACM.
“P3P and Privacy FAQ.” https://www.w3.org/P3P/p3pfaq.html (accessed Feb 15, 2023).
P. K. Masur and M. Scharkow, “Disclosure Management on Social Network Sites: Individual Privacy Perceptions and User-Directed Privacy Strategies,” Social Media + Society, vol. January-March 2016, pp. 1–13, Feb. 2016, doi: 10.1177/2056305116634368.
D. F. Somé, N. Bielova, and T. Rezk, “Control What You Include!: Server-Side Protection Against Third Party Web Tracking,” E. Bodden, M. Payer, and E. Athanasopoulos, Eds., in Lecture Notes in Computer Science, vol. 10379. Cham: Springer International Publishing, 2017, pp. 115–132. doi: 10.1007/978-3-319-62105-0_8.
R. Dingledine, N. Mathewson, and P. Syverson, “Tor: The {Second-Generation} Onion Router,” presented at the 13th USENIX Security Symposium (USENIX Security 04), 2004. Accessed: May 15, 2023. [Online]. Available: https://www.usenix.org/conference/13th-usenix-security-symposium/tor-second-generation-onion-router
V. Toubiana, A. Narayanan, D. Boneh, H. Nissenbaum, and S. Barocas, “Adnostic: Privacy Preserving Targeted Advertising”.
O. Salim and T. Al-Rousan, “Securing the Web Browser Local Data Storage,” vol. 9, pp. 75–82, Feb. 2021, doi: 10.30534/ijeter/2021/11922021.
R. Putthacharoen and P. Bunyatnoparat, “Protecting cookies from Cross Site Script attacks using Dynamic Cookies Rewriting technique,” Jan. 2011.
Sunil Kumar, M. ., Kumarasamy, M. ., Madhavi, N. B. ., Dhariwal, S. ., Sampath Kumar, R. ., & Oyebode, O. J. . (2023). Reinforcement Based Concrete Modelling in Commercial Buildings Using Machine Learning Simulations. International Journal of Intelligent Systems and Applications in Engineering, 11(4s), 118–126. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2578
A. Cahn, S. Alfeld, P. Barford, and S. Muthukrishnan, “An Empirical Study of Web Cookies,” in Proceedings of the 25th International Conference on World Wide Web, Montréal Québec Canada: International World Wide Web Conferences Steering Committee, Apr. 2016, pp. 891–901. doi: 10.1145/2872427.2882991.
Ms. Mayuri Ingole. (2015). Modified Low Power Binary to Excess Code Converter. International Journal of New Practices in Management and Engineering, 4(03), 06 - 10. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/38
C. Moiso and R. Minerva, “Towards a user-centric personal data ecosystem The role of the bank of individuals’ data,” presented at the 2012 16th International Conference on Intelligence in Next Generation Networks, ICIN 2012, Oct. 2012, pp. 202–209. doi: 10.1109/ICIN.2012.6376027.
Wisniewski, A., Cranor, L. F., Sadeh, N., & Sadeghi, A. (2017). A survey of parental control apps for mobile devices. ACM Transactions on Privacy and Security (TOPS), 20(4), 1-35.
Ghazaly, N. M. . (2020). Secure Internet of Things Environment Based Blockchain Analysis. Research Journal of Computer Systems and Engineering, 1(2), 26:30. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/8
Pew Research Center. (2019, January 14). Americans' opinions on privacy and information sharing. Retrieved from https://www.pewresearch.org/internet/2019/11/15/how-americans-think-about-privacy-and-the-vulnerability-of-their-personal-data
Rowan, Mark, and Josh Dehlinger. "Observed gender differences in privacy concerns and behaviors of mobile device end users." Procedia Computer Science 37 (2014): 340-347.